
Nicholas Thomson

Shanel Huang
The Windows Registry is a centralized key-value database that stores permissions, user data, and configuration settings for the Windows operating system and many Windows native applications. The keys stored in the registry provide a granular view into the processes occurring on a Windows host, such as certificate expirations, security checks, and pending reboots.
Datadog’s Windows Registry integration enables joint Windows and Datadog users to collect the value of any registry key in Datadog. This means Windows customers can now monitor unexpected changes of values only available in the registry. Monitoring these events can help teams stay ahead of issues caused by outdated registry values, ensure that permissions are in accordance with security best practices, and get detailed information on user behavior. This unified source of information can help teams to maintain the overall health of their Windows systems.
In this post, we'll show you how to:
- Understand how registry events impact performance
- Create a Datadog Monitor to be notified when a critical registry key value changes
- Create Cloud SIEM security signals and automated workflows from Windows Registry logs
Understand how registry events impact performance
The Windows Registry integration is included in the Datadog Agent package, so no installation is needed. You can use Log Management’s out-of-the-box pipeline to automatically parse, enrich, and tag your Windows events. Then, logs from Windows Registry will appear in the Log Explorer, where you can filter by the facet source:windows_ registry to see only Windows Registry logs, or get further granularity by filtering for the registry key or the message of the log you’re interested in.
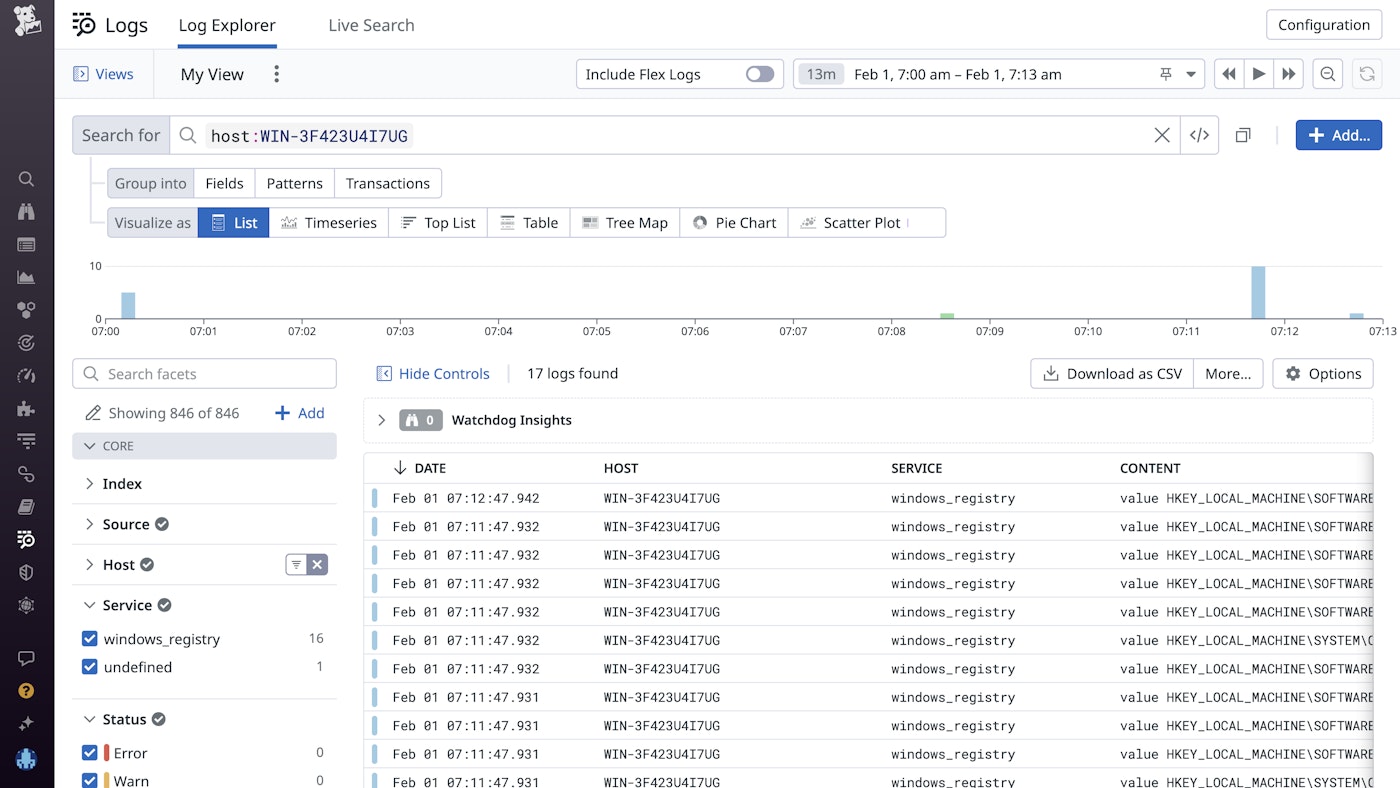
You can use these logs to gain deep visibility into critical activity on your Windows hosts. For example, say you're a security engineer, and you want to ensure that your application is compliant with security best practices. One potential vulnerability you are looking for is machines that have automatic logon enabled, as this can bypass security measures such as passwords.
You navigate to the Log Explorer and filter for Windows Registry logs that contain logon activity. You find a log from Windows Registry with the subkey: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon and with a value that has just changed from 0 to 1, indicating that this machine has recently been switched to automatic logon.
With this knowledge in hand, you can investigate the machine further to determine if this is a possible sign of attacker activity, or if there is a valid reason for automatic logon being switched on.
Create a Datadog Monitor to be notified when a critical registry key value changes
The Windows Registry is the most granular source of information on a Windows machine, containing all information on users, their specific permissions, and other important data. This means you can use the registry to monitor a number of important changes—but the registry doesn't allow you to create alerts natively. Instead of manually searching the registry for events pertinent to your incident investigations, you can stream the logs into Datadog, create custom metrics from them, and then create monitors on metric thresholds to alert you when a change occurs that you need to know about.
Say you're an SRE at a Windows-native application, and you want to ensure that your app doesn't lose functionality due to an expired certificate. So you decide to create a monitor on your system's SSL certificate to alert you when it is near expiration.
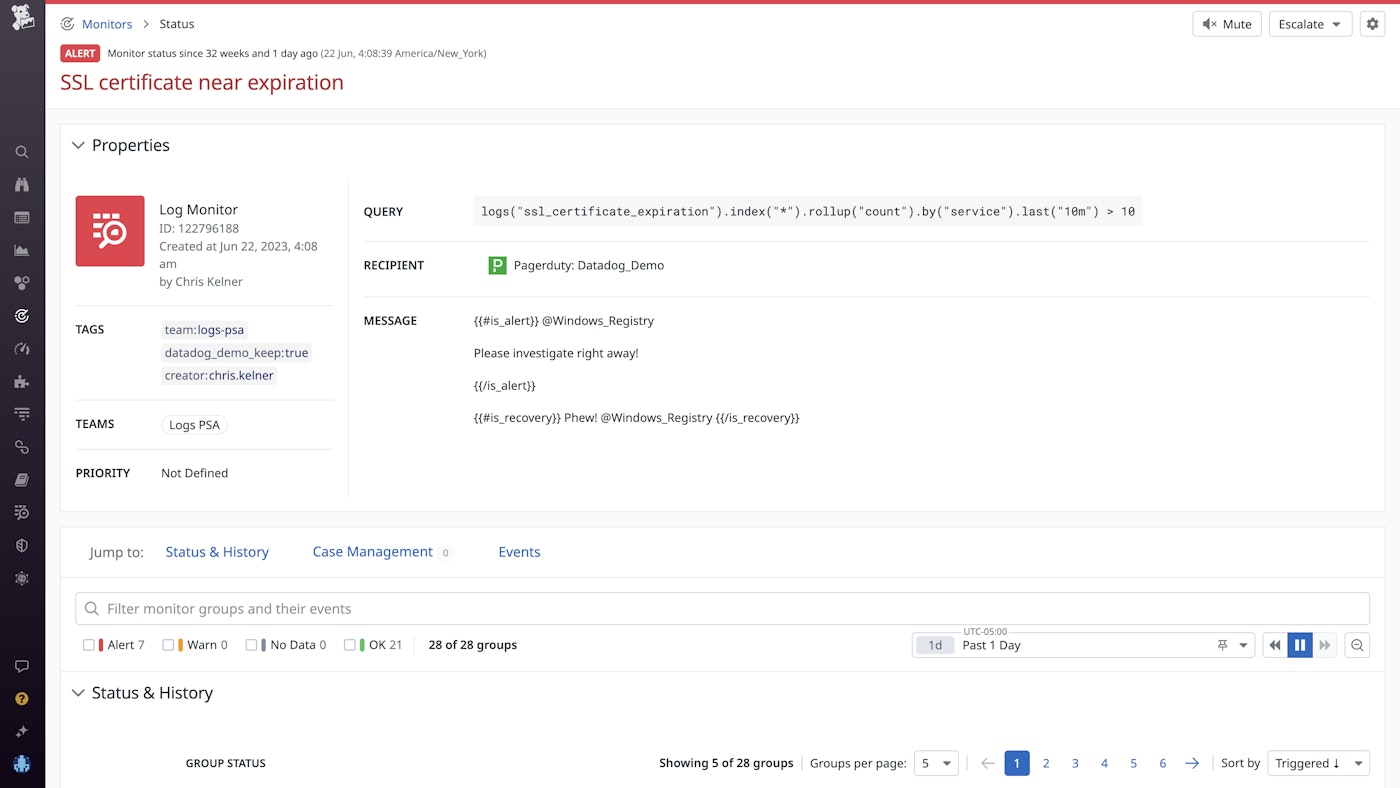
To do this, you can create an alert that scans your logs tagged source:windows_registry looking for an indication of a certificate expiration warning in the messages. This will allow you to stay ahead of certificate expirations and ensure availability of your application.
Create Cloud SIEM security signals and automated workflows from Windows Registry logs
Windows Registry logs can be consumed by Datadog's Cloud SIEM, which provides out-of-the-box detection rules for Windows, so you can monitor your systems for suspicious activity. Cloud SIEM can ingest, scan, and enrich any logs you send in from the Windows Registry, enabling you to add additional context to your detection rules.
For example, say you're a security engineer, and you want to create a security signal from a registry log alerting you when Windows Defender is disabled, so you create a detection rule using this Windows Registry key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection\DisableRealtimeMonitoring.
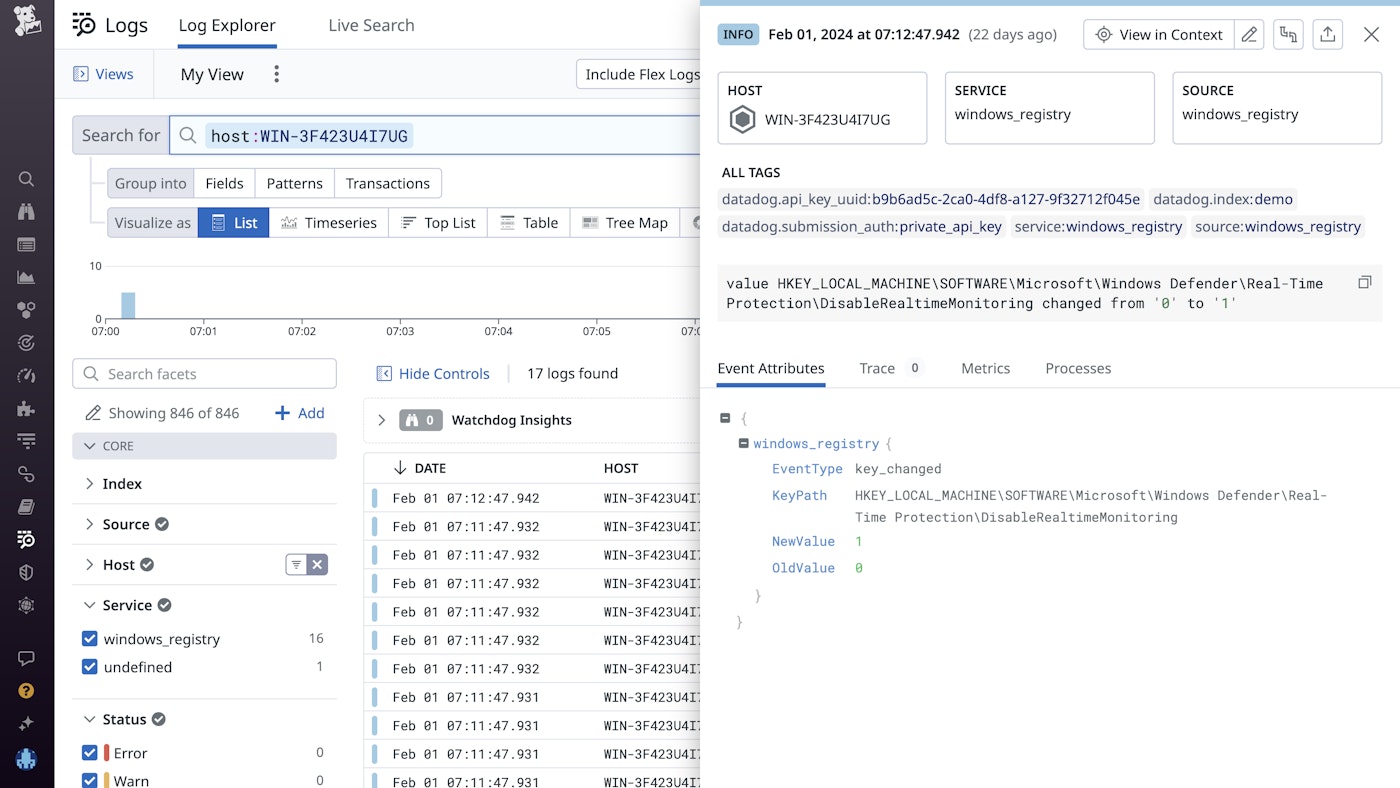
You can then create a workflow that automatically determines if the activity came from a suspicious IP and alerts the necessary members of your team if the threat is deemed serious.
Start monitoring Windows Registry activity
Datadog’s Windows Registry integration enables you to monitor, alert on, and enrich Cloud SIEM detection rules with data from the registry. This will help you troubleshoot issues affecting end users, enhance security guardrails to prevent malicious actors from taking advantage of vulnerabilities, and more.
If you’re new to Datadog, sign up for a 14-day free trial.





