Vera Chan

Jason Hunsberger
Windows event logs are a key source of important information about your Windows environments, including detailed records of user activities, system performance, and potential security issues. However, with the sheer volume of logs modern environments generate, it can be overwhelming for security teams to efficiently detect, triage, and respond to threats in real time.
Datadog’s Windows event log integration enables you to ingest and process all of these events so you can analyze, generate metrics, and alert on them from a centralized platform. In this post, we’ll explore how you can then use Datadog Cloud SIEM to automatically detect suspicious Windows activity with out-of-the-box (OOTB) threat detection rules and gain an at-a-glance overview of threat activity with enhanced dashboards.
Centralize your Windows event logs
Datadog’s content pack for Windows event logs provides a unified starting point for monitoring your Windows environment by deploying threat detection rules and accessing customizable dashboards. Using the content pack, you can easily enable the integration and begin ingesting event logs. Datadog Log Management’s OOTB log-processing pipeline will automatically normalize and enrich these logs, allowing for efficient searching, and analysis at any scale. You can enrich them further with custom reference data for added context.
Detect threats with out-of-the-box detection rules
With threat detection rules, Datadog will continuously scan your Windows event logs for potentially malicious activity as it ingests and processes them. Create your own detection rules or use our built-in rules, which are aligned with the MITRE ATT&CK® framework. Next, we’ll look at some examples of the pre-configured detection rules that our security research team has built.
Detect Windows Domain Admins group changes
Detecting changes to the Windows Domain Admins group is critical for maintaining network security. Unauthorized modifications to this group can signal an attempt at privilege escalation, where an attacker gains elevated permissions to access sensitive systems and data. This detection rule helps organizations maintain a strong security posture, ensuring that any modifications to key administrative groups are legitimate and intentional. This proactive monitoring also assists in compliance efforts, as organizations need to maintain strict control over who has administrative access to their systems.
Detect PsExec execution
Detecting the use of PsExec is essential because it’s a popular tool used by both administrators for legitimate remote execution and also by attackers for lateral movement within compromised networks. PsExec allows execution of processes on remote systems, often without leaving traces, making it a favored tool in sophisticated attacks like ransomware or credential theft campaigns. Our security research team built this detection for teams to monitor for PsExecution and identify malicious use of the tool earlier in the attack chain.
By distinguishing between legitimate administrative use and unauthorized access, this rule offers critical context for security investigations. Early detection helps contain threats, reducing their ability to spread across the network and minimizing potential damage. It also safeguards infrastructure from the misuse of remote execution tools like PsExec. Additionally, this detection aids in post-incident analysis, providing valuable insights into how an attacker moved through your environment—crucial for strengthening defenses and refining response strategies.
In addition to these, other built-in detection rules include:
- Windows audit log clears
- Windows directory service restore mode password changes
- Multiple failed login attempts
- Suspicious named pipe is created
- Windows firewall is disabled
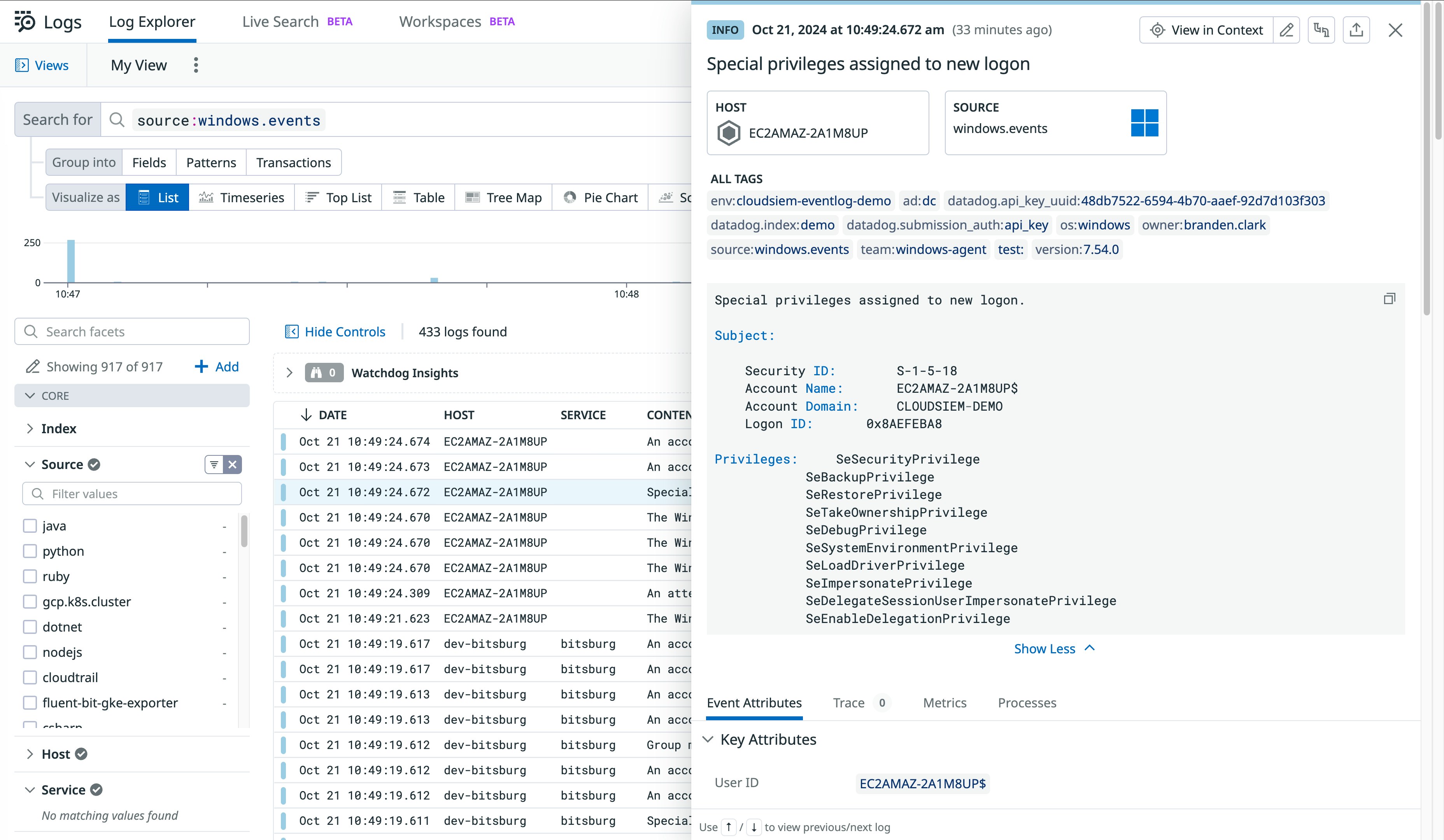
If Datadog detects any of this activity, it automatically generates a security signal that includes additional context around the issue, as well as actions and remediation steps. These signals are available from a unified explorer, enabling security teams to easily triage and prioritize issues across their environment.

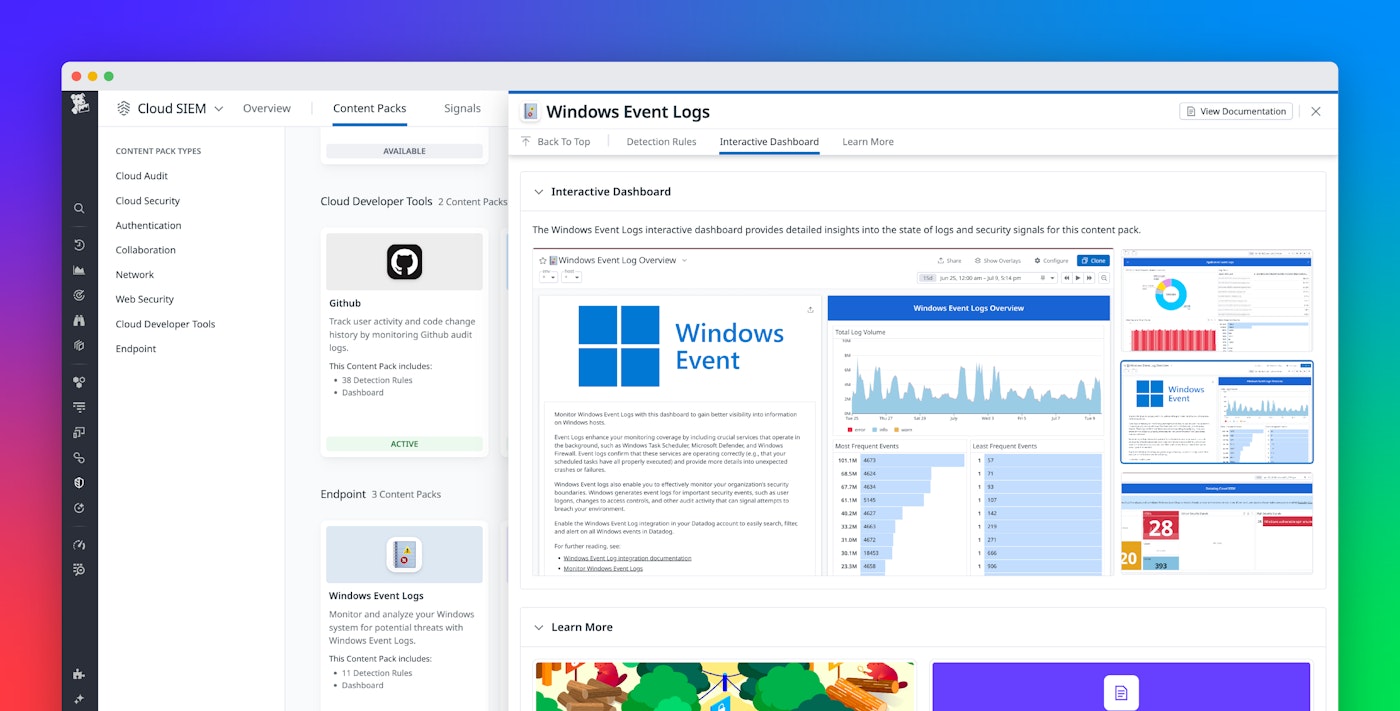
Visualize and track Windows event logs
Datadog’s customizable OOTB dashboard visualizes your Windows event logs to provide a high-level overview of activity across your environment. Widgets display key information including top lists of most frequent events and most common security, application, and system events along with which hosts are emitting them. For more comprehensive security coverage, Cloud SIEM customers also have access to a visual summary of how many detections Datadog has made within their environment, including a top list of the most critical security signals. You can easily pivot to related security signals in the Signal Explorer to investigate further.
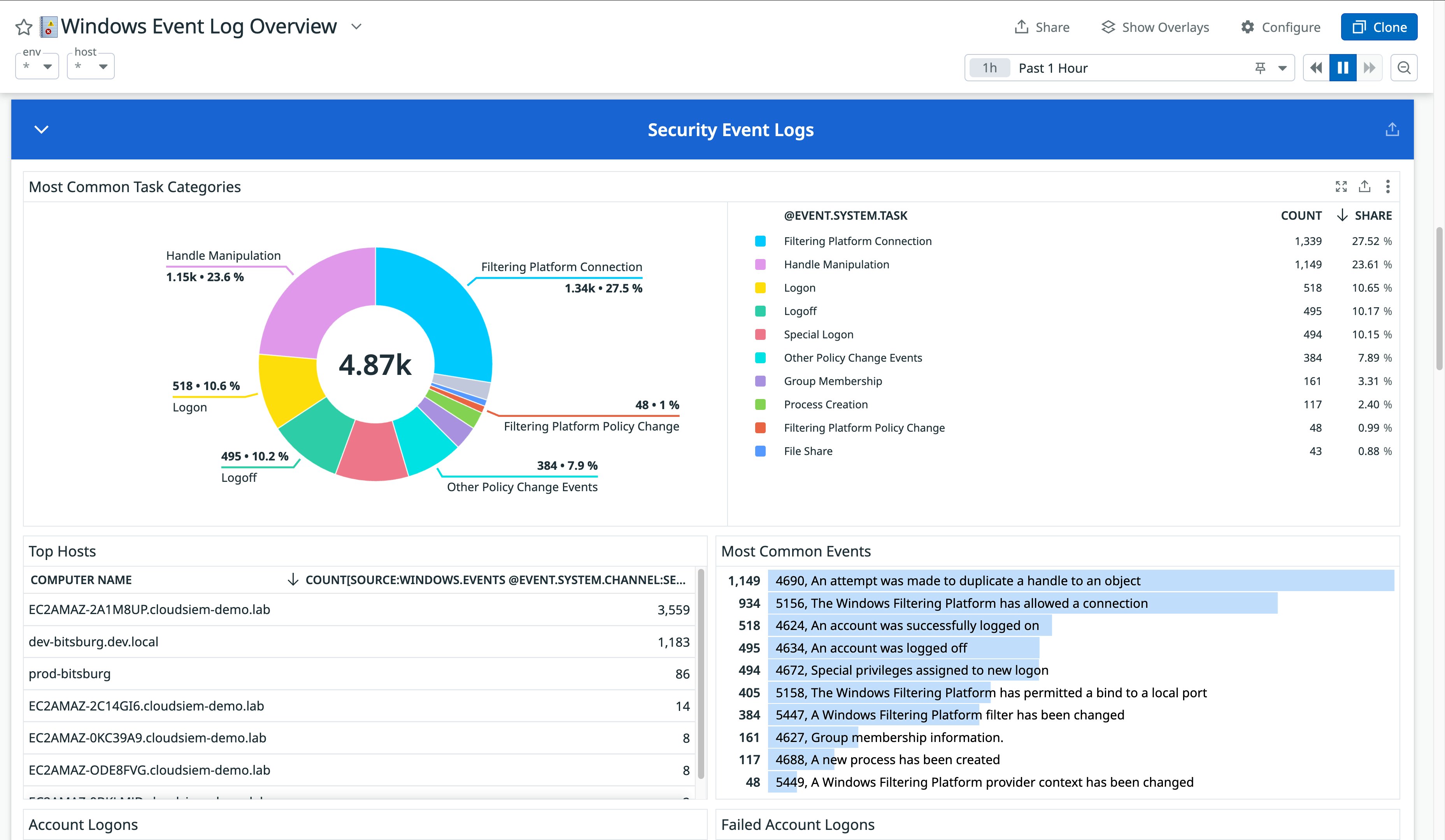
Get deeper security visibility into your Windows environment with Datadog Cloud SIEM
Monitoring Windows event logs is critical for identifying potential security threats across your Windows services. With OOTB detection rules and enhanced dashboard visualizations, Datadog Cloud SIEM helps teams get deep security visibility into their event logs so they can easily detect, triage, and respond to threats. Get started today with the Windows event logs content pack.
For more information, you can also view our documentation and get started with the content pack, or read more details on how to Monitor Windows event logs with Datadog. And if you’re not a customer, get started today with a 14-day free trial.