Connect to Datadog over AWS PrivateLink using AWS Transit Gateway
8月 26, 2024
Introduction
Large-scale networks require simplified network architecture and scalability to facilitate efficient operations and growth. AWS Transit Gateway provides a transit hub-spoke model that enables you to interconnect thousands of VPCs from the same and different AWS regions, data centers, and remote networks while providing streamlined network management and reduced operational complexity.
In the Connect to Datadog over AWS PrivateLink using AWS VPC Peering reference architecture, we demonstrated the usage of AWS PrivateLink and VPC Peering to connect small-scale networks to use the AWS backbone to send telemetry data to Datadog PrivateLink Endpoints without traversing the internet.
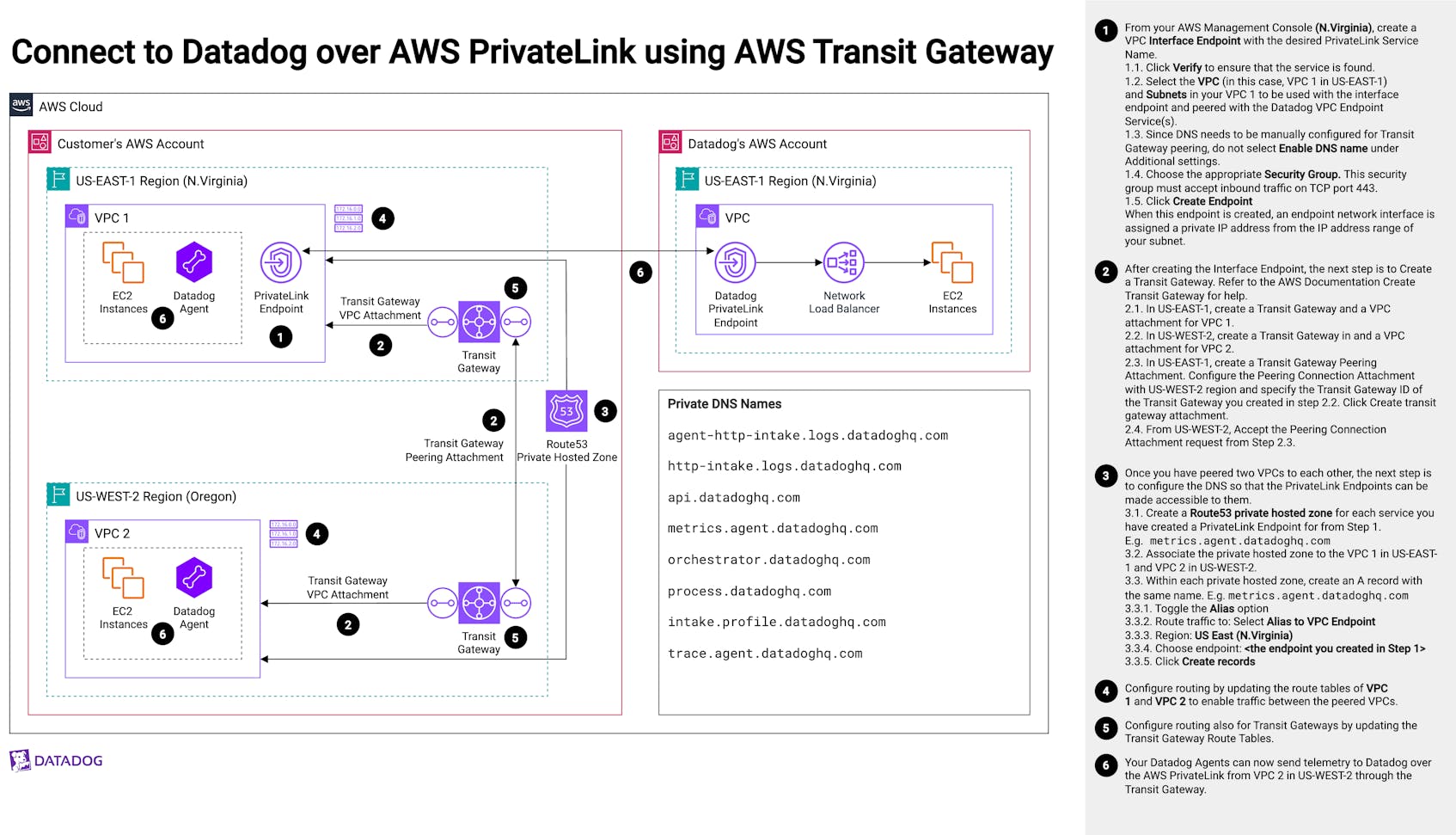
This architecture represents the overall deployment and configuration of AWS Transit Gateway and AWS PrivateLink integrated with Datadog, so that the Datadog Agents running in your EC2 instances in different AWS regions (US-EAST-1 and US-WEST-2) can send data to Datadog without traversing the internet.
Explanation of the architecture
- 1. From your AWS Management Console (N.Virginia), create a VPC Interface Endpoint with the desired PrivateLink Service Name.
- 1.1. Click Verify to ensure that the service is found.
- 1.2. Select the VPC (in this case, VPC 1 in the US-EAST-1) and Subnets in your VPC 1 to be used with the interface endpoint and peered with the Datadog VPC Endpoint Service(s).
- 1.3. Since DNS needs to be manually configured for Transit Gateway peering, do not select Enable DNS name under Additional settings.
- 1.4. Choose the appropriate Security Group. This security group must accept inbound traffic on TCP port 443.
- 1.5. Click Create Endpoint. When this endpoint is created, an endpoint network interface is assigned a private IP address from the IP address range of your subnet.
- 2. After creating the Interface Endpoint, the next steps are to Create a Transit Gateway. Refer to the AWS Documentation Create Transit Gateway for help.
- 2.1 In US-EAST-1, create a Transit Gateway and a VPC attachment for VPC 1.
- 2.2 In US-WEST-1, create a Transit Gateway in and a VPC attachment for VPC 2.
- 2.3 In US-EAST-1, create a Transit Gateway Peering Attachment. Configure the Peering Connection Attachment with US-WEST-2 region and specify the Transit Gateway ID of the Transit Gateway you created in step 2.2. Click Create transit gateway attachment.
- 2.4 Switch over to US-WEST-2, and accept the Peering Connection Attachment request from Step 2.3.
- 3. Once you have peered the two VPCs together, the next step is to configure the DNS so that the PrivateLink Endpoints can be made accessible to them.
- 3.1 Create a Route53 private hosted zone for each service you have created a PrivateLink Endpoint for from Step 1 (e.g.,
metrics.agent.datadoghq.com). - 3.2 Associate the private hosted zone to the VPC 1 in US-EAST-1 and VPC 2 in US-WEST-2.
- 3.3 Within each private hosted zone, create an A record with the same name (e.g.,
metrics.agent.datadoghq.com).
- 3.3.1. Toggle the Alias option.
- 3.3.2. Route traffic to: Select Alias to VPC Endpoint.
- 3.3.3. Region: US East (N.Virginia).
- 3.3.4. Choose endpoint: < the endpoint you created in Step 1 >.
- 3.3.5. Click Create records.
- 3.1 Create a Route53 private hosted zone for each service you have created a PrivateLink Endpoint for from Step 1 (e.g.,
- 4. Configure routing by updating the route tables of VPC 1 and VPC 2 to enable traffic between the peered VPCs.
- 5. Configure routing also for Transit Gateways by updating the Transit Gateway Route Tables.
- 6. Your Datadog Agents can now send telemetry to Datadog over the AWS PrivateLink from VPC 2 in US-WEST-2 through the Transit Gateway.
Authors
Lowell Abraham, Sr. Product Solutions Architect
References
Inspiration and reference documents or existing solutions: