As your business grows and your services scale in number and complexity, it’s difficult to maintain a rapid pace of innovation while keeping your applications secure. It’s particularly challenging to respond to attacks, as DevOps and security teams need to collaborate to understand each attack’s root cause and remediate the vulnerabilities that enabled it.
Datadog’s APM Security View helps you efficiently detect and mitigate attacks and quickly resolve security incidents to ensure that your applications are reliable, performant, and secure. Powered by Datadog Application Security Management (ASM), APM Security View surfaces security data within the Service Catalog, the Service Page, and Datadog distributed tracing to help you detect attacks against APM-instrumented services and quickly remediate those attacks using code-level insight. And by identifying risks from known vulnerabilities in third-party libraries, APM Security View can help you reduce your exposure to future attacks.
In this post, we’ll show you how APM Security View helps you:
- Identify services exposed to security risks
- Understand those vulnerabilities
- See which services have been exposed to attacks
- Mitigate active threats
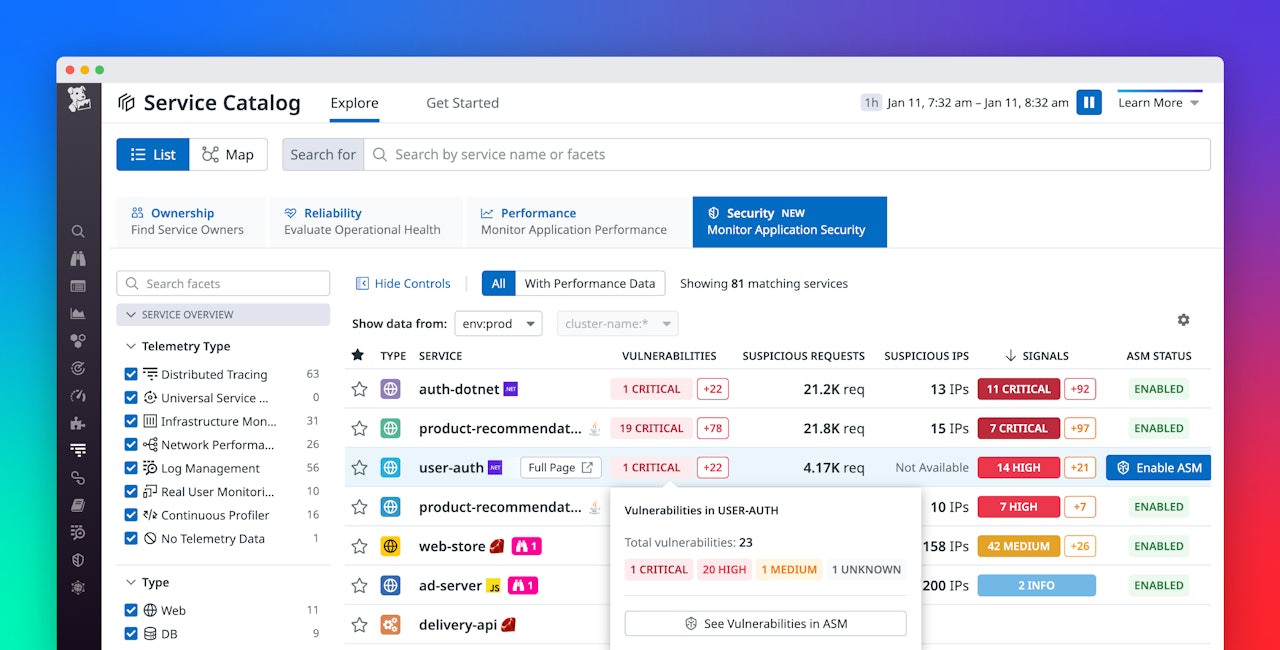
Identify high-risk services in the Service Catalog
The Datadog Service Catalog centralizes knowledge about all your services, giving your teams key information about each service’s dependencies—as well as owner contact information and on-call schedules—that they can use for troubleshooting and incident management. The Service Catalog also includes the APM Security View, which surfaces key security data that can help teams proactively identify vulnerable services and quickly respond to malicious activity.
Spot vulnerabilities that attackers can exploit
Datadog ASM automatically detects vulnerabilities in open source packages—which often comprise the majority of an application’s code—and APM Security View surfaces that information within the Service Catalog and the Service Page. This shows your actual risk exposure by listing vulnerabilities that affect services running in production—as opposed to a stale branch or a development commit—and sorts them by severity to highlight the greatest potential impact.
APM Security View also lets you quickly understand your exposure to attacks, including an overview of suspicious requests and the most common attempted attacks. By combining information about runtime vulnerabilities and exposure to attacks, APM Security View gives teams a full understanding of each service’s security risk so they can prioritize their remediation efforts. And seeing risk information inside the Service Page enables collaboration between incident responders, service owners, and on-call engineers to efficiently respond to attacks, patch vulnerabilities, and minimize risk.
Note that the data APM collects allows it to provide only partial visibility into recent and ongoing attacks. To gain complete visibility into attacks against your services, you can easily enable ASM to monitor all activity. ASM collects all relevant data to provide complete information about every attack, including a description of the attack and actionable remediation steps. Vulnerability details include a link to the relevant entry in the Common Vulnerabilities and Exposures (CVE) database, a list of other services affected, information about the affected library, and remediation steps. ASM is powered by APM libraries, so you can benefit from it right away without deploying another agent.
Track security signals to detect attacks
You can rely on monitors to notify you of an anomaly such as an increased rate of requests to your service, but it’s important to determine whether that traffic is legitimate or is a sign of an attack. Datadog automatically evaluates your application’s activity against security detection rules to differentiate malicious requests from legitimate traffic. If the traffic to your services violates any detection rules—possibly indicating an attack—Datadog generates a security signal and surfaces the details in the Service Catalog.
If an attacker has exploited a vulnerability—for example SSRF or Log4Shell—you’ll see a signal that shows you the type of attack, related logs and signals, and recommended remediation actions. Security signals provide high-quality, actionable information that spotlights an ongoing security issue. While a detected vulnerability indicates that a service could be at risk, a security signal indicates a higher priority concern—an actual attack against the service. You can sort the APM Security View to quickly find services with signals to focus your remediation efforts on exploited vulnerabilities over latent ones. And you can click any signal to pivot to the Service Page, which shows you more information about the service’s risks alongside its complete performance and reliability data.
The severity of a security signal conveys the level of risk to the service, and APM Security View helps responders see which signals are critical. Responders can quickly initiate and coordinate their remediation efforts using the service information provided in the Service Catalog, including documentation and details of the underlying infrastructure. For deeper insight into the issue, users can pivot to ASM to see which libraries are vulnerable and which other services may be affected.
Trace the attack and remediate the vulnerability
To fully understand an attack, you need to see how it propagates through your services. Datadog distributed tracing provides powerful visualization and analysis tools to help responders identify the context and scope of an attack.
By showing you all the endpoints in the path of the attack, an APM flame graph illustrates its impact. If the flame graph shows that the attack targeted a critical component of your application—for example, a data store that holds inventory or user account information—responders can quickly grasp the potential impact of the attack and reach out to collaborate with the relevant teams.
If the flame graph indicates that an attack is a threat to your application’s security or your business operation, you can leverage ASM’s code-level visibility to quickly pinpoint the code that you need to fix to remediate the issue. ASM incorporates our source code integration to show you the function in which the vulnerability was triggered, so developers quickly know where to focus their remediation effort.
Get a deeper view into your services’ security
APM Security View surfaces insights from ASM to help you understand your high-risk services. If you’re an APM customer, you can start using ASM to gain complete visibility into your security signals and understand the full scope of the threats against your services. ASM utilizes the same APM libraries that you’ve already deployed, so you can start using it right away. See our documentation and demo video for more information about how you can use ASM to quickly remediate exposed vulnerabilities and reduce your mean time to resolution (MTTR).
If you’re not yet using Datadog, you can start today with a 14-day free trial.