What Is SNMP?
Simple Network Management Protocol (SNMP) is a network protocol that is native to IP networks and compatible with most network devices. SNMP monitoring provides a standardized way for network engineers and admins to gather information about networking equipment, and helps ensure that a company’s network is running smoothly. Many network monitoring tools rely on SNMP to gain visibility into network infrastructure, such as routers, switches, and firewalls.
SNMP was developed in 1988 as a utility to be standardized across all networking equipment. Major network appliance vendors built SNMP support into their devices so network engineers had a uniform way to gather information from their devices, independent of the vendor they purchased their equipment from. Today, few additional protocols have been as widely adopted as SNMP.
In this article, we’ll discuss how SNMP monitoring works, the key types of information you can collect with it, and how to get started with using SNMP to monitor your networking equipment.
How SNMP Monitoring Works
SNMP monitoring can be used to collect information from your entire fleet of network devices. SNMP relies on a client-server application model, where a software server component (the SNMP Manager) collects information by querying a software client component (the SNMP Agent), which runs on a network device. You can also configure the SNMP Agent to send information to the manager without being queried. The SNMP Agent comes pre-installed on most network devices. To start collecting device information, you would enable SNMP on the device, and configure an SNMP Manager to begin communicating with the device.
Components of SNMP Monitoring
SNMP provides a flexible framework, with several components working together to enable network engineers to monitor the health and performance of devices:
- SNMP Manager
The server, or other external process, that will poll network devices for information and collect the responses. SNMP Managers may also be referred to as Network Management Stations (NMSs).
- SNMP Agent
The software client that is pre-installed on most network devices. The SNMP Agent will store information about device status and relay this to the SNMP Manager when polled.
- Managed Device
A network device on which the SNMP Agent is installed, enabled, and configured. Routers, switches, firewalls, and wireless access points are examples of devices that you can manage via SNMP.
- Management Information Base (MIB)
A dictionary of hierarchically structured information from a device. Each entry in a MIB contains the object identifier (OID) and its human-readable definition.
- Object Identifier (OID)
An address on a device that represents a specific piece of information. OIDs can represent any measurable information such as uptime, fan speed, or temperature, as well as configurable elements like maximum bandwidth or device name.
These pieces work together to allow network engineers to extract useful information from network devices, regardless of the vendor, the device type, or the software running on the device.
SNMP Monitoring Commands
The SNMP Manager uses a set of commands to get information about managed devices from SNMP Agents. Agents also use commands to send device information to managers.
These are some basic SNMP commands that managers and agents use for monitoring network devices:
- Get
The SNMP Manager sends a Get query to the SNMP Agent in order to retrieve a specific piece of device information, represented as an OID.
- Response
The SNMP Agent retrieves the requested OID from the MIB and sends the data to the SNMP Manager.
- GetNext
This command requests the value of the next OID in the MIB tree. When you need to obtain more than one piece of data from a network device, you can efficiently use Get followed by GetNext instead of two separate Get commands.
- GetBulk
Using this single command, the SNMP Manager can retrieve multiple pieces of information from a network device. This command is supported by SNMP v2 and later versions.
- Trap
This is an agent-initiated command through which the agent informs the manager of specific events. For example, you can configure an agent to notify the manager when CPU utilization on a specific device exceeds 80 percent for one minute. From a monitoring standpoint, traps are one of the most important SNMP functions. Without SNMP traps, you’d have to wait for the manager to poll a device before finding out critical information. Traps allow you to identify network issues early and contain them before their impact spreads.
- Inform
This is similar to a Trap command, but here the SNMP Manager acknowledges receipt of the agent’s notification. This command is available only in SNMP v2 and later.
- Set
SNMP managers can use a Set command to change configurations on a managed device.
Note that in most cases, network engineers and admins don’t explicitly run these commands. Rather, they rely on monitoring applications to run SNMP commands behind the scenes and gather data from devices.
SNMP v1, v2, and v3: What’s Different?
As the SNMP protocol has matured, additional features have been added to improve its security and efficiency. Under v1, the initial version of the protocol, SNMP managers would authenticate to SNMP agents through the use of a password (called a community string). However, this community string was sent in plain text, making it easy for unauthorized parties to gain access to device information. In addition, SNMP v1 supported only 32-bit counters when it counted the bytes transferred through network interfaces. After reaching the 32-bit limit (approximately 4.3 billion bytes), the counter would reset, and you would lose the device data you had collected to that point. This limitation made it challenging to measure throughput in large, modern networks.
The release of SNMP v2, which is still widely used today, helped resolve some of the weaknesses of SNMP v1. First, SNMP v2 added 64-bit counters to accommodate higher network throughputs. This version also introduced new commands to expand the functionality and improve the efficiency of the protocol. For example, the GetBulk command introduced the ability for SNMP managers to fetch multiple pieces of information about a device by using a single message. The Trap command gave SNMP agents the ability to asynchronously send data to an SNMP Manager without being polled.
SNMP v3 is the most secure of the three versions. In this most recent version, a username and password are required to retrieve device information, and device data is encrypted. Because of these enhanced security measures, v3 is the version of SNMP that is recommended for devices that are reachable from the public internet.
SNMP Metrics
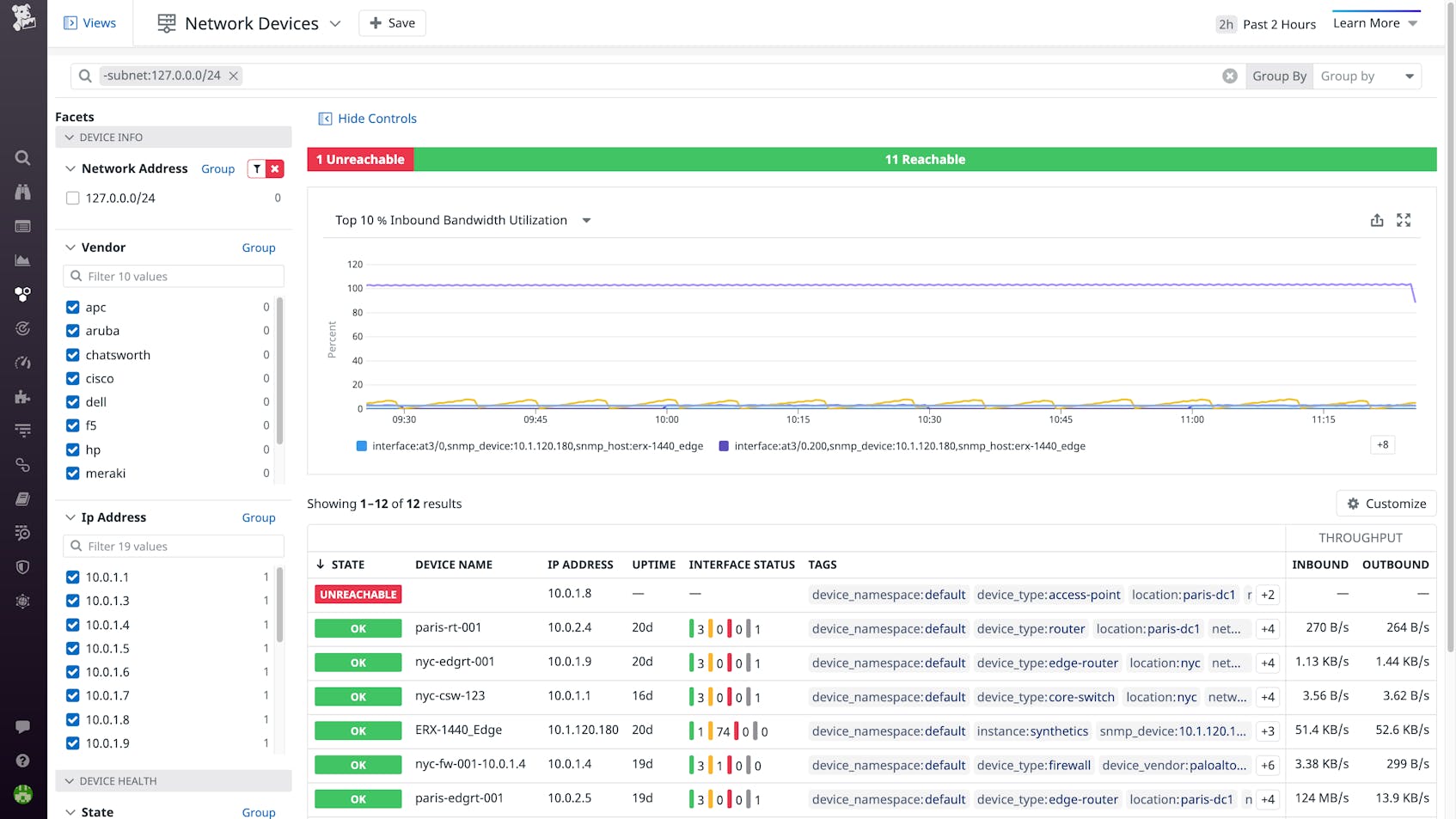
SNMP allows you to collect a wide variety of metrics from network devices, such as uptime, throughput, temperature, interface errors, CPU utilization, and memory usage. An advanced SNMP-compatible monitoring tool enables teams to analyze changes in such metrics over time, to visualize their metrics in dashboards, and to alert on metrics that exceed a specified threshold.
To add more context to metrics, some network monitoring tools offer tagging. Tags add dimensions to your device metrics so that the performance of different subsets of devices can be aggregated, analyzed, and compared. For example, you can tag each device by datacenter location to understand if devices within a specific datacenter are exhibiting an outsized number of errors.
SNMP Monitoring Tools
Network engineers and admins are responsible for ensuring that their organization’s network is continuously available and performing as expected. In order to help ensure network health and performance, you need visibility into the performance of all your network devices.
Datadog Network Device Monitoring (NDM) leverages SNMP to automatically discover and monitor network devices at any scale and across multiple vendors. You can aggregate metrics across all devices or use tags to filter down to a specific subset when you are investigating a network outage or incident. With machine-learning based alerts, you can get notified automatically when bandwidth utilization or another metric approaches a critical threshold. Most importantly, a single pane of glass unifies network device metrics with infrastructure, application, and security metrics. Thanks to this unified view, engineers and administrators across an organization can work together to monitor and improve the delivery of the company’s services over the network.
Get started with Network Device Monitoring today to get complete visibility into your network.