Amber Bennoui

Matt Mills
As serverless infrastructure grows in popularity, customers are increasingly deploying ECS and EKS containers via AWS Fargate. Although Fargate removes the need to manage underlying servers and clusters, it does not eliminate all security risks. In fact, these environments can introduce more sophisticated security challenges.
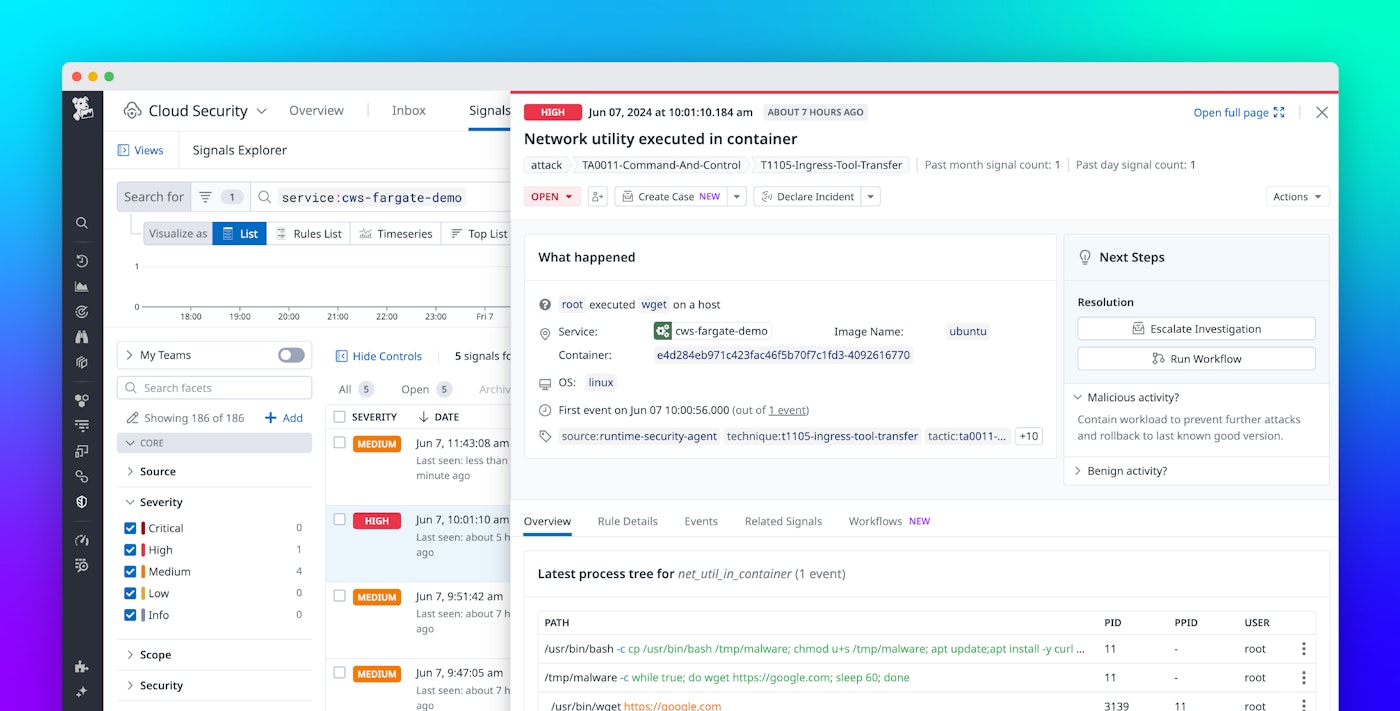
With Datadog Cloud Security support for AWS Fargate, AWS Fargate ECS and EKS customers can now monitor for suspicious process and file activity, such as the execution of a network utility in a container or file permission changes. When a security signal is triggered, Cloud Security automatically correlates it with observability data, providing the necessary context to quickly investigate and remediate threats. The Datadog Agent continuously monitors processes and file system changes, detecting anomalies like malicious file changes, suspicious processes, and unauthorized activities using 150+ rules designed for serverless containerized workloads. File Integrity Monitoring (FIM) also helps customers meet compliance requirements like PCI and FedRAMP by monitoring unauthorized file modifications within containers.
The following dashboard provides a comprehensive view of all detected threats, enabling swift investigation and response:
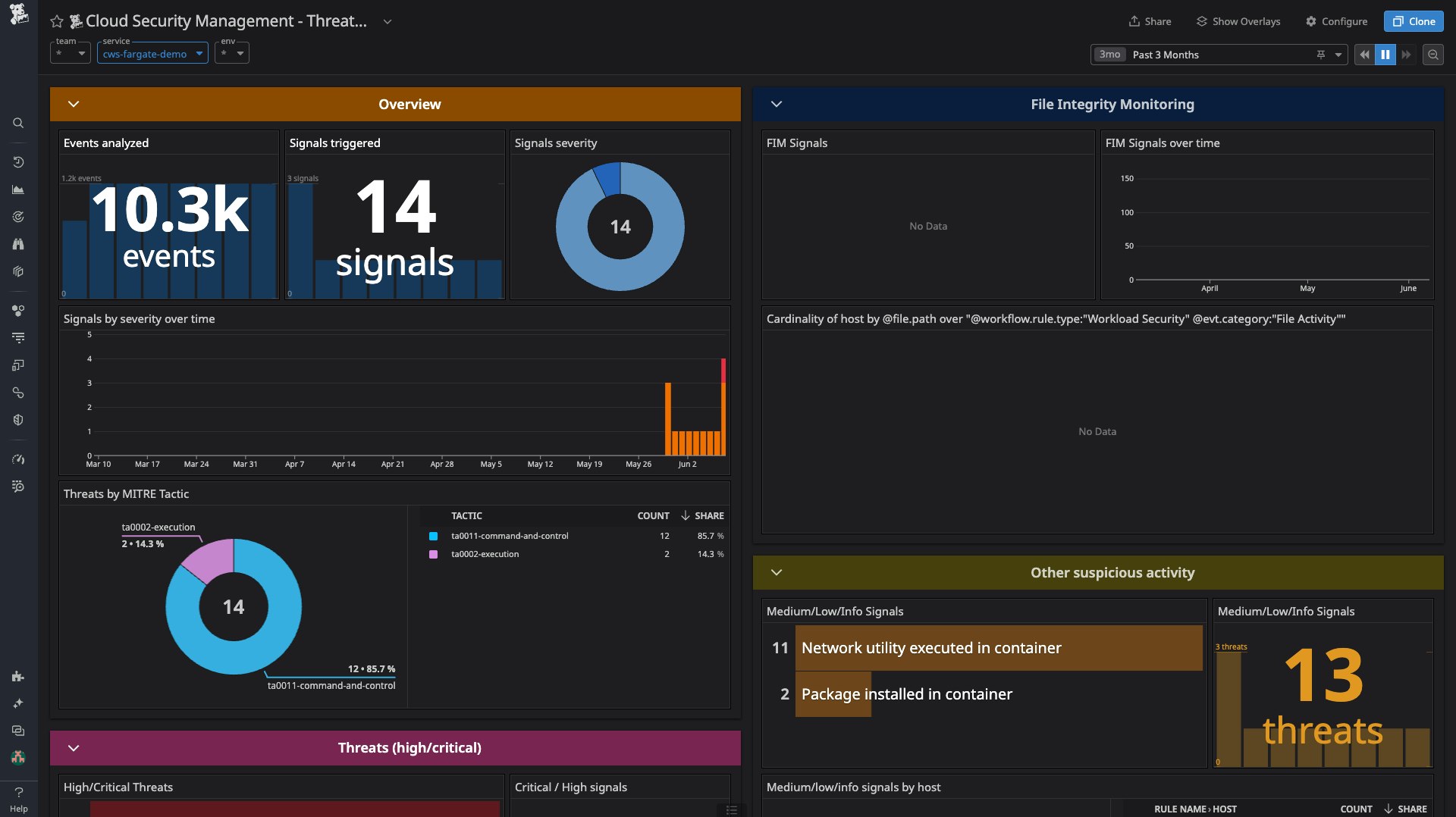
This post introduces some of the common threat actors and techniques targeting ECS and EKS containers deployed via AWS Fargate, and describes how the Datadog Agent—complemented by Datadog Cloud SIEM and AAP—enables you to detect threats using OOTB rules.
The ECS on Fargate threat model
Due to the shared responsibility model, applications deployed on ECS on AWS Fargate have a reduced attack surface. Contrary to the classic “ECS on EC2” deployment model, when you deploy containers using AWS Fargate, each task has its own isolation boundary (implemented by a light virtualization technology, Firecracker VMs). Two tasks never share the same underlying kernel, network interface, or memory resources. In addition, when you use AWS Fargate, AWS manages the security of the underlying instance in the cloud and the runtime that’s used to run your tasks.
Attackers typically use one of the following three tactics to gain initial access to or execute on ECS containers deployed via AWS Fargate:
- Exploiting a publicly accessible container running vulnerable software
- Compromising AWS credentials, and creating and deploying a new task
- Compromising AWS credentials, and modifying or executing an existing task
The primary objective of most actors targeting this space has been cryptojacking, as two of the most well-known threat actors targeting Fargate—SCARLETEEL and AMBERSQUID—both deploy cryptominers. However, attempts to further compromise a victim’s assets and infrastructure have been noted as well. Behaviors such as stealing existing credentials, creating new credentials, further enumerating available infrastructure and services, and exfiltrating data have also been observed.
By using Cloud Security to monitor activity in your ECS on AWS Fargate containers, evidence of initial compromise can potentially be observed, primarily by spotting unusual file, network, and process events related to initial or post-exploitation activity. Let’s look at a couple of known attacker use cases and how Datadog’s security suite of products can detect their activities.
Detect malicious cryptomining
SCARLETEEL is known to target vulnerable public-facing services deployed in containers in Fargate. In documented attacks, once they successfully gained access to a container, they took actions such as deploying cryptominers and gaining credentials through IMDS, and then used additional tools to discover more resources to exploit.
The following Datadog Cloud Security OOTB rules will detect several of the actions taken during this type of attack:
- Network utility accessed risky cloud metadata service
- Process arguments match cryptocurrency miner
- Offensive Kubernetes tool executed
- Unfamiliar process accessed Kubernetes pod service account token
Datadog App and API Protection (AAP) can be used to detect exploitation as well. Since one of the available attack vectors involves exploiting a public-facing container, AAP could be used to detect the initial exploitation of the software hosted by the container and potentially observe any commands being passed.
AWS logs all console and API requests via AWS CloudTrail, and Datadog Cloud SIEM can ingest CloudTrail events related to ECS activity, such as updating, modifying, or executing a task. By creating detections around those behaviors and further enhancing them with OOTB detection rules designed to detect compromised IAM users and access keys, Datadog provides coverage for attackers using compromised account credentials to create or modify existing ECS tasks.
Detect malicious Docker images
The threat actor AMBERSQUID tries to stay under the radar by targeting less widely used services, such as AWS Fargate. AMBERSQUID actors use stolen AWS credentials to deploy known malicious Docker images loaded with scripts to take actions such as creating various AWS accounts and roles.
Via logs captured by AWS CloudTrail, we can see some of the actions taken within the account. The following logs show the actor creating a new user account:

And these logs show the actor creating multiple clusters and task definitions:
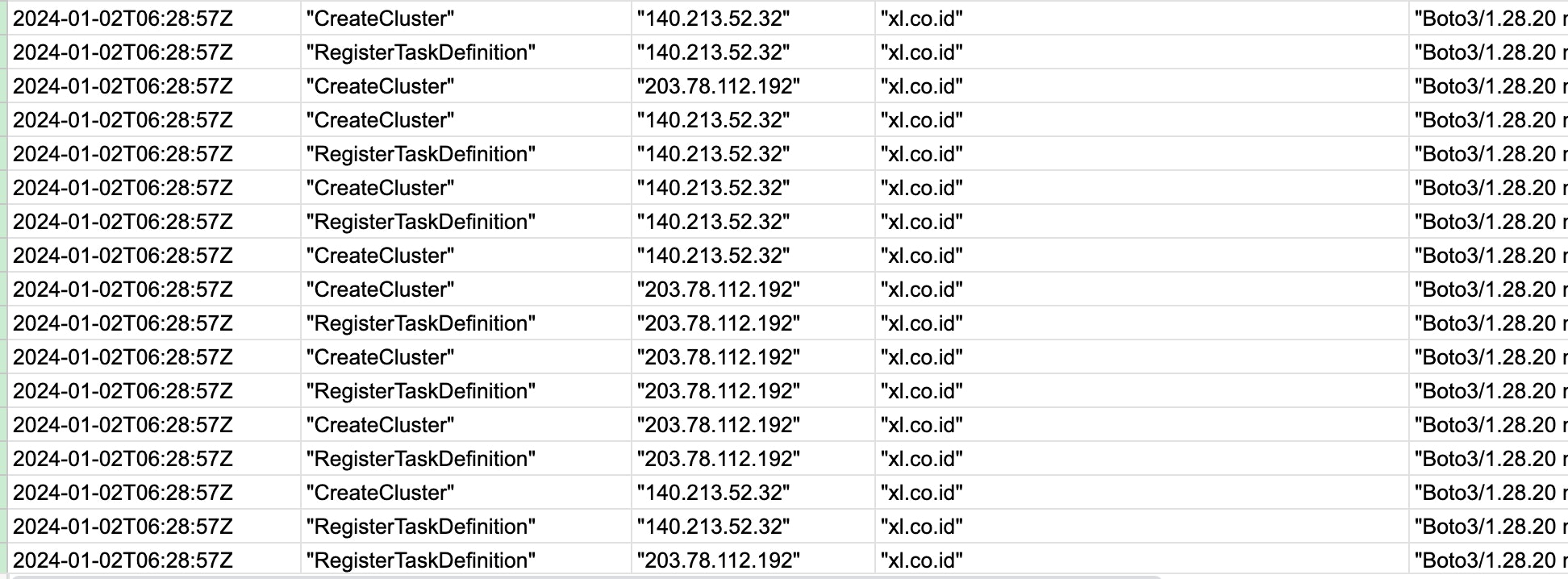
Datadog Cloud SIEM provides several OOTB rules to detect activity by compromised AWS credentials, including:
- AWS console login without MFA
- Compromised AWS IAM User Access Key
- New AWS account seen assuming a role into AWS account
Additionally, the deployment of malicious containers can be detected by this rule:
A user executing into a deployed Fargate container can be detected by the following rule:
Surface threats in your ECS and EKS workloads on AWS Fargate today
Datadog Cloud Security provides real-time threat detection in Linux, Windows, and container-based environments, and with this launch, supports AWS Fargate ECS and EKS as well. With the Datadog Agent—in addition to protection offered by Datadog Cloud SIEM and AAP—Datadog now offers full-spectrum threat detection for your ECS and EKS containers deployed via AWS Fargate.
To access Cloud Security for AWS Fargate ECS and EKS, install the Datadog Agent and enable Cloud Security. Once installed, the Agent status will display “Enabled” in Cloud Security Settings and the Agent will automatically start scanning for process and FIM threats based on the OOTB detection policy. Learn more and get started by visiting our documentation. If you’re new to Datadog, you can sign up for a 14-day free trial today.