What is Cloud Security Posture Management?
Today, more organizations than ever before rely on the cloud for business-critical services. Cloud-based file sharing, video conferencing, and messaging applications help employees collaborate across in-office and remote environments, while cloud platforms enable developers to ship and deliver software at speed and scale.. However, relying on cloud-based services and infrastructure increases the complexity of your organization’s IT environment—as well as its attack surface. As many as 99 percent of cloud security failures are the result of misconfigurations, a statistic fueled largely by the complexity of configuring cloud environments and the rapid speed of code deployments in DevOps cultures.1 Using appropriate monitoring tools and strategies is vital for identifying and responding to risks within highly dynamic cloud resources.
Cloud Security Posture Management (CSPM) is a category of modern security solutions that monitor your organization’s cloud infrastructure for misconfigurations and compliance risks. CSPM continuously scans your cloud-based resources—including user roles and privileges, access keys or tokens, infrastructure components such as containers and hosts, and more—for known vulnerable configurations that could present a security risk. It also monitors your environment for configurations that violate certain industry standards and benchmarks, such as the Health Insurance Portability and Accountability Act (HIPAA) or Service Organization Control Type 2 (SOC 2).
As a CSPM tool scans your cloud environment for these issues, it reports on their security status in real time, identifying misconfigurations and tagging owners and associated services so that the appropriate teams can take remediating action.
By providing ongoing insight into the security posture of your varied cloud resources, CSPM helps your compliance, engineering, legal, and security teams:
- Assess and track the security posture of your organization’s cloud assets and accounts
- Receive and respond to alerts on key security issues that require immediate action
- Adhere to industry compliance standards and best practices
How does CSPM work?
CSPM solutions continuously scan the resources that make up your cloud environment, checking them against predetermined rules that flag configurations that are known to be vulnerable or that violate important industry standards, including CIS Benchmarks for Amazon Web Services (AWS), the Payment Card Industry Data Security Standard (PCI DSS), HIPAA, the General Data Protection Regulation (GDPR), and SOC 2.
If CSPM detects a misconfiguration or a compliance violation, it will flag the issue for you and record the following information:
- The state of the misconfigured asset
- The configuration rule that was broken
- The relative severity of the failure
DevOps, security, and other teams within your organization can review these reports to determine next steps, as well as create alerts on specific issues so they’ll be notified immediately for the highest-severity findings.
What are the benefits of CSPM?
Large cloud environments can be made up of hundreds or thousands of different resources, each of which presents possible vulnerabilities to attackers if it is not configured properly. Additionally, cloud environments are inherently dynamic, with resources constantly being created and destroyed based on need or usage. As another challenge, industry compliance frameworks require that cloud assets maintain specific conditions and configurations at all times.CSPM solutions help organizations continuously monitor their complex cloud infrastructures for risks that could otherwise be difficult to surface. By providing ongoing measurement and monitoring of your cloud environment’s security posture, CSPM helps your teams detect misconfigurations that can lead to intrusions and identify potential paths of attack.
Traditionally, CSPM solutions have been viewed primarily as tools to help security teams identify and remediate cloud misconfigurations. But as cloud environments become more complex, development and operations teams can deploy CSPM as they manage and monitor infrastructure and other cloud resources in a holistic DevSecOps model.
Consider using CSPM for these benefits:
- Security management
Teams can use CSPM to evaluate their organization’s overall security posture as well as identify specific risks. CSPM can pinpoint misconfigurations and trace these issues to individual servers, containers, accounts, and other resources to help teams root-cause and remediate risks.
- Infrastructure optimization
Teams can use CSPM to observe and report on all components of their organization’s cloud infrastructure. Resource mapping can locate potential chokepoints, identify underutilized or unused resources, and pinpoint inactive user roles.
- Completion of audits and fulfillment of customer agreements
CSPM’s reporting capabilities can help verify license usage and service-level agreements (SLAs), establish customer trust, meet compliance requirements in audits, and satisfy vendor questionnaires.
What industry challenges can CSPM address?
As organizations increasingly rely upon cloud-based services and applications, CSPM solutions can help address several industry-wide security risks and compliance challenges, including:
- Data breaches:
Scanning for misconfigurations in your cloud environment can help prevent the unauthorized access, use, or disclosure of sensitive data stored in the cloud by identifying and remediating potential access points for attackers.
- Account hijacking:
CSPM scans for misconfigured identity and access management (IAM) resources that attackers could use to gain unauthorized access to cloud accounts.
- Maintain compliance:
A CSPM solution can help teams conduct regular audits and assessments to ensure that your infrastructure’s security controls are effective and that you are meeting compliance requirements.
Before implementing a CSPM solution, planning is key. Inventory the components that comprise your current cloud infrastructure, such as hosts, containers, and IAM resources. Map out your organization’s infrastructure so you have a visual reference to ensure your CSPM solution covers all bases.
What are the best approaches when using a CSPM solution?
As the technologies deployed in cloud environments customers have evolved, so have the needs of security teams who monitor these resources. A CSPM solution should not only report continuously on your organization’s security and compliance posture but also provide alerting and reporting capabilities that help security and DevOps teams operate more efficiently. To take full advantage of CSPM tools, follow this four-step approach:
- Detect:
Use CSPM to continuously scan infrastructure assets for misconfigurations and any violations of industry-specific compliance standards.
- Prioritize:
Configure CSPM to send alerts to relevant team members based on security rules, asset sensitivity, and issue severity.
- Triage:
Develop a system for routing and assigning alerts, establish rules for hand-offs, and maintain historical data on your investigations for future audits and research. Consider muting or suppressing unnecessary alerts to reduce workloads.
- Remediate:
Once you’ve triaged an issue and prioritized it for remediation, use integrations available in your CSPM solution to notify the teams responsible for configuring affected resources using tools such as Slack, Microsoft Teams, Jira, or other incident management tools.
What are the best tools for Cloud Security Posture Management?
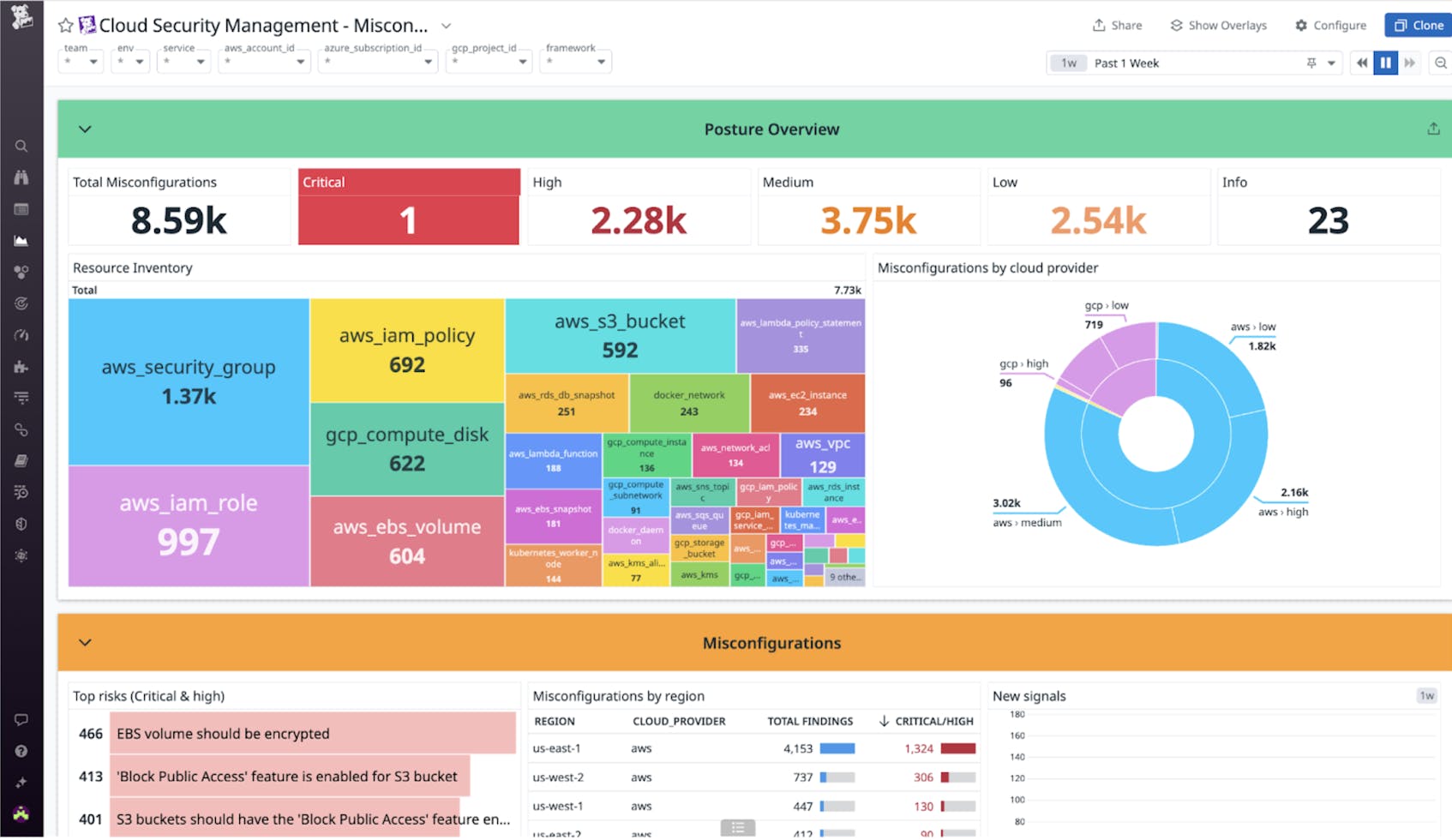
Your cloud infrastructure will continue to evolve and grow over time, making security a continuous process rather than a one-time fix. Datadog Cloud Security Management (CSM) includes CSPM capabilities that help you streamline your organization’s security and compliance process. Datadog CSM can be utilized across different teams with many responsibilities—equipping them with a robust set of tools to manage and monitor the security posture of your cloud infrastructure.
Datadog CSM enables you to identify and continuously monitor misconfigurations, unsecured accounts, API token issues, containerized environments, and other risks within your organization’s cloud infrastructure. It includes a Misconfigurations dashboard that highlights key issues and helps you monitor your security posture on an ongoing basis.
In addition to identifying risky configurations in your cloud infrastructure, Datadog CSM helps ensure compliance with industry standards, surfaces identity-based risks, and pinpoints potential threats across all of your cloud workloads.