Addie Beach

Lauren Smith

Rajat Luthra
Reliable access to financial data is critical for organizations and individual consumers alike, making resiliency key for financial institutions responsible for managing this information.
While cloud computing can strengthen your app’s resiliency, it can also open up new security risks and require more complex continuity planning. Organizations and the companies that provide them services are increasingly being assessed on their risk management, business continuity planning, incident response and recovery, and cybersecurity measures, such as those specified under the Digital Operational Resilience Act (DORA).
Because there are so many aspects of digital preparedness, it can be challenging to make sure that every part of your stack is in compliance. Datadog monitors your entire system—including over 1,000 third-party integrations—and provides you with powerful, AI-enriched data correlation. This helps you evaluate potential risks within your system, so you can easily:
- Patch vulnerabilities and detect threats to your data
- Implement robust business continuity
- Respond to, remediate, and report issues
Patch vulnerabilities and detect threats to your data
Having a deep understanding of risk within your own system and your third-party services can help with addressing DORA concerns. In your system, you can achieve this by looking for vulnerabilities and developing a solid risk management plan, which often involves minimizing human error or malpractice through standardized best practices, quality assurance testing, and regular system audits. To analyze and mitigate risks from outside services, however, you need end-to-end visibility into potential weak points and proactive handling of unusual activity within your vendor portfolio.
With Datadog’s security features, you can easily access your app’s history of leaks and attacks, spot weaknesses with real-time threat detection, and use automated workflows to prevent future incidents. Datadog Security products also enable you to continuously scan your entire system, covering your containers, hosts, serverless functions, and APIs, to identify potential vulnerabilities, attacks, and identity risks. Additionally, the Datadog platform itself uses encryption and secure data handling practices.
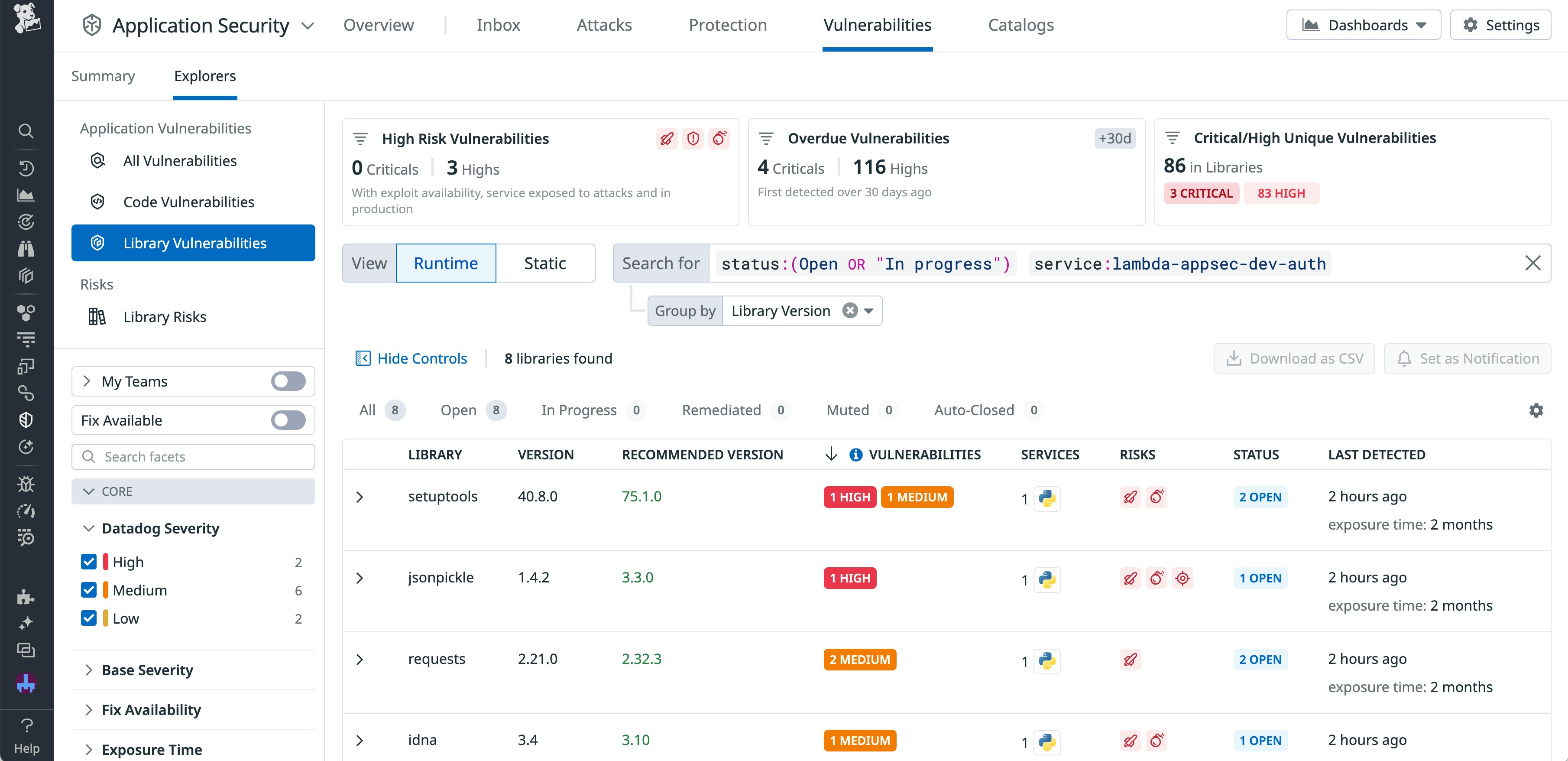
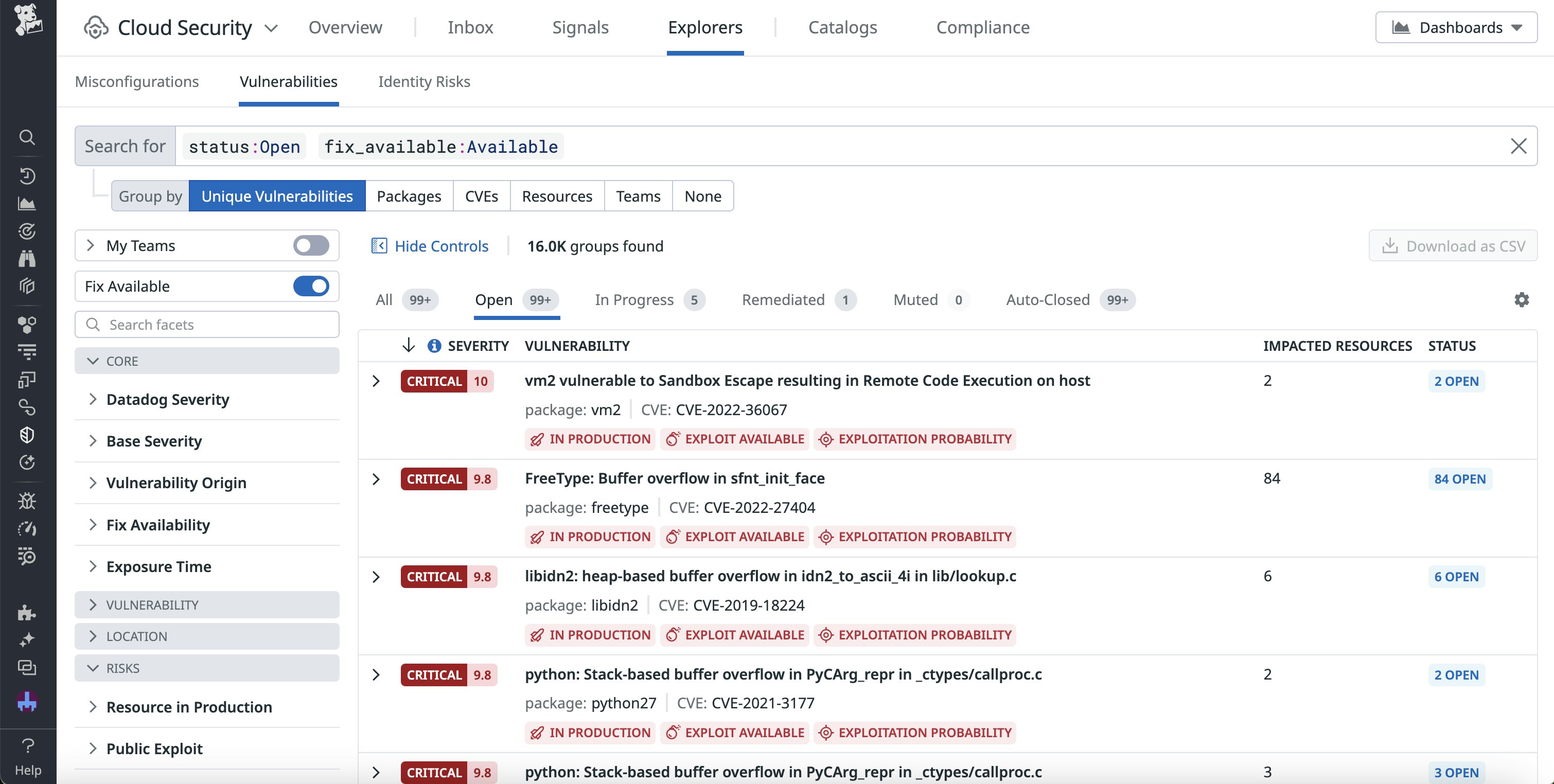
Let’s say you’re concerned about vulnerabilities in your AWS Lambda functions that handle financial transactions, especially within the third-party libraries that are used in concert with these functions. By enabling the Datadog AWS integration and Cloud Security, you can immediately begin collecting security data from your cloud environment. Potential risks in your serverless functions, containers, hosts, and their associated libraries—including misconfigurations and identity risks—are automatically cataloged in App and API Protection and Cloud Security. You can view these risks here and here, with the severity and number of impacted resources clearly identified for each issue. By clicking into a vulnerability, you can then access suggested remediation steps and context from the rest of your stack.
Implement robust business continuity
Of course, security incidents aren’t the only form of risk that threaten your system. Performance issues such as hardware failures or external outages and errors can also affect your customer’s ability to access their financial data. Business continuity planning prepares you for these issues by helping you determine which parts of your system are mission critical, what plans are in place to handle disruptions to these areas, and what kind of backups or workarounds are in place to ensure minimal user impact. Additionally, in-depth business continuity planning and monitoring helps you make sure that these issues have minimal impact on your customers, as well as spot and remediate smaller issues before they snowball into larger incidents.
Datadog Infrastructure Monitoring helps you evaluate the current and historical health of your hosts, containers, network devices, and serverless resources, so you can stay on top of developing issues and ensure that your backup systems are online. You can also use Application Performance Monitoring (APM) to identify performance, reliability, and security issues within your app, tracing them from the service level all the way down to individual lines of code. Crucially, APM enables you to map out dependencies throughout your app, showing you routes through which critical services may be impacted.
Let’s say you receive an alert that a database used for storing customer authentication information is experiencing a sudden spike in errors. By viewing the Service Map and selecting this database, you’re able to identify downstream services impacted, which include several other services crucial for login functionality. You can also see upstream services that may be contributing to the issue. This enables you to not just assess the scope of the incident and potentially reach a solution faster, but also better understand how and where you should be adding backups or workarounds to ensure better continuity of service in the future.
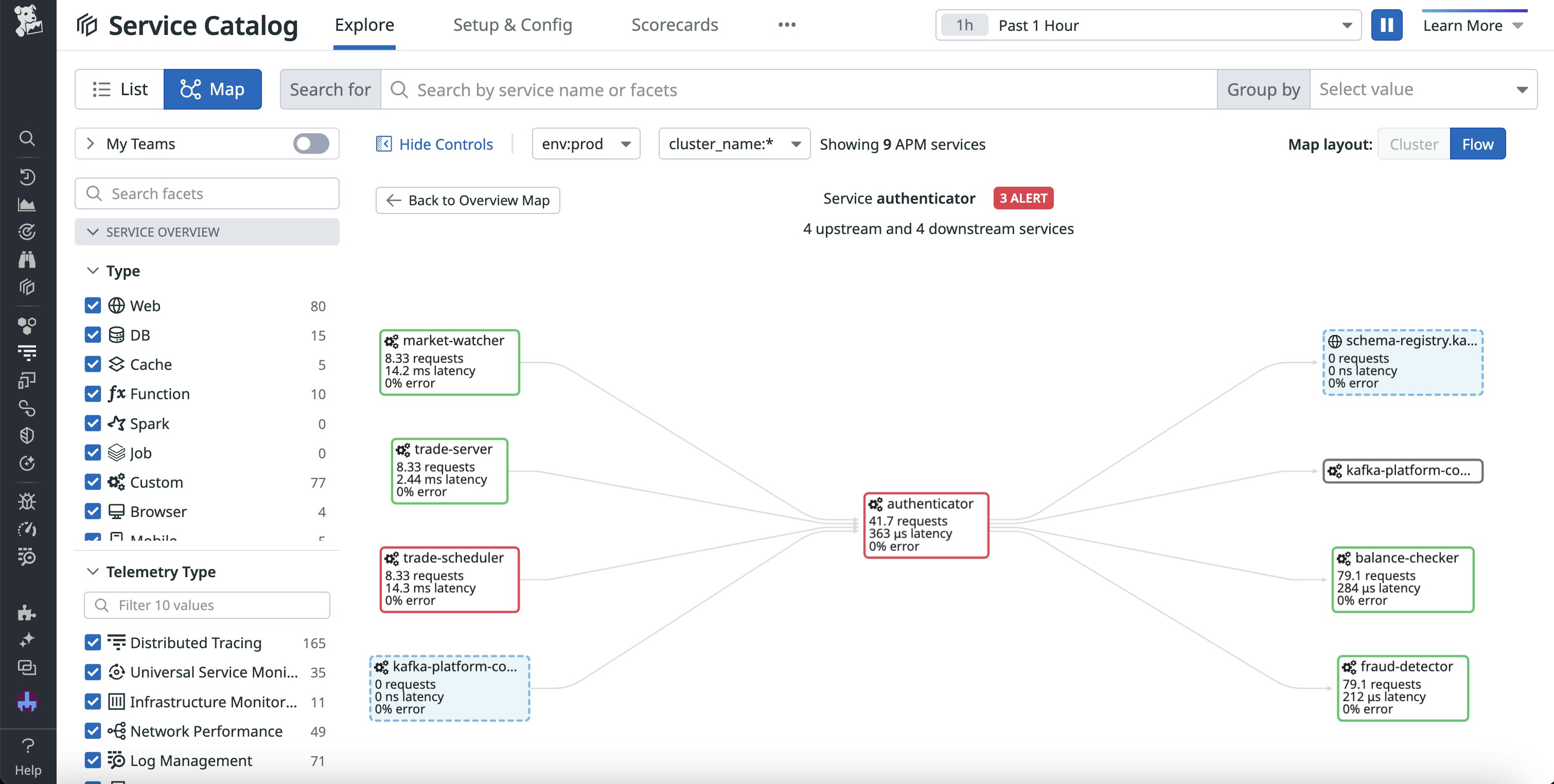
Respond, remediate, and report
In addition to ensuring that your system can respond to disruptions effectively, you may also need a clear plan for reporting these events to authorities under existing regulations. This could include providing accounts of incidents at three different points: an initial notification when the incident is detected, an update as the incident is being remediated, and an analysis once the incident is finished. Accurate reporting helps ensure that your organization has an effective plan for dealing with issues and enables consumers to better assess their own risk. Datadog Incident Management accelerates both your incident response and reporting efforts by giving you a single place to triage, organize, and document incidents.
Continuing the example from before, let’s say that the issues with your authentication database are preventing users from accessing their banking information. You decide to declare an incident to help you triage the issue and organize the relevant responders. Once the issue is resolved, you can easily link the postmortem to the incident overview page, which itself contains a record of when the incident started, who responded to it and how, and the number of customers who were impacted. This page then serves as a place to collect all incident activity and reporting for fast communication.
DORA can overlap with financial responsibility or data protection requirements. Cloud Security provides compliance frameworks that help you quickly evaluate how your security posture matches up against industry standards, so you can generate reports that identify critical security misconfigurations and other rule failures in your environments. Additionally, Sensitive Data Scanner prevents data leaks by proactively identifying and redacting sensitive data in your logs, traces, and events. Alongside Audit Trail, which gives you a more granular record of system activity, this can help you stay in compliance with additional regulations that apply to financial data.
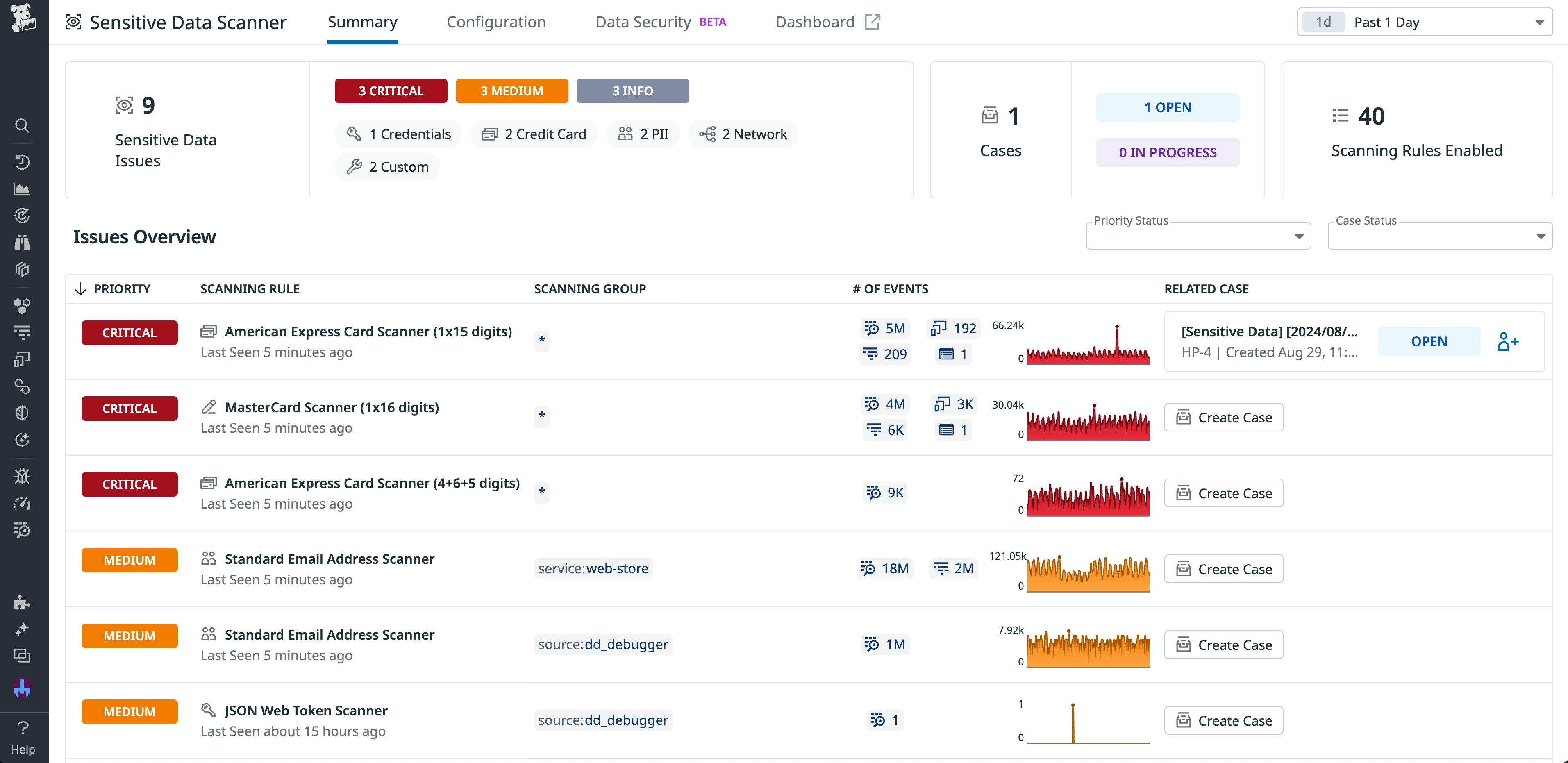
DORA and Datadog
By considering regulations like DORA, you can help ensure that your websites and apps are resilient enough to handle disruptions of any size so your customers can quickly access critical financial information whenever they need it. Datadog provides a number of features that help you mitigate risk across your entire stack, from your internal infrastructure and code to your third-party services.
You can get immediate support for DORA with Datadog Cloud Security’s compliance frameworks, which provide real-time visibility into misconfigurations in your cloud environment affecting your DORA compliance and include over 250 out-of-the-box rules mapped to DORA controls.
You can use our documentation to get started with Datadog Security, Infrastructure Monitoring, APM, Audit Trail, and Sensitive Data Scanner. If you’re not yet a Datadog user, you can try out these features by signing up for a 14-day free trial.