Datadog Security enables you to detect, prioritize, and respond to threats and vulnerabilities across your infrastructure and applications—whether they’re still in development or running in production. This year at DASH, we announced new capabilities and products to give you deeper security visibility across your stack. Enrich your Cloud SIEM signals with additional context from Cloud Security Management. Get real-time threat detection for AWS Fargate and Windows-based environments. Identify and remediate code-level vulnerabilities with Datadog Code Security, and secure your APIs with Datadog Application Threat Management.
In this post, see these and other offerings to help you secure your infrastructure and applications. Then, check out our keynote roundup for more announcements, including:
- Agentless Scanning for Cloud Security Management
- Data Security
- One-click infrastructure-as-code remediation
- Datadog Code Security
- Supply chain risk reduction with Datadog SCA
- And more
Cloud SIEM
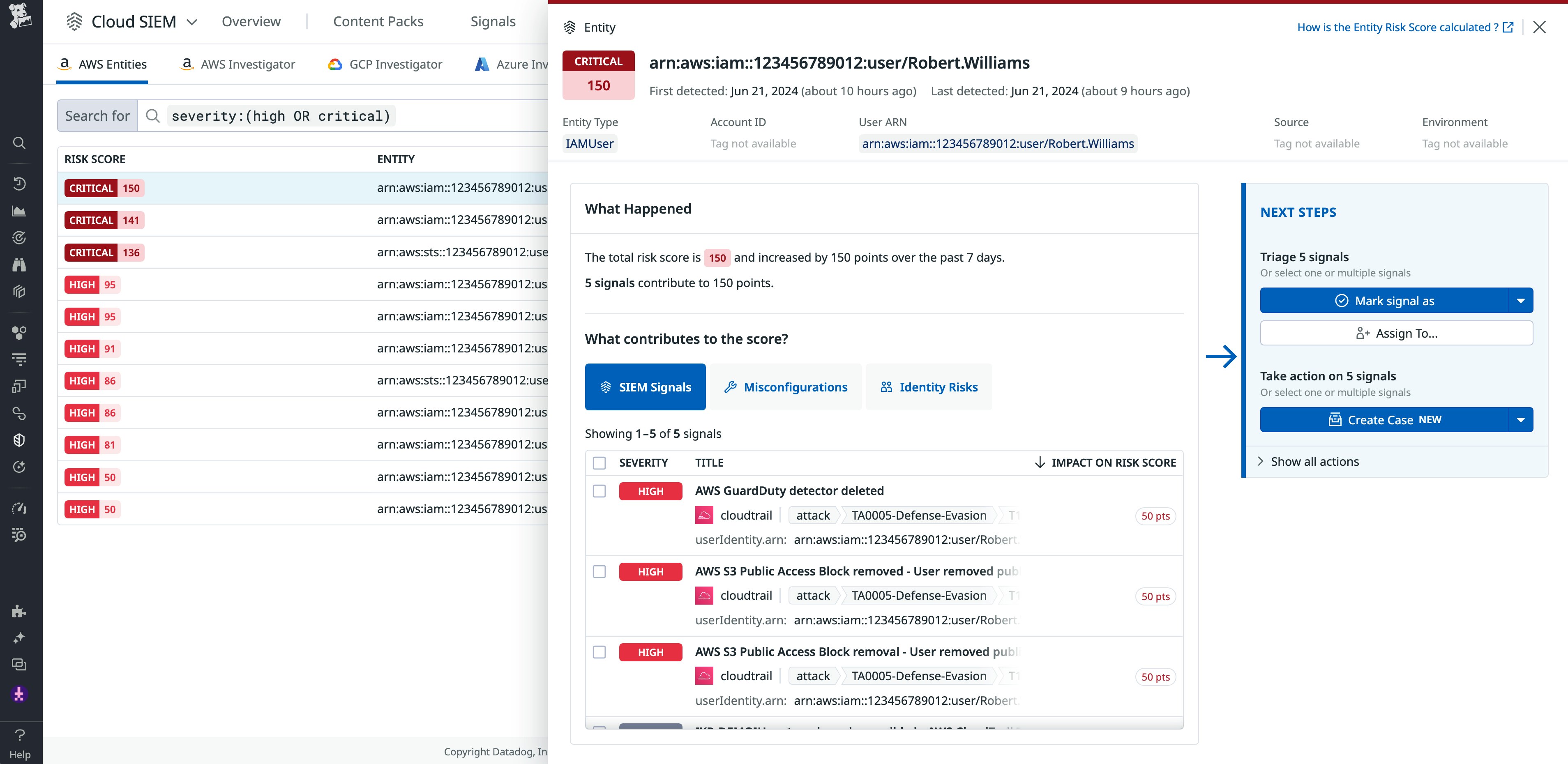
Accelerate investigations with Datadog Cloud SIEM Risk-based Insights and AWS Entity Analytics
Cloud SIEM Risk-based Insights for AWS Entity Analytics improves investigative efficiency for security teams by correlating Cloud SIEM signal context with insights from the Cloud Security Management product, such as misconfigurations, identity risks, and existing configuration risks that could potentially escalate threats. Security analysts can view a heuristic risk score associated with each entity generated by an opinionated risk model to prioritize their investigations.
Learn more in our blog post.
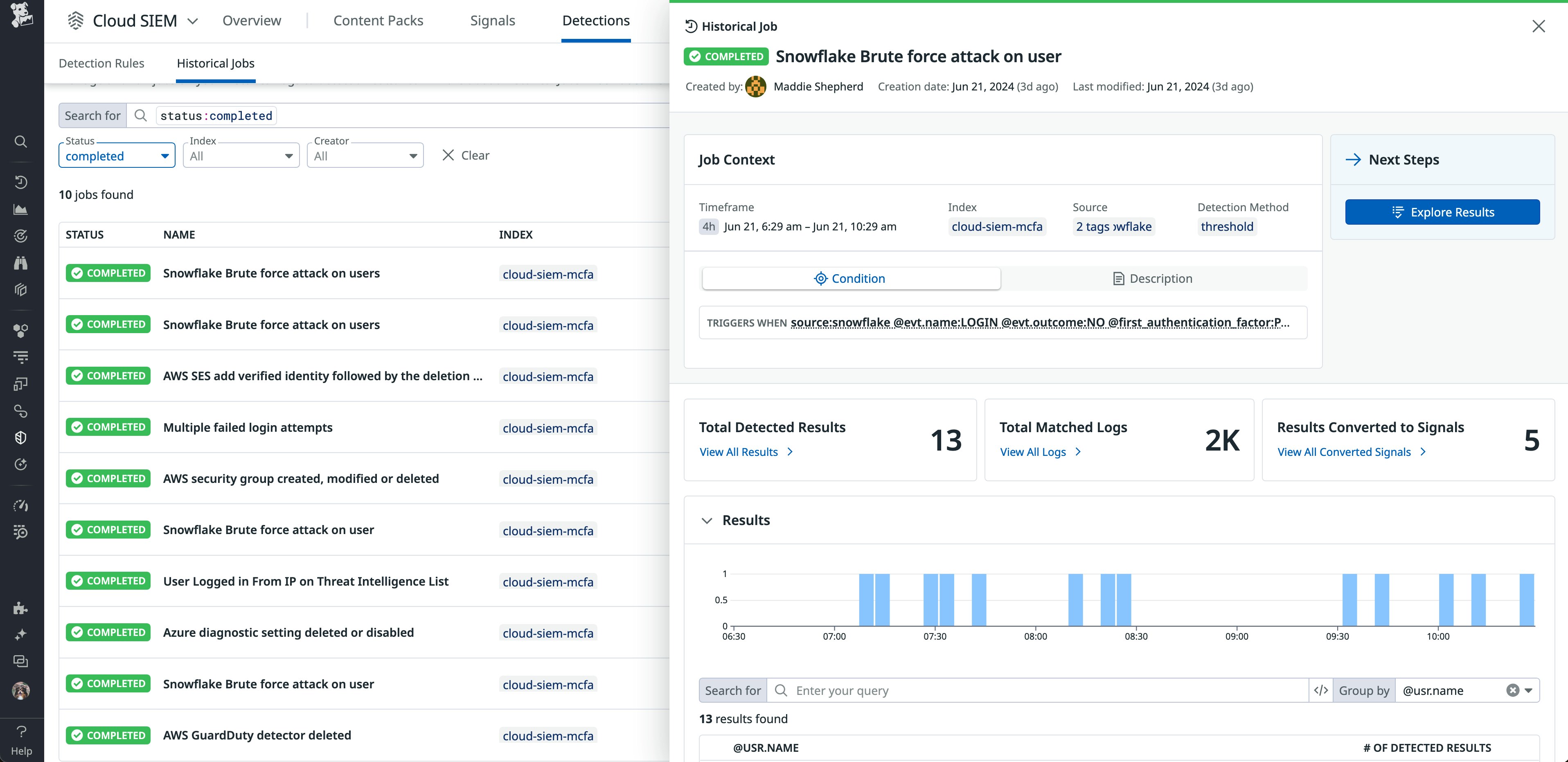
Backtest detection rules with Datadog Cloud SIEM Historical Jobs
Security teams need to quickly identify new anomalies and attacks, uncover suspicious behavior, and conduct threat campaigns to detect malicious activity from emerging threat actors, techniques, or vulnerabilities. To do this, they must craft complex, advanced detection rules to identify sophisticated attacks effectively. They also require a way to test these detection rules prior to releasing them to production to minimize false positives and reduce burnout.
Datadog Cloud SIEM tackles these challenges by extending its real-time detection engine with a historical detection engine, enabling analytics on historical logs. This solution allows for:
- Proactive threat detection rule testing with historical jobs before deployment
- Enhanced threat investigation and identification through threat hunting
- Flexible log manipulation and the creation of complex detection rules using advanced query operators
Learn more in the blog post.
Cloud Security Management
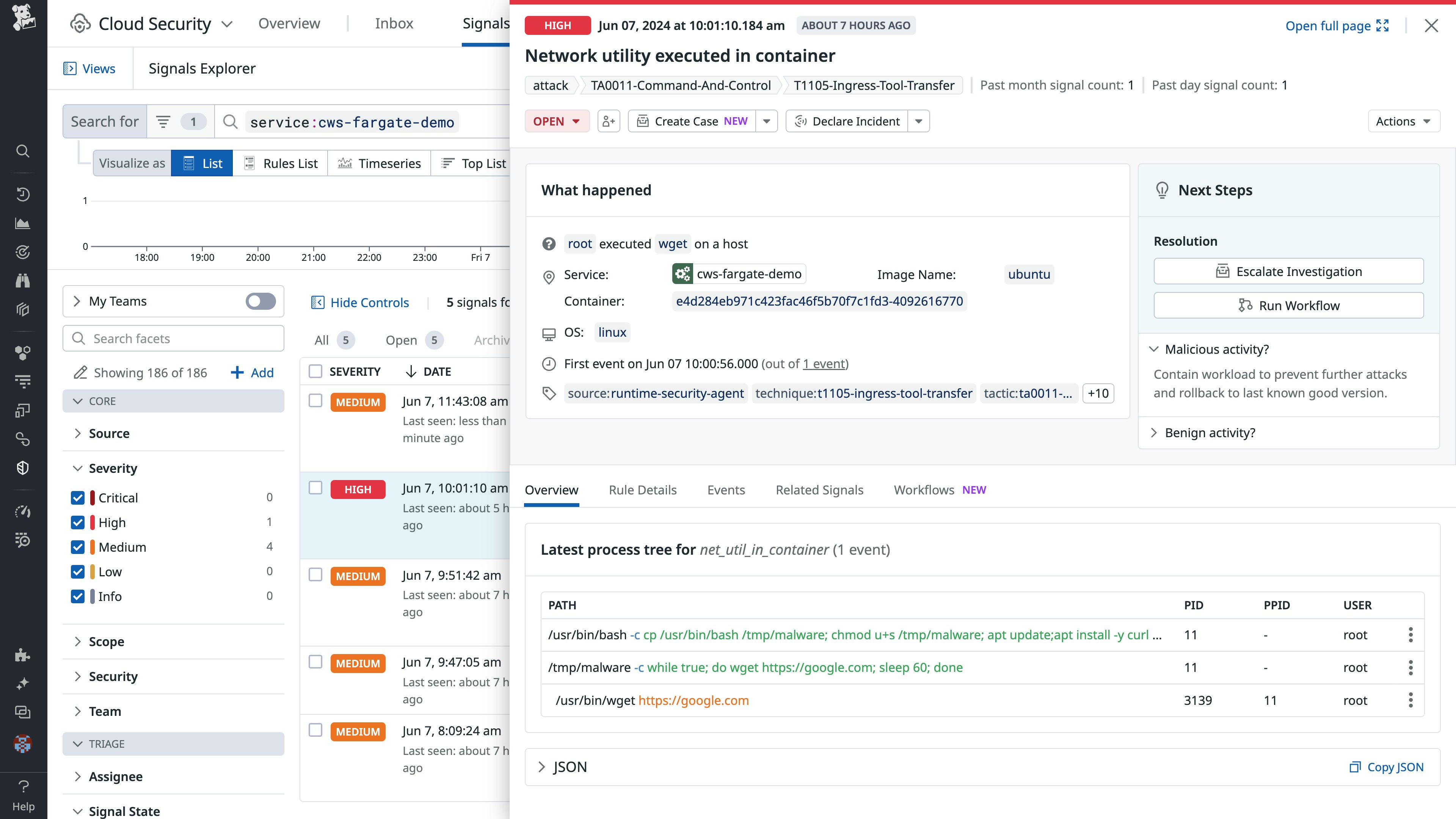
Get real-time threat detection for AWS Fargate ECS and EKS environments
Although AWS Fargate removes the need to manage underlying servers and clusters, it can introduce sophisticated security challenges. With Datadog Cloud Security Management (CSM) support for AWS Fargate for ECS and EKS, customers can now monitor for suspicious process and file integrity monitoring (FIM) activity, such as the execution of a network utility in a container or file permission changes. When a security signal is created, CSM automatically correlates it with observability data, providing the necessary context to quickly investigate and remediate threats. Learn more in our blog.
Get real-time threat detection for Windows environments
Datadog’s Cloud Security Management (CSM) now delivers comprehensive runtime threat detection for Windows environments. With CSM for Windows, security teams can monitor for suspicious file, process, and network activity on Windows Server 2016 and newer, and automatically correlate security risks with observability context for accelerated investigations. Check out our blog to learn more about how CSM for Windows workloads can strengthen organizational security posture and help security teams respond to threats more effectively.
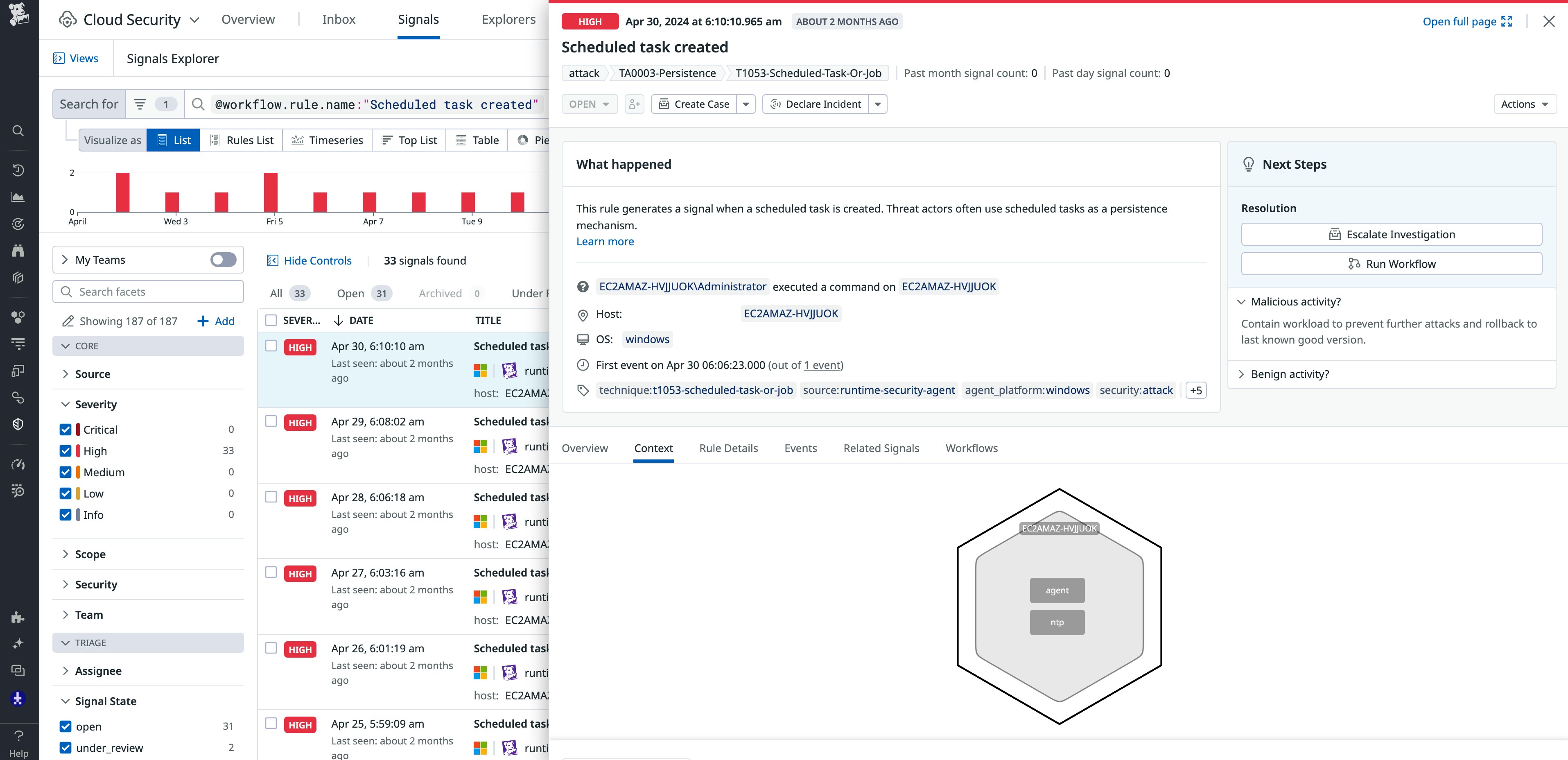
Continuously scan for vulnerabilities on Windows hosts
Datadog Cloud Security Management (CSM) now offers continuous vulnerability scanning for Windows hosts in public beta. With CSM Vulnerability Management, development, operations, and security teams can collaborate to quickly detect, prioritize, and remediate vulnerabilities across their containers, container images, hosts, and host images. CSM Vulnerability Management for Windows hosts is now in public beta. See our documentation to get started.
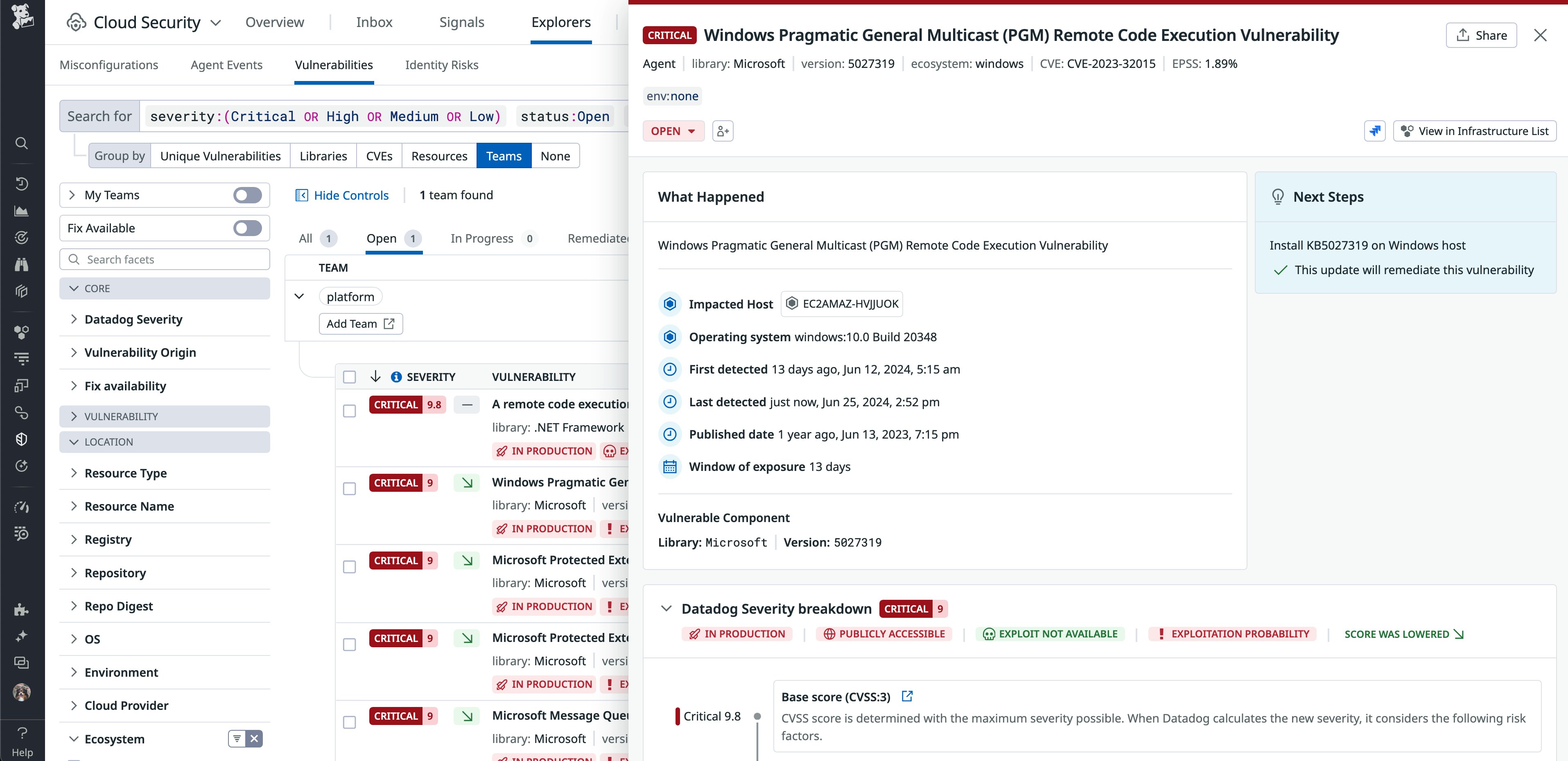
Review security posture at a glance with the out-of-the-box CSM Vulnerability Management dashboard
With Datadog’s new out-of-the-box CSM Vulnerability Management dashboard, security teams and operations leaders can now review their security posture at a glance and identify which teams need support to remediate their vulnerabilities. Customize the dashboard to easily report progress to stakeholders across your organization.
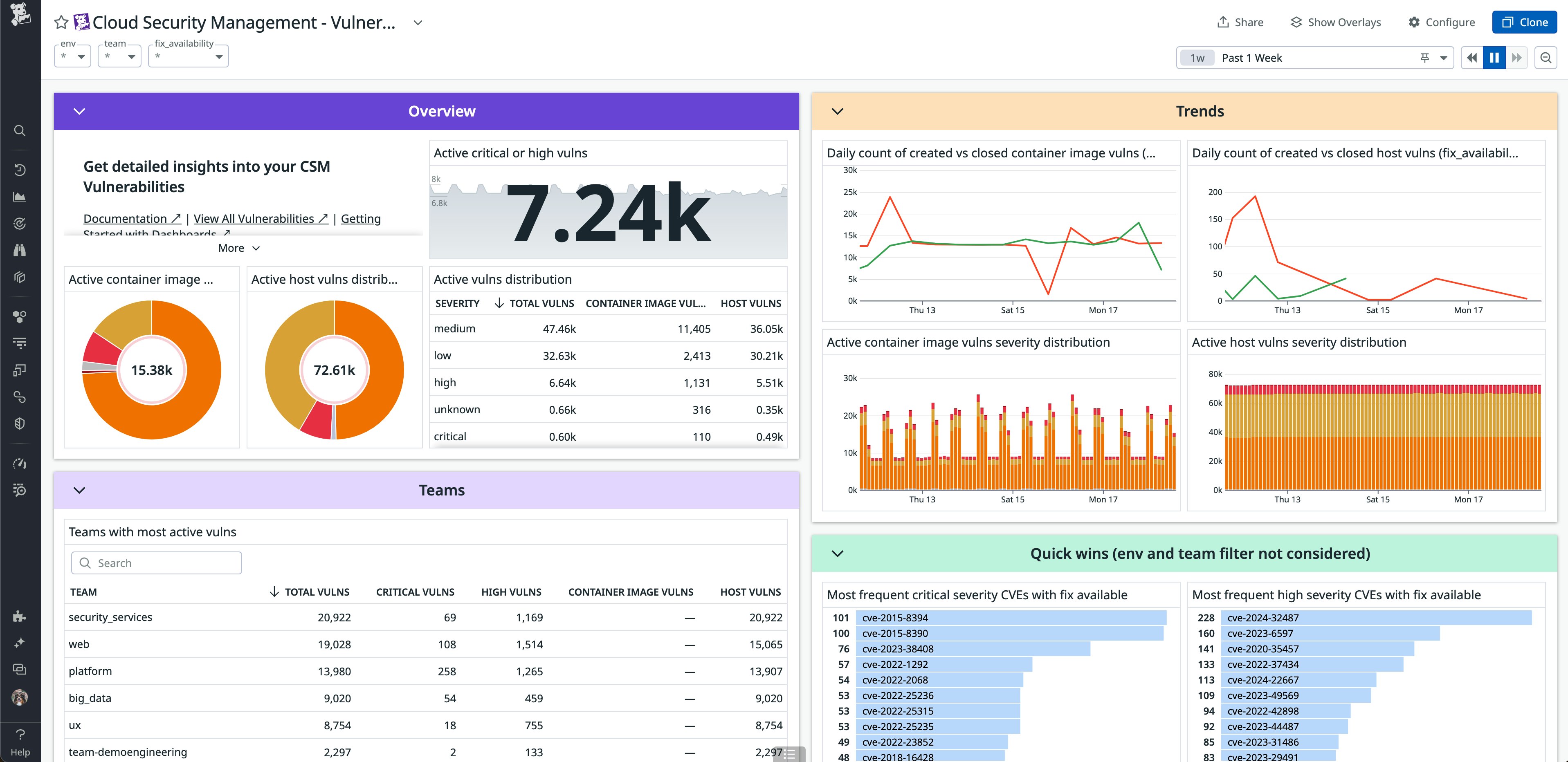
Find and remediate identity risks in your Azure and Google Cloud environments with Datadog CIEM
As part of Cloud Security Management, Datadog Cloud Infrastructure Entitlement Management (CIEM) helps organizations proactively remediate IAM risks across their infrastructure. Now, in addition to AWS, Datadog CIEM supports Azure and Google Cloud resources. It detects direct and indirect privileged access, excessive permissions, large blast radii, and more. It also helps remediate these issues with suggested downsized policies, one-click Infrastructure-as-Code (IaC) remediation, Datadog Workflows, and direct access to cloud consoles. Read more about Datadog CIEM in our blog post and see our documentation.
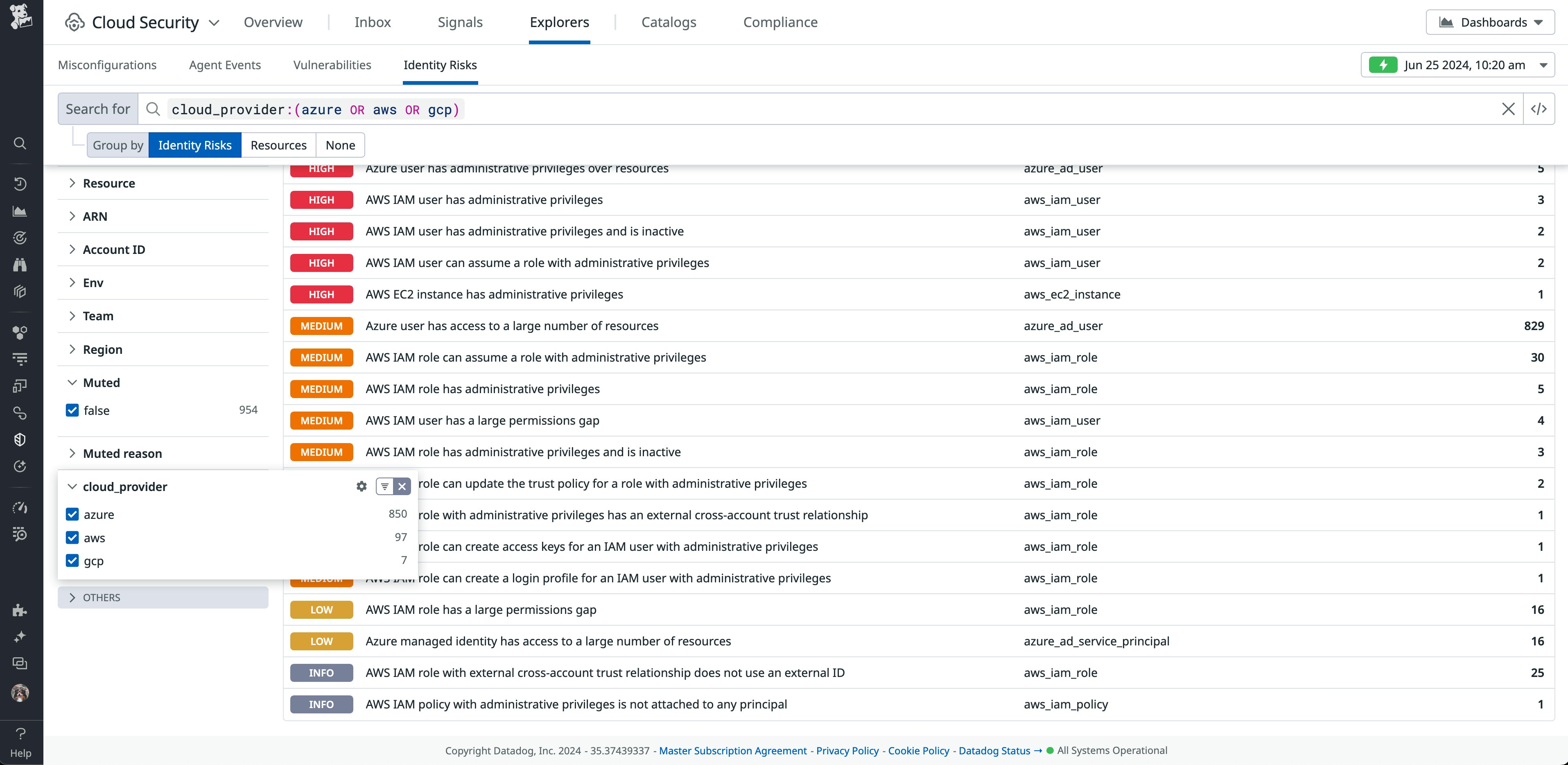
Identify and remediate permission gaps in AWS with Datadog CIEM and AWS IAM Access Analyzer
AWS IAM Access Analyzer helps organizations find overprivileged resources in their AWS environments, so they can detect and remediate excessive access to critical cloud resources—one of the most common vulnerabilities and the root of many data breaches. Datadog Datadog Cloud Infrastructure Entitlement Management (CIEM) now integrates directly with AWS IAM Access Analyzer, so you can see these findings right in your Datadog UI, alongside other identity risks across your infrastructure. Once it identifies accounts that have been granted permissions they are not using, Datadog CIEM will suggest downsized policies to limit unnecessary access, and you can pivot directly to AWS IAM Access Analyzer to take further actions there. Check out our blog post about the integration to learn more.
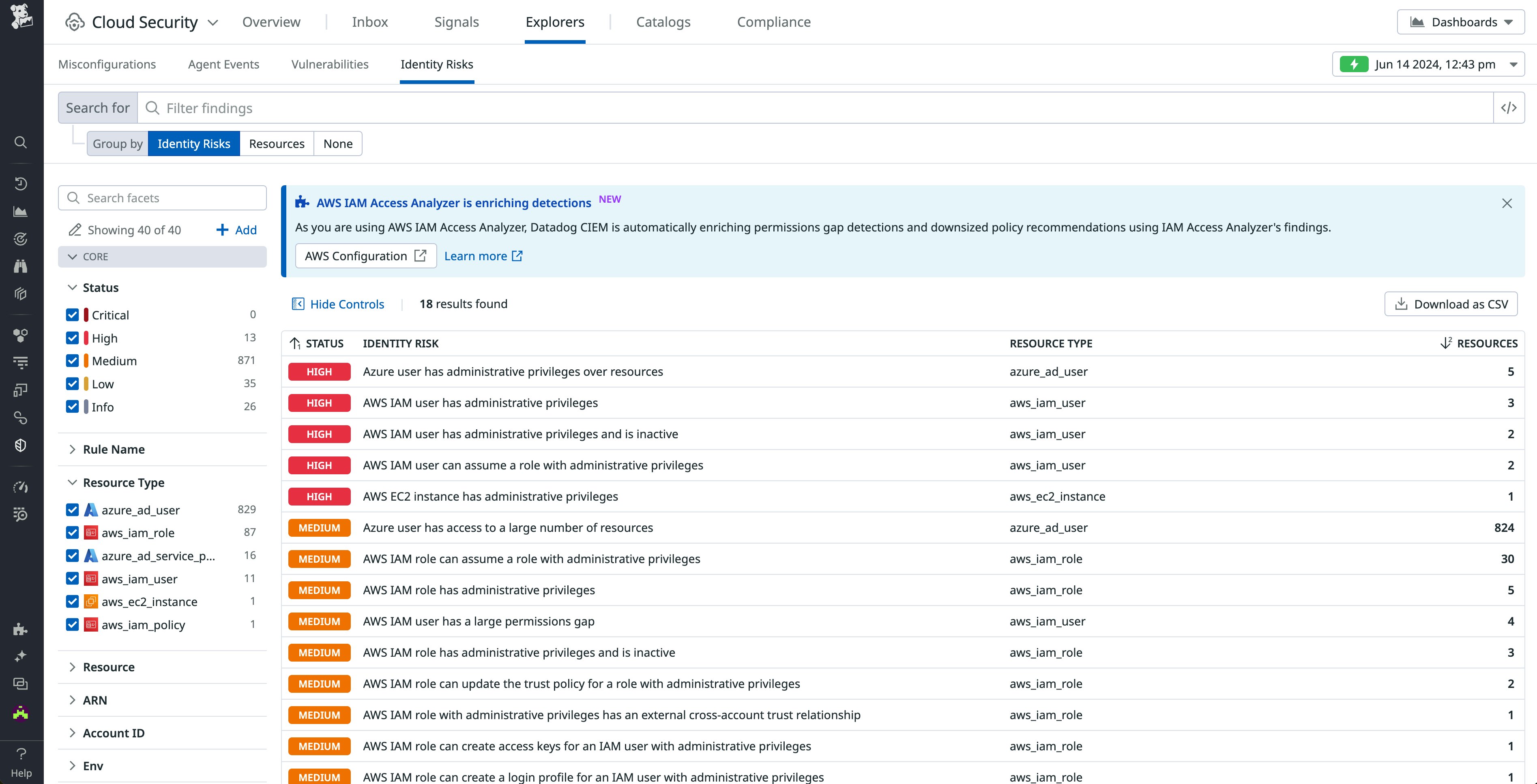
Identify and stop unauthorized cryptomining with Datadog Cloud Security Management
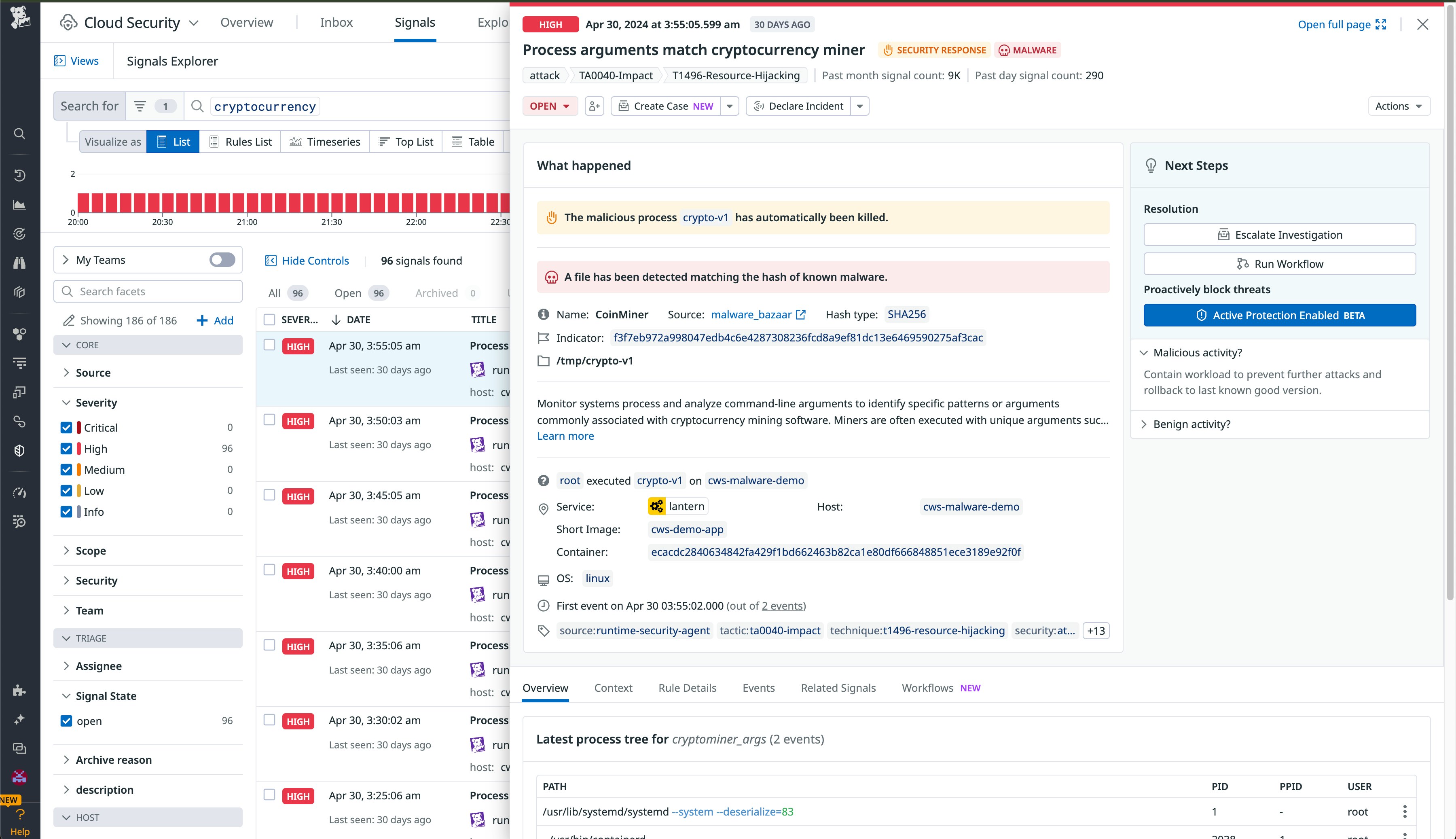
Cloud environments face an increasing number of cyberattacks, making security a top priority—especially against undetected cryptomining, which can quickly escalate costs and degrade performance. Datadog Cloud Security Management (CSM) Threats enables teams to proactively identify and stop unauthorized cryptomining on cloud workloads by using Agent rules that monitor processes and automatically stop malicious mining activities. Detailed signals and context help teams swiftly quarantine affected resources and address vulnerabilities. With advanced detection capabilities, Datadog CSM Threats allows DevOps and security teams to collaboratively own their environment’s security, smoothing the DevSecOps transition. Read our blog post to learn more and visit the Agent Configuration page to enable protection.
Application Security Management
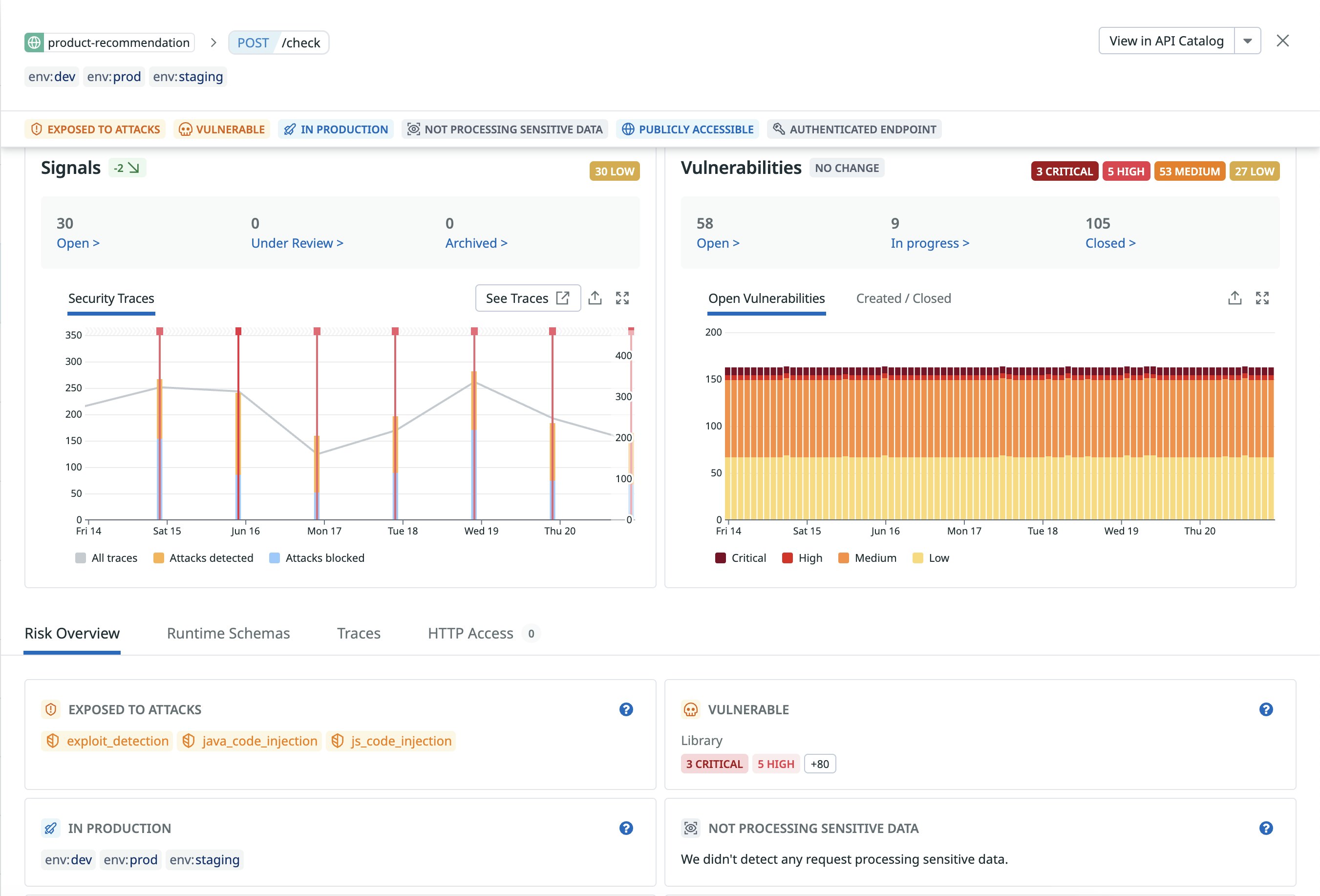
Secure your APIs with Datadog Application Threat Management
Identifying which APIs are running in production, assessing their security risks, ensuring proper authentication and authorization methods, and defending them against attacks are all highly complex tasks. Datadog Application Threat Management has added API security capabilities to help you:
- Secure a wider range of APIs with added support of GraphQL (Node, Go) and gRPC (Java, go) APIs
- Continuously inventory API risks that cover authentication methods, exposure of sensitive data and private endpoints to the internet, and the use of vulnerable third-party libraries
- Identify and protect API endpoints against top 10 OWASP API attacks and business logic attacks that include account takeovers
See our documentation to get started with Datadog Application Threat Management’s API security features.
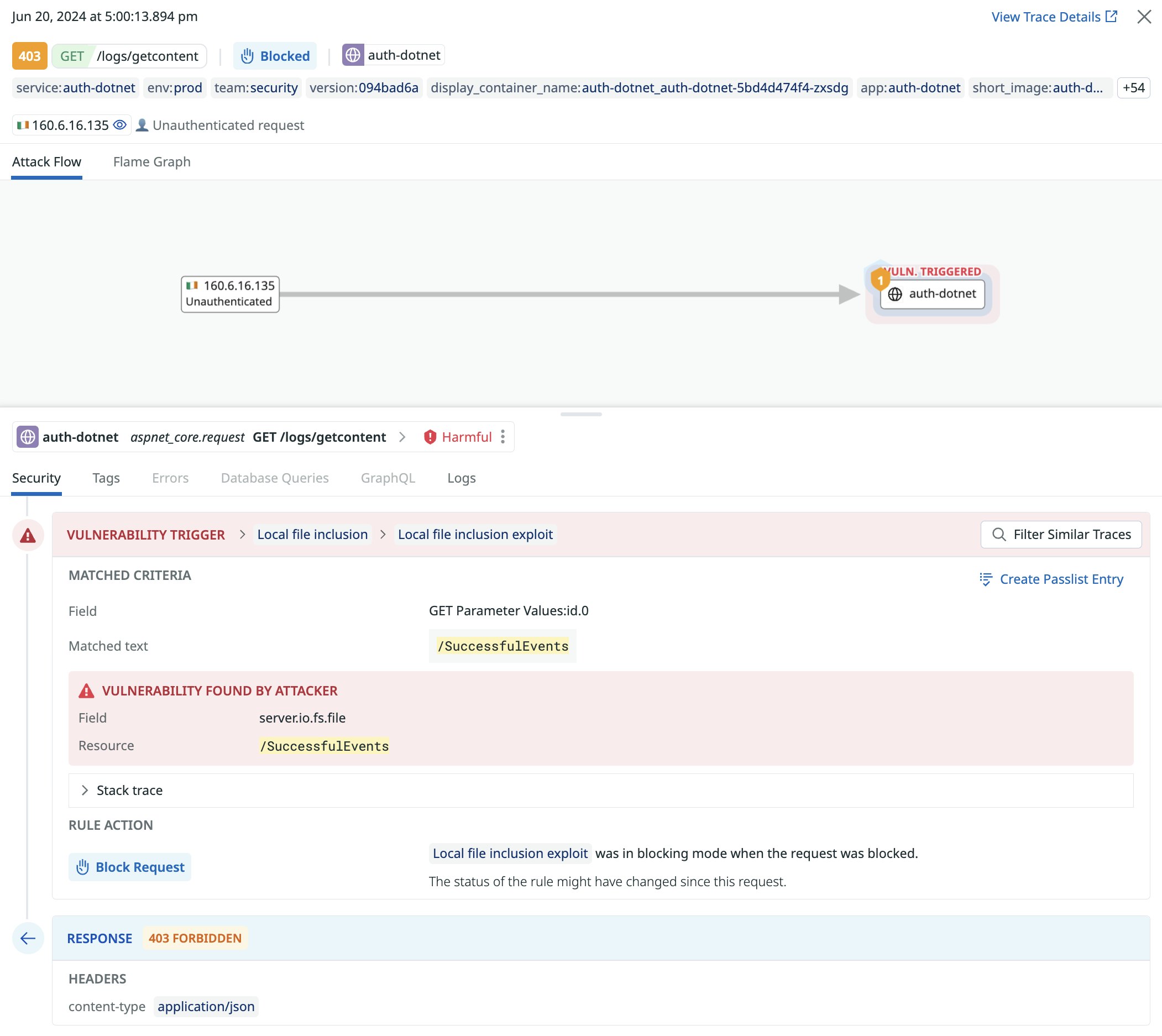
Proactively protect your applications from vulnerabilities with Exploit Prevention
Exploit Prevention within Datadog Application Threat Management enables customers to take a proactive stance against known and zero-day vulnerabilities. Exploit Prevention uses a runtime application self-protection (RASP) approach to detect and block exploits within monitored applications. This capability combines telemetry from the Datadog tracer with predefined heuristics to detect and block defined categories of exploits without impacting legitimate traffic. For example, in case of a local file inclusion attack, ASM Exploit Prevention inspects all file access attempts in order to ascertain if the path has been injected and whether a restricted file is being accessed, and then makes a block decision. Visit the Exploit Prevention documentation to learn more and get started.
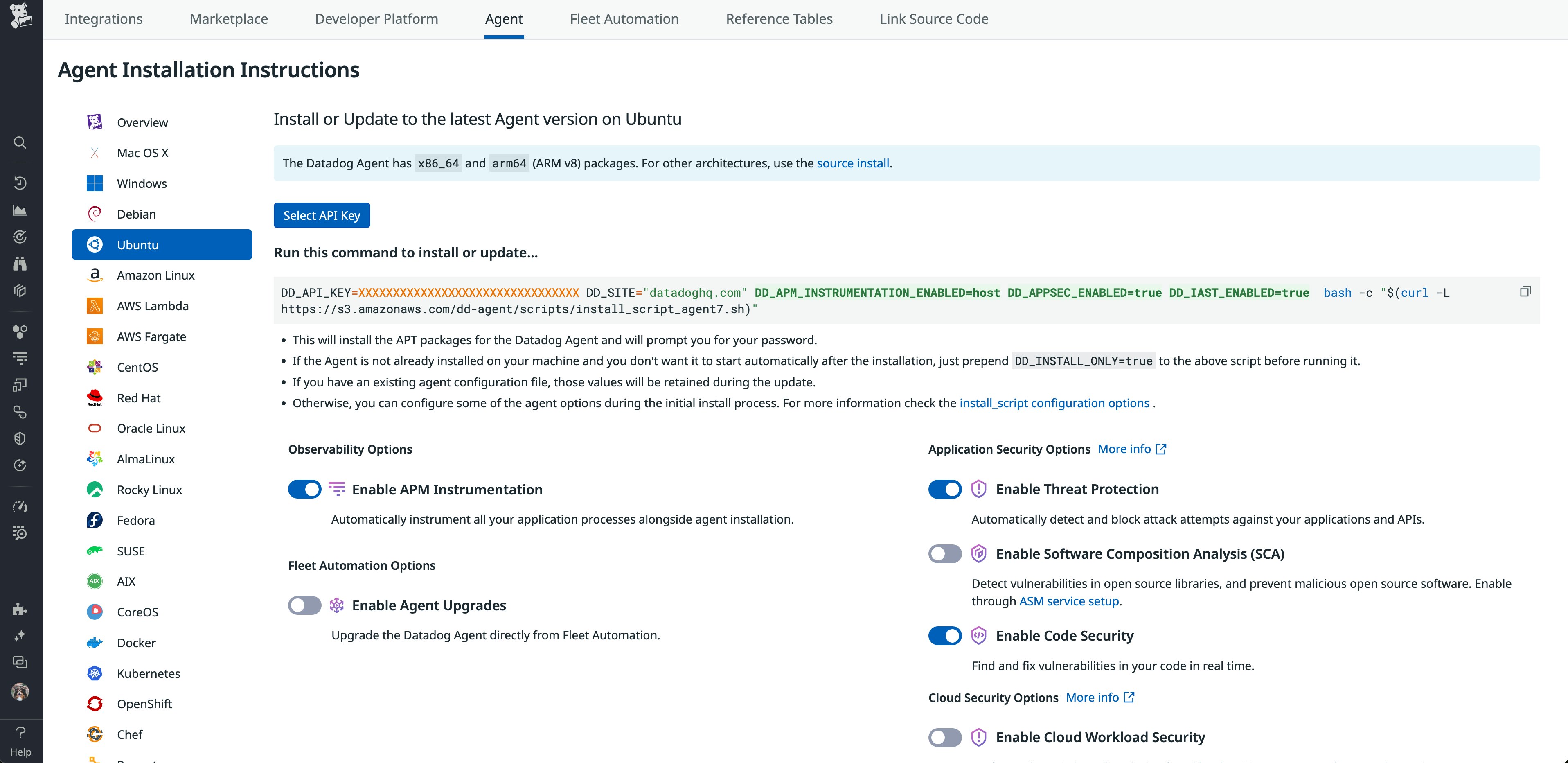
Enable Application Security Management without manual instrumentation with Single Step Instrumentation
Datadog Single Step Instrumentation enables you to instrument your services in minutes at the same time you install the Datadog Agent. Now, you can enable and deploy Datadog Application Security Management to your services using Single Step Instrumentation. Detect and remediate threats and vulnerabilities across your applications and APIs with minimal manual configuration and without needing to deploy the Datadog trace. See our documentation to get started.