Collaboration platforms like Atlassian Jira and Atlassian Confluence contain sensitive company and employee data, making them critical targets for cyberattacks. Teams use Jira to track and manage projects, and rely on Confluence as an internal knowledgebase for documentation, company policy guides, team wikis, and more. Atlassian organizations, which provide a centralized place for admins to manage their Atlassian products and users, are also prime targets. These environments bring with them a host of security risks, including unprotected files that may contain sensitive information, insecure or outdated passwords, and corporate networks accessed by employees’ personal devices, which can be vulnerble to viruses and malware.
Datadog’s Atlassian Jira and Confluence Audit Records and Atlassian Organization Audit Logs integrations enable you to collect and process Jira, Confluence, and organization audit logs, which contain data about activities such as account management, system configuration, and product access changes. Security teams can then visualize this data and generate metrics and alerts from it from within a centralized platform. In this post, we’ll look at how you can use Datadog Cloud SIEM to get automatic detection of suspicious user and admin activity as well as enhanced visibility into your security posture with enhanced dashboards.
Centralize alerts, threats, and activity from Atlassian audit and event logs
To quickly get started monitoring your Atlassian Jira and Confluence environments and Atlassian organizations with Datadog Cloud SIEM, you can use the Atlassian Jira and Confluence Audit Records Content Pack and Atlassian Organization Event Logs Content Pack. These Content Packs provide a centralized place to enable and configure Datadog’s Atlassian integrations, deploy preconfigured detection rules, and access each integration’s customizable dashboard.
Centralize Atlassian Jira and Confluence audit log activity
From the Atlassian Jira and Confluence Audit Records Content Pack, you can seamlessly enable the Jira and Confluence Audit Records integration and begin ingesting audit logs from your Atlassian Jira and Confluence environments. These logs capture key activities, such as user account management, project configuration updates, and space and page actions. System configuration changes—including those to global settings, application links, and add-ons—are also logged alongside authentication and authorization events. By forwarding audit records activity, organizations can perform real-time analysis, long-term investigations, threat hunting, and custom detection development.
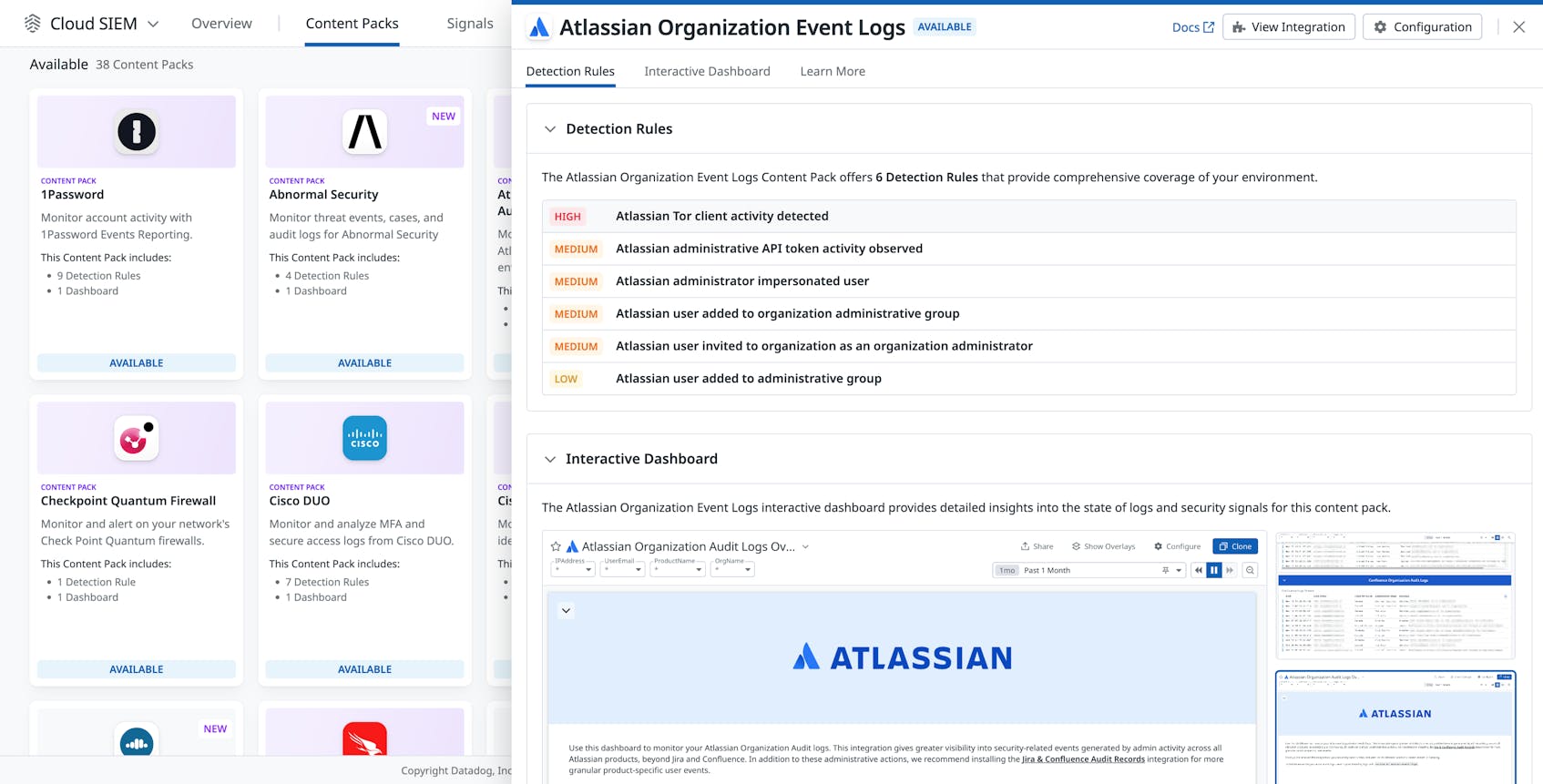
Centralize Atlassian organization event log activity
From the Atlassian Organization Event Logs Content Pack, you can easily enable the Atlassian Organization Audit Logs integration, which centralizes event logs from your Atlassian organization in Datadog, providing visibility into administrative actions across all Atlassian products—not just Jira and Confluence. These logs capture critical details about group management, group access configurations, and product access changes. If your organization uses Atlassian Guard Premium, additional logs can provide insights into user-created content and classification activities.
Datadog Log Management’s log-processing pipeline normalizes and enriches your Atlassian audit and event logs, allowing for efficient searching and analysis at any scale. You can retain all of your logs for a standard 15 months, or variably with Flex Logs to accommodate different use cases. Either way, being able to cost-effectively store log data supports historical investigations of deeply embedded threats and sophisticated attacks that typically occur over long periods of time.
With these logs in Datadog, you can set up Cloud SIEM detection rules for any preconfigured logs pipeline, build custom dashboards, and cross-reference Atlassian events with other services for deeper insights. The integrations also support data retention control, which enables long-term investigations, and real-time threat detection.
Automatically detect threats with built-in and custom detection rules
Datadog detection rules can automatically generate security signals that include additional context about a security issue as well as suggested actions to take. These rules help security teams identify key attack stages, from credential theft to data extraction and destruction tactics.
Detect suspicious activity in Atlassian Jira and Confluence audit records
You can only act on suspicious Jira and Confluence audit activity as fast as you’re alerted to it. Datadog continuously scans your Atlassian logs as it ingests and processes them. Built-in detection rules that are mapped to the MITRE ATT&CK® framework automatically look for specific threat indicators and stream generated security signals in a unified explorer, helping to streamline security investigations and threat detection. You can also create custom detection rules to enrich these logs with additional business-specific context.
Security risks can be addressed with built-in detection rules to help organizations safeguard sensitive data and configurations. For example, the Atlassian Tor client activity detected rule flags suspicious access attempts from Tor networks, which are often associated with anonymity-seeking attackers probing for vulnerabilities or attempting unauthorized access. By identifying such activity, organizations can mitigate potential breaches early.
Other critical use cases include monitoring sensitive administrative actions in Confluence. For example, the Atlassian Confluence admin key usage and Confluence global setting changed rules detect unauthorized or unusual administrative actions, such as altering system configurations or using admin privileges to access restricted data. Additionally, export activities such as Confluence site export and Confluence space export can be tracked to identify potential exfiltration attempts of intellectual property or sensitive documents. Lastly, the Confluence public link turned on rule highlights when private content is inadvertently or maliciously made publicly accessible, which could lead to data exposure.
Detect suspicious activity in Atlassian organization event logs
Datadog Cloud SIEM provides built-in detection rules tailored to Atlassian organization event logs, enabling security teams to monitor and respond to potential threats targeting administrative access and organizational integrity. For example, the Atlassian Tor client activity detected rule detects suspicious access attempts from Tor networks. The Atlassian administrative API token activity observed rule monitors the usage of API tokens associated with high-privilege accounts, detecting unauthorized or unusual activity that could indicate compromised credentials or insider threats. Similarly, the Atlassian administrator impersonated user rule flags when an admin takes actions on behalf of another user, a behavior that could point to malicious activity or mismanagement.
Additional detection rules track changes to administrative groups and roles, which are common vectors for privilege escalation. The Atlassian user added to organization administrative group, Atlassian user invited to organization as an organization administrator, and Atlassian user added to administrative group rules alert teams to new administrative access assignments, enabling swift investigation of potentially unauthorized changes that could increase organizational risk.
Monitor Atlassian logs and alert activity with preconfigured dashboards
Datadog provides preconfigured dashboards that visualize ingested Atlassian log data so that you can easily track threats across your infrastructure over time by confidence level. This offers essential insights that help security teams quickly assess the health and security of their environment. With features like geolocation maps for login origins and toplists of frequent or rare activities, this actionable visibility enables you to perform real-time analysis, long-term investigations, and threat hunting, as well as develop custom detections to enhance your organization’s security posture.
The Atlassian Jira and Confluence Audit Records dashboard includes widgets that display key metrics such as user and admin event counts, sys admin and super admin event counts, and audit events for user management over time, complemented by a user management log stream for granular insights. The dashboard offers an overview of Confluence audit records, showcasing log counts by source, frequent events (such as permissions, users and groups, spaces, admin key usage, page edits, content changes, and import/export activities), and infrequent events (such as admin key actions, space configurations, and export operations). A dedicated permissions log stream further enhances visibility into access control changes.
The Atlassian Organization Event Logs dashboard features widgets like an Atlassian organization audit logs overview, displaying log counts by source, frequent events, and infrequent events for quick anomaly detection. Additional widgets highlight activity by IP address, top organizations, top users, and frequent log messages. Dedicated streams for Confluence organization audit logs and Jira organization audit logs enable real-time monitoring of changes within Confluence, Jira software, and Jira Service Management environments.
Get deeper visibility into collaboration platforms with Datadog Cloud SIEM
Datadog Cloud SIEM and our Atlassian integrations provide organizations with a powerful, unified platform that enhances their visibility, threat detection, and incident response across their collaboration platforms. These integrations ensure seamless monitoring, enabling security teams to respond more effectively to evolving threats and maintain a stronger security posture.
If you’re already a Datadog customer, see our Atlassian Jira and Confluence Audit Records documentation or Atlassian Organization Event Logs documentation and start exploring the new Atlassian Jira and Confluence Audit Records Content Pack or Atlassian Organization Event Logs Content Pack. If you’re not a Datadog customer, you can get started today with a 14-day free trial.