Partha Naidu
As organizations increase the size of their cloud footprint and the complexity of their applications, they face challenges securing their infrastructure and services. Security breaches often go undetected for months, giving attackers time to do extensive harm. Once organizations become aware of a breach, they may no longer have access to the logs that comprise a complete history of the attack, because the time span easily exceeds their log retention window. This prevents teams from answering critical questions about the source, vector, and duration of the attack. And even when organizations do have access to logs, it can be challenging to detect patterns in large volumes of log data to gain the insight necessary to contain and remediate the incident.
In this post, we’ll show you how you can use Datadog Cloud SIEM Investigator to conduct historical security investigations that enable you to understand the scope and impact of an attack, regardless of how long ago it occurred.
We’ll show you how you can:
- Visualize logs to investigate an attack
- Find patterns and context in related Security Signals
- Manage attacks and mitigate risks with Workflow Automation
Visualize security logs to understand the scope of an attack
Cloud SIEM Investigator enables you to visualize logs that provide the full history of a security incident. Datadog gives you a cost-effective way to store a deep history of logs, and now you can visualize those logs to see the course and impact of a security breach—even if it began long ago. For example, if your organization discovers a data leak, you can use Cloud SIEM Investigator to inspect logs over a long time span, and look back on progressively older logs to identify the first signs of the breach.
Filtering the Cloud SIEM Investigator view enables you to isolate relevant records that can help uncover an attacker’s trail. For example, you can filter to highlight suspicious users or accounts, or see which services an attacker interacted with and the results of those interactions—i.e., whether an attacker’s requests to the service were allowed or denied. This can help you understand the methods employed by the attacker. If you see that a user tries but fails to update the metadata on a large number of Amazon EC2 instances, you might suspect that this user is a malicious actor attempting to gain a foothold inside your AWS environment.
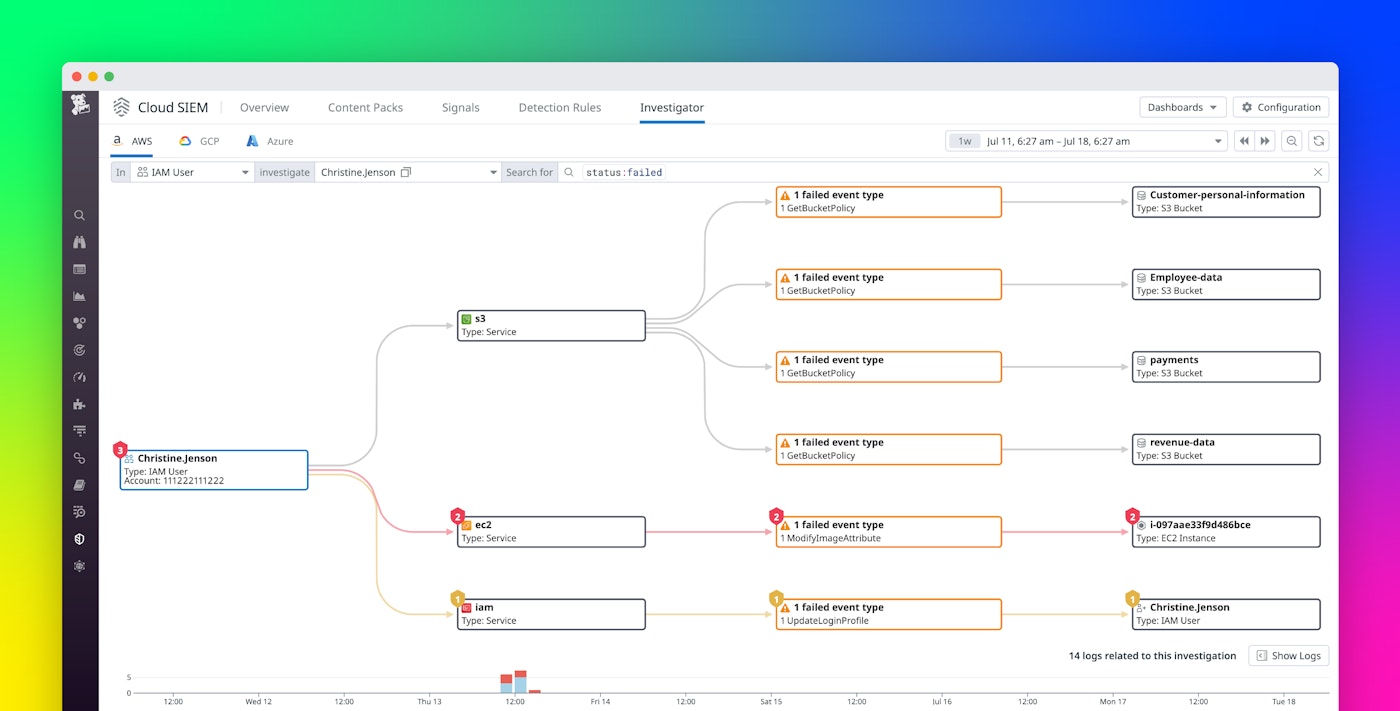
In the screenshot below, Cloud SIEM Investigator visualizes AWS CloudTrail logs to show that a single IAM user made requests to the Amazon S3 service. The timeline at the bottom of the page shows that the user has interacted with this service over several days, and a significant portion of those requests generated errors. Following the path of the user’s S3 activity, we can see that they were able to list S3 buckets, which provided them with knowledge of the organization’s infrastructure. We can also see that the user tried but failed to access the bucket policy of the customer-data bucket. This might have been an attempt to identify a bucket with lax access controls and could suggest the start of an attack.

Build context for your investigation with Security Signals
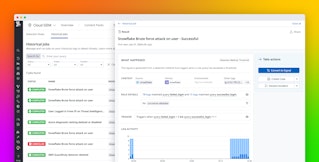
To gain context around a suspected attack, you can easily pivot from Cloud SIEM Investigator to see Security Signals related to any identities (such as accounts or users) or cloud services you think may be involved. Datadog Cloud SIEM monitors your security logs to detect risks and generates a Security Signal if any of your detection rules are violated, which could indicate that you are under attack. The screenshot below shows how you can navigate from Cloud SIEM Investigator to see Security Signals related to an IAM user you suspect is a malicious actor.

You can use Security Signal data to focus and accelerate your investigation, quickly confirm whether you’re under attack, and even see the method of attack. In the screenshot below, the side panel shows a Security Signal attributed to a suspicious IAM user and indicates that they tried to exfiltrate an AMI to make an EC2 image available to unauthorized users. This signal has been generated eight times in the last month, indicating that an attacker is making a repeated effort to find and exploit a vulnerability. You can explore other Security Signals to get a fuller picture of the attacker’s mode of operation—for example, you may discover that they used privilege escalation, a compromised access key, or brute force as an initial step in the attack.

Manage attacks and mitigate risks with Workflow Automation
If you’ve detected an ongoing attack, you want to react quickly to apply any remediation steps you’ve defined, such as locking compromised user accounts or rotating access keys. Datadog Workflow Automation lets you automate actions like these to quickly respond to a breach, and you can use Blueprints to easily create workflows to simplify and speed up your response.
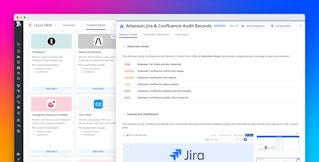
For example, the Blueprint shown below lets you create a workflow to quickly suspend an Okta user account. When the workflow is triggered, it sends a Slack message alerting responders and asking them to confirm that the user should be suspended (or, alternatively, to identify the issue as a false positive and take no further action).

A workflow like this can help teams accelerate their response when their security investigation leads them to believe that a user presents a threat. If a Security Signal indicates a threat for which you’ve automated a response, you can immediately trigger that workflow to contain the attack. Simply click the Run Workflow button in the side panel in Cloud SIEM Investigator, and then choose the workflow you want to run.

Understand and manage attacks with Cloud SIEM Investigator
Cloud SIEM Investigator gives you a powerful tool to ensure the security of your business-critical applications by enabling you to conduct retroactive security investigations based on a deep history of logs. And you can easily trigger Workflow Automation to remediate attacks and mitigate your exposure in the future. Cloud SIEM Investigator supports AWS CloudTrail logs and Google Cloud Audit Logs. See our Cloud SIEM guides to get started monitoring your AWS and GCP logs for threats, and visit the documentation for more information about Cloud SIEM Investigator. And if you’re not already using Datadog, you can start today with a free 14-day trial.