Mallory Mooney
Managing access across multiple AWS accounts is a popular approach to isolating workloads and data. While it provides several benefits to organizing the various operational requirements for the environment, it introduces additional complexity for managing IAM policies and workload permissions. A primary concern is assigning too many permissions to any one source, which increases the risk of an attacker moving within the environment undetected. In Datadog’s latest threat roundup, we noted a continued focus on cloud control plane attacks, which we observed were the result of mismanaged access controls.
To prevent unauthorized access, organizations need the ability to identify and remediate risky configurations before they can be exploited. In this post, we’ll look at common cross-account access risks in AWS and how Datadog Cloud Security Identity Risks offers actionable insights for detecting them. Datadog Cloud Security continuously scans your entire infrastructure to detect and prioritize misconfigurations, identity risks, vulnerabilities, and compliance issues. This level of visibility is important for identifying privilege escalation paths, permission gaps, and resources with either direct or indirect administrative privileges. It also helps you understand the impact of these risks to your environment so your teams can quickly remediate them.
Common IAM and permission risks
One of the most common challenges in managing multiple cloud identities, workloads, and resources across AWS accounts is the risk of mismatched or overly permissive IAM roles. For AWS environments, roles are identities with specific permissions that can be assumed by any entity that needs special, temporary access, such as a particular IAM user or workload. These scenarios can create an entry point for attackers to move across accounts, elevate their permissions, and potentially access sensitive data.
Let’s look at an example of an attacker assuming an IAM role in order to access another account. In one instance, Datadog security researchers observed an attacker attaching the AdministratorAccess policy to a newly created IAM role, which they were able to assume from a separate account. These steps enabled the attacker to gain admin-level access to the target’s AWS environment in a way that was more difficult to detect. Taking this example further, let’s assume that the IAM role already existed within the target’s environment, which is also running a public-facing Amazon Elastic Compute Cloud (EC2) instance. Misconfigurations like these can happen due to various reasons, such as oversight, convenience, or temporary fixes, but can be easily overlooked or forgotten.
How would the attacker take advantage of this scenario? If they are able to compromise the instance, they could exploit the Instance Metadata Service (IMDS) to find and use credentials associated with an attached IAM role. The attacker could then verify what actions are available for the compromised role, such as a trust policy that enables them to assume a privileged role in another AWS account. Once they pivot to that new role, then the attacker has successfully escalated their privileges. At this point, the attacker can execute other actions, such as creating new IAM users to maintain persistence, which Datadog researchers observed in the previously mentioned real-world scenario.
When an entity assumes an IAM role, AWS CloudTrail will generate a log for the sts:AssumeRole action. Check out our CloudTrail guide to learn more about interpreting these types of logs and finding the root identity of who initiated the action.
Detect cross-account access risks with Datadog
Because IAM roles with administrative privileges pose a risk to your cloud environment, it’s important to know when they exist (and when they are created). Cloud Security Identity Risks provides this visibility via Cloud Infrastructure Entitlement Management (CIEM) capabilities that are integrated with the rest of the Datadog platform. It routinely scans your cloud infrastructure—including identities and resources—to find security risks, such as permissions gaps, unused and unnecessary admin privileges, and potential cross-account access. These scenarios include:
- An IAM role assuming another IAM role with admin privileges to access another account
- An EC2 instance assuming an IAM role with admin privileges to access another account
- An IAM user assuming an IAM role with admin privileges to access another account
In the following screenshot, Cloud Security flagged risky entities that have the ability to assume another role, including an EC2 instance:
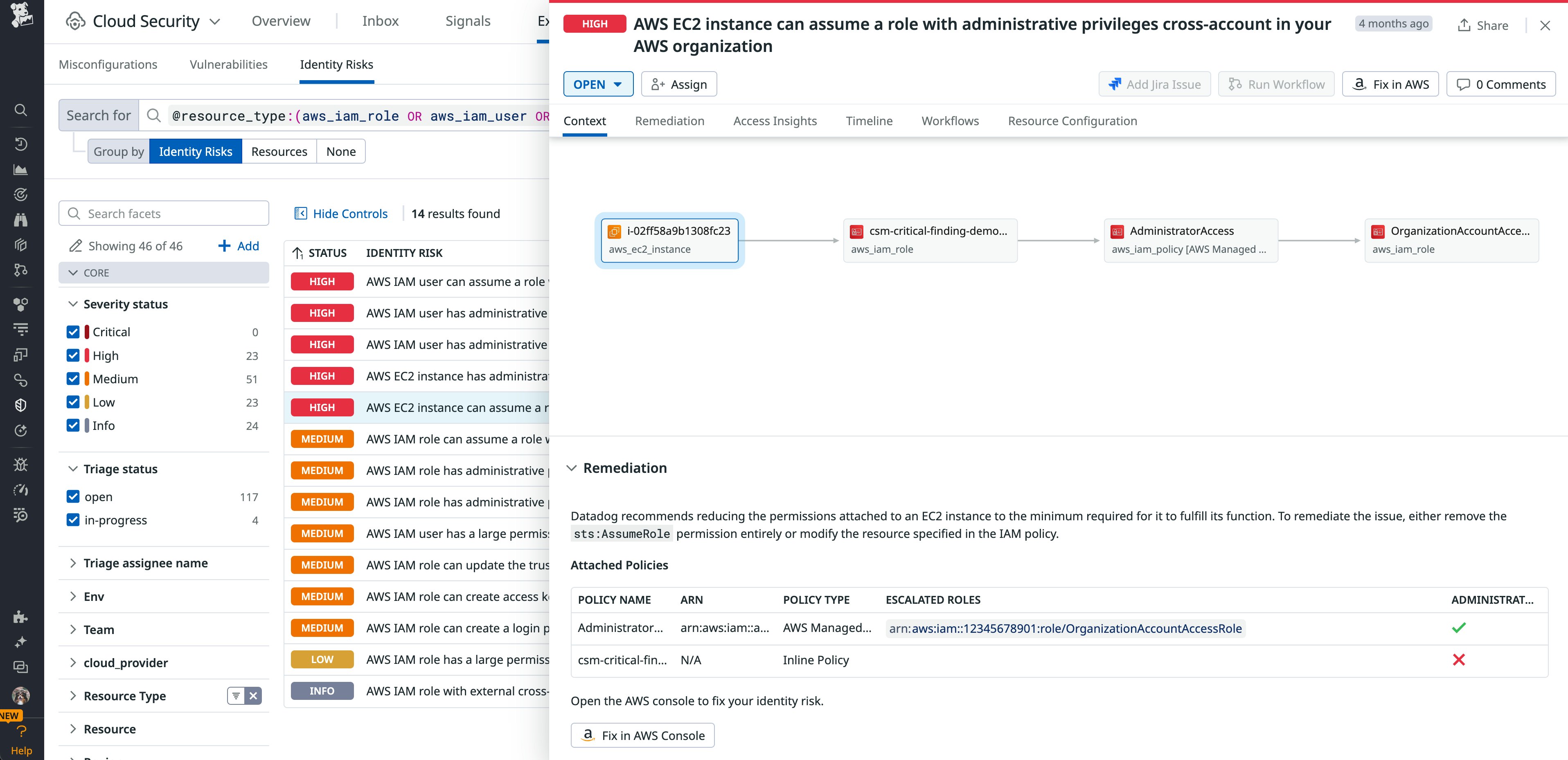
For any flagged issue, Cloud Security Identity Risks offers recommendations for adjusting affected access and permission policies, with the ability to navigate directly to your AWS Console. These capabilities enable you to efficiently safeguard your cloud identities and resources from attacks that take advantage of IAM misconfigurations.
Mitigate cross-account AWS IAM risks with Datadog
In this post, we looked at some of the common ways that attackers can take advantage of IAM misconfigurations in AWS environments and how they enable them to pivot from one account to another. We also looked at how Cloud Security Identity Risks automatically identifies these risks within your environment, giving you actionable insights for resolving them before an attacker takes advantage of them. Check out our documentation for more information about Cloud Security Identity Risks. Also, check out the AWS Security Blog to learn how to efficiently grant cross-account access. If you don’t already have a Datadog account, you can sign up for a free 14-day trial.