Daniel Blazquez
A large percentage of the source code of modern cloud-native applications is open source. The benefits of open source are clear: accelerated innovation, better adoption of standards, and transparency are only some of them. However, teams must be careful when incorporating open source projects into their applications, as they can be a source of several classes of risks.
Security vulnerabilities—particularly known vulnerabilities with CVEs—are among the main risk factors that open source libraries can introduce into your software. And very often, open source libraries introduce additional risks beyond vulnerabilities. This post describes lesser-known risks to look out for in open source libraries, best practices for reducing them, and how you can use Datadog SCA to help automate protecting the health of your software supply chain.
Hidden risks in open source libraries
On top of known security vulnerabilities such as log4shell and other high-impact CVEs, open source projects can introduce the following risks into applications:
- Malware: Malicious actors exploit techniques such as typosquatting and repo and package hijacking to trick developers into installing malware.
- Licensing: The terms of open source licenses vary, and non-compliance can lead to legal issues.
- Deprecated libraries: End-of-life or outdated components introduce additional security risks due to unpatched vulnerabilities and the lack of compatibility updates.
- Unmaintained libraries: Some open source projects lack active development and become susceptible to unaddressed bugs and security flaws.
- Poor security hygiene: Some projects do not follow security best practices to assess the quality, security, and maintenance of the code. For example, some projects do not have code review practices in place.
In addition to these quantifiable risks, teams may have discretionary internal policies that determine which open source libraries are permitted into their application code. Therefore, understanding the composition and effective list of libraries and their versions for each service is important to ensuring secure open source usage.
Best practices to reduce open source risks
Application security is a responsibility shared among developers, security teams, and operations teams. Together, these teams should define processes to address the following open source security best practices:
- Practice open source due diligence: Thoroughly evaluate open source projects before incorporating them into applications. Check for known vulnerabilities, active maintenance, community support, security practices, and licensing compatibility.
- Stay updated: Update the open source components. Subscribe to security advisories and mailing lists for the open source projects to receive alerts about new vulnerabilities and updates. Define policies that dictate the resolution deadlines, and the risk-acceptance criteria.
- Adopt a process to triage and fix vulnerabilities: Often, it is impossible to fix all vulnerabilities. Establish a vulnerability management process to triage and remediate vulnerabilities in open source components, especially those in sensitive production environments.
- Measure security posture over time: Establish metrics to understand the overall posture of your open source security and its evolution over time. Expand the visibility of the security posture to all teams involved in the software delivery process.
As with all best practices, it’s unrealistic to expect that teams and organizations would be able to practice all of these perfectly. For example, with the volume of emails, Slack messages, and other notifications that engineers receive and send daily in order to complete the daily requirements of their jobs, keeping on top of security advisories about new vulnerabilities and acting on every one of them would be nearly impossible.
Automate risk reduction in your software supply chain with Datadog SCA
Manually implementing open source risk reduction practices is error-prone, and can potentially consume a large amount of time and resources. Datadog Software Composition Analysis (SCA), part of Datadog Code Security, helps automate some of these processes in order to improve your organization’s productivity and MTTR.
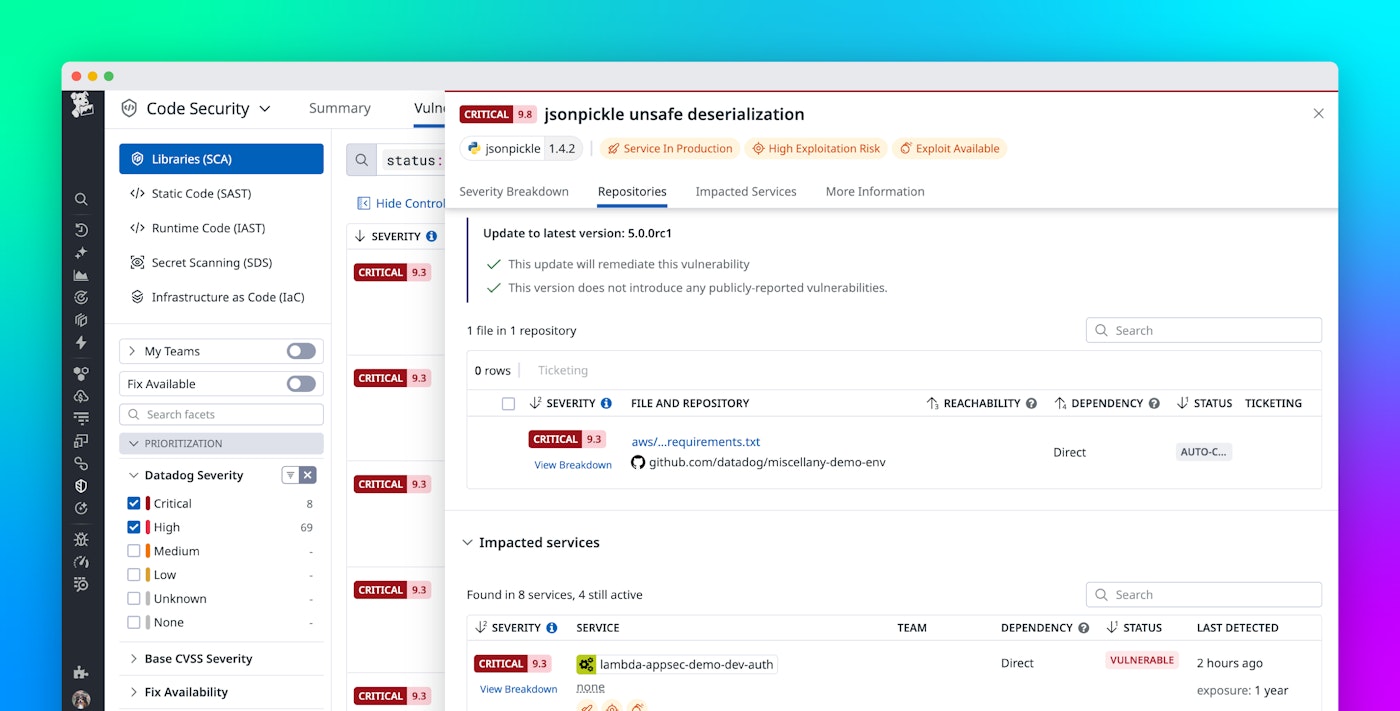
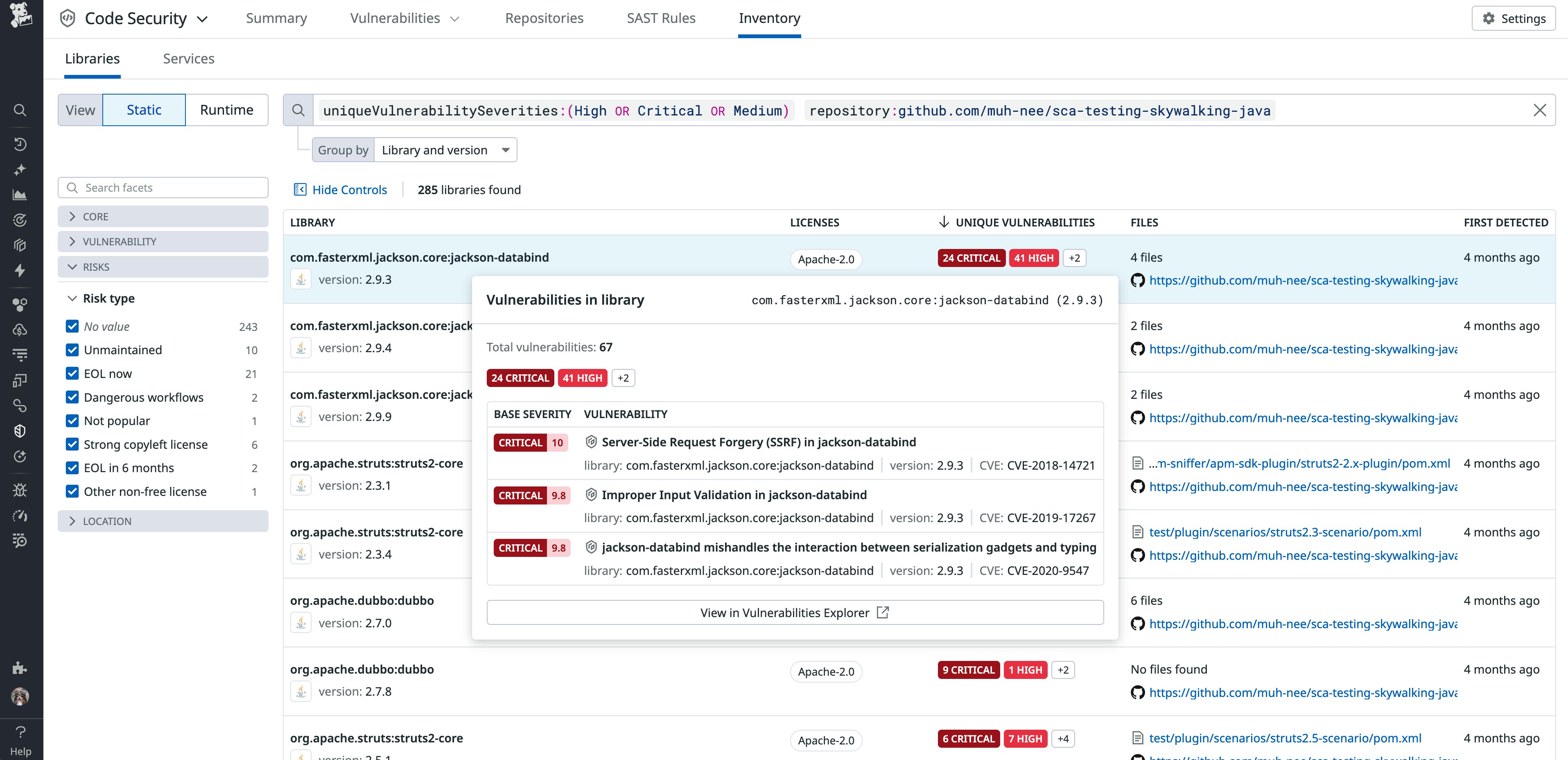
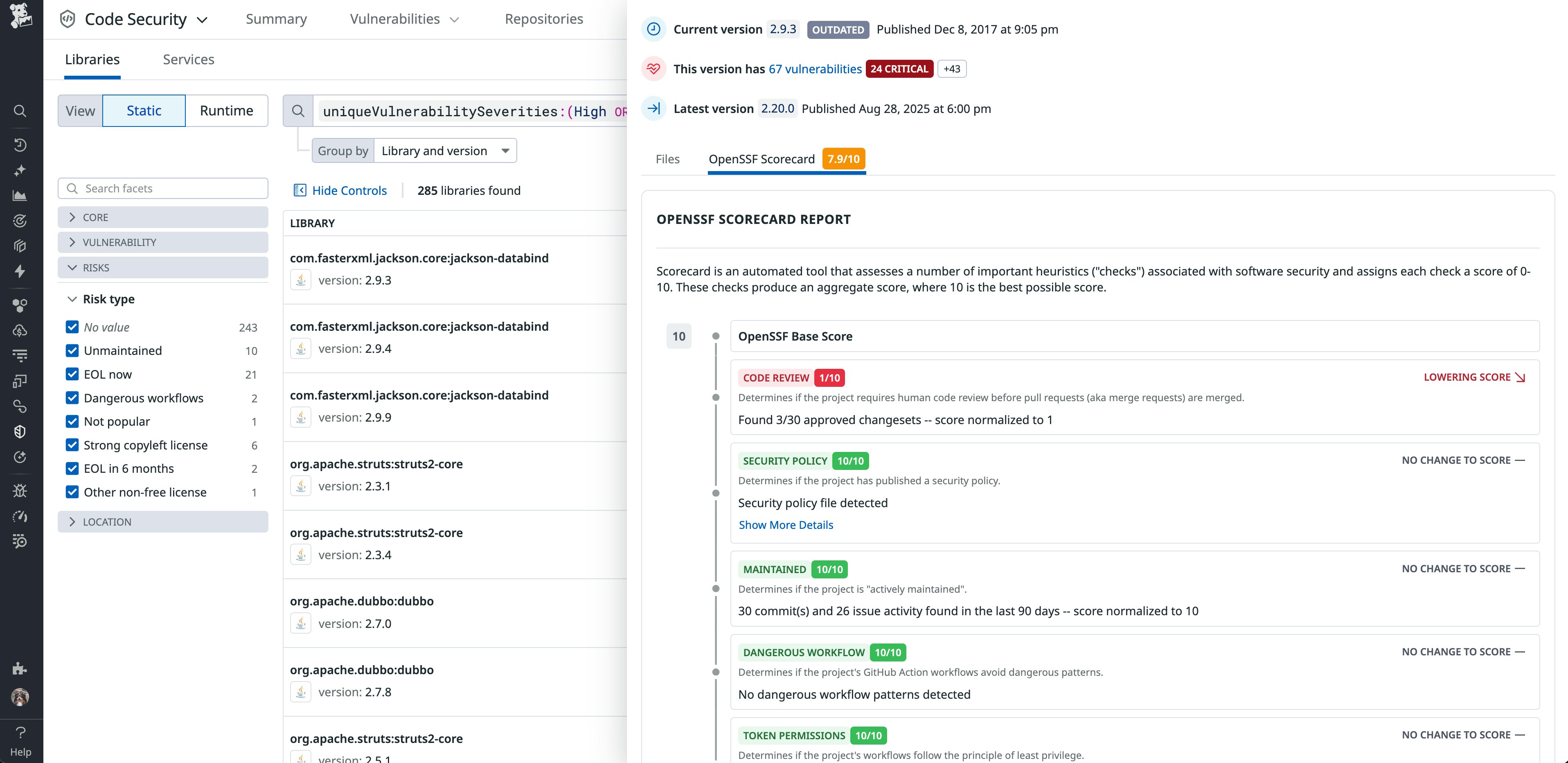
Using a combination of integrations that cover the entire software development life cycle, Datadog SCA analyzes the open source and third-party components used in your software applications in order to find vulnerabilities, malware, and other issues, such as improper licensing and poor security hygiene. Engineering teams can understand the composition of the services and see the libraries and versions in the Library catalog. Here, Datadog SCA surfaces all the details about each library and version, using several public data sources (GuardDog, NIST, osv.dev, OpenSSF scores, etc.) and private data sources (including our own Security Research group).
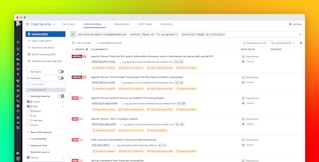
The vulnerabilities and issues found in the libraries are surfaced in the Vulnerabilities explorer, including prioritization based on the full context of your deployment.
Continuous evaluation: the heart of effective composition analysis
Traditional SCA tools work by periodically analyzing snapshots of application source code. Datadog has found that, in order to be measurably effective, code-level detection must be complemented with real-time visibility into the services already deployed, including those running in production.
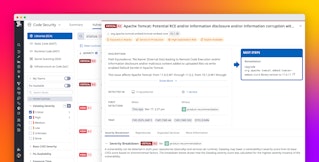
Datadog SCA incorporates everything Datadog knows about your deployment into its SCA posture calculation. It also enables you to reprioritize issues and focus on those that are exposed in sensitive production environments.
Another reason for our approach is that continuous evaluation breaks down silos and allows more teams to be involved in the security of applications, including DevOps and SREs. Elevating the visibility of open source risks to these teams helps improve the security posture of the organization and cultivates a culture of collaboration. The combination of early threat detection in application source code and real-time visibility into production services enables you to continuously monitor your libraries and ensure your security posture by maintaining awareness of security vulnerabilities, licensing issues, malware, and generally poor maintenance of open source projects.
Secure your software supply chain with Datadog
The open source movement is a driver of innovation, transparency, and convergence around standards. However, it also introduces risks, such as vulnerabilities, malware, deprecated libraries, or issues with licensing compliance, that will have an impact on the security posture of the organizations leveraging open source.
The best practices described above will reduce the risks of open source. But these practices are time-consuming to implement manually, so we recommend that teams using open source do so through automation. Datadog SCA can help automate risk management across your services, and it covers the entire software development lifecycle. Check out our documentation for more information. If you don’t already have a Datadog account, you can sign up for a free 14-day trial .