With the growing complexity and velocity of security threats in dynamic, cloud-native environments, it’s more important than ever for security teams to have the same visibility into their infrastructure, network, and applications that developers and operations do. Conversely, as developers and operations become responsible for securing their services, they need their monitoring platform to help surface possible threats.
We are excited to announce the addition of Cloud SIEM to Datadog. You can now detect threats in real time and investigate security alerts across your infrastructure metrics, distributed traces, and logs. Now, your full engineering organization—including development, operations, and security—has comprehensive visibility across all layers of your environment using a single unified platform.
Comprehensive security visibility from observability data
Datadog’s more than 850 integrations let you collect metrics, logs, and traces from your entire stack as well as from your security tools, giving you end-to-end visibility into your environment. This lets you cast a wider net to catch possible security issues, and provides deeper context during your investigations. For example, if you detect abnormally high CPU utilization on a host, you can pinpoint which container or process is causing it to determine if you’re dealing with a crypto-miner.
Turn-key security integrations
Datadog’s integrations give you security visibility and detection capabilities into every layer of your environment. Integrations automatically collect, parse, and enrich your data, and they provide out-of-the-box content such as built-in dashboards and detection rules.
New security integrations provide additional contextual information to accelerate investigations, such as user authentication history from Okta or Google Workspace and network logs from integrations like Meraki. Datadog Cloud SIEM also ingests third-party alerts. This means you have immediate access to information such as vulnerabilities detected by Twistlock, runtime anomalies identified by Lacework and Alcide.io, or web application attacks blocked by Signal Sciences.
For example, alert on critical AWS CloudTrail actions, such as disabling security logging, which an attacker might take to cover their tracks. Then, correlate those events with AWS GuardDuty anomalies indicating potential data exfiltration, and confirm the user’s recent activity with their Google Workspace authentication history.
Enriching your events with security context
Datadog’s log processing pipelines automatically parse out key standard attributes from your ingested logs and events, unifying your logs across teams and data sources. This makes it easy to search and filter log data across your entire infrastructure for threat detection and investigation.
Log processing pipelines also enrich ingested logs and events with dynamic context that improves threat detection accuracy. For example, the geoip processor identifies the country and city of an IP, allowing you to detect anomalies in authentication patterns. The lookup processor lets you enrich events with your own business data to answer questions such as: have we denylisted this IP? Does this MAC address belong to a stolen laptop? Is this user an administrator?
Real-time threat detection
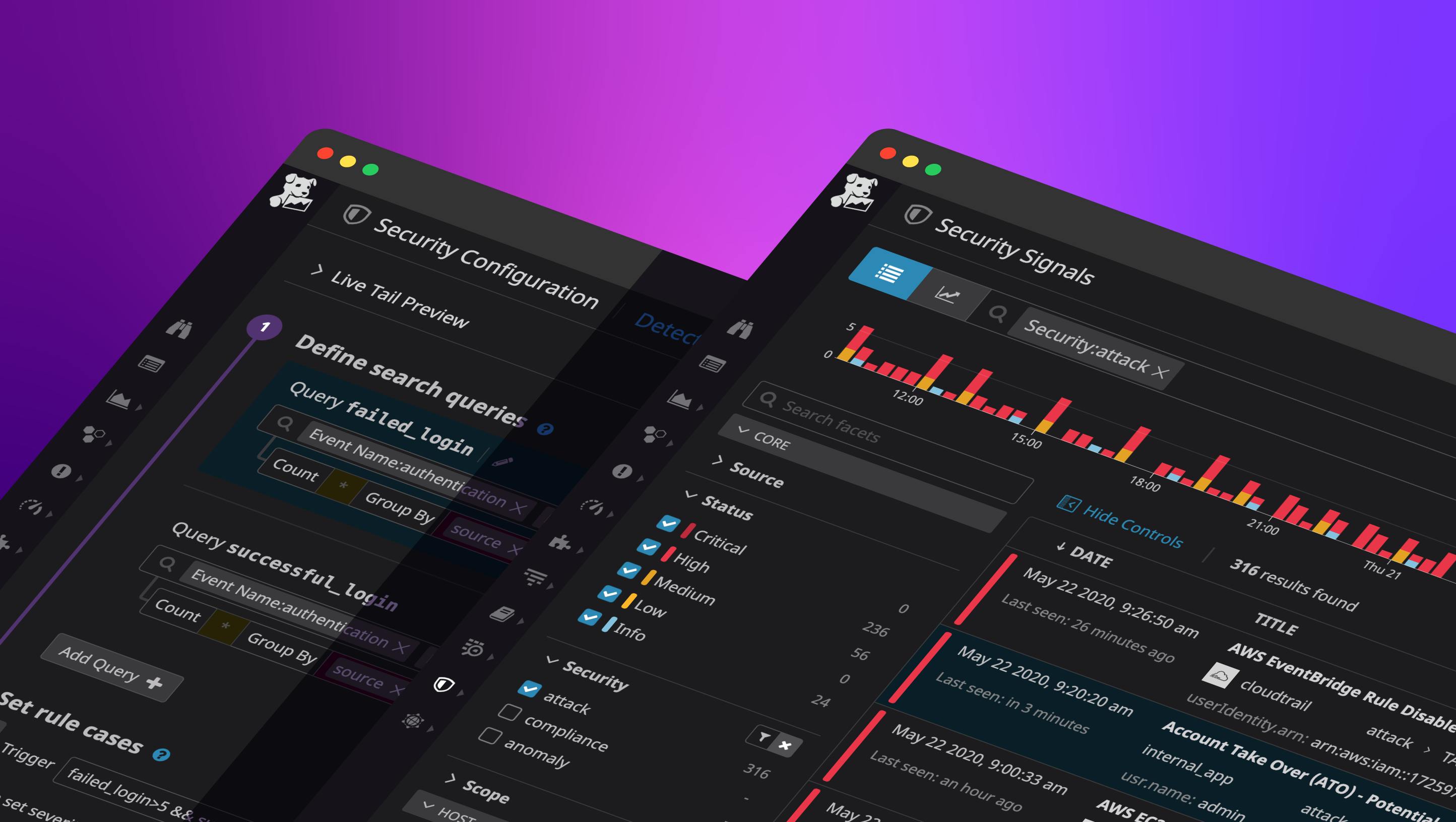
Datadog’s new Detection Rules give you a powerful way to detect security threats and suspicious behavior within all ingested logs, in real time. With Detection Rules, you define conditional logic that Datadog applies to your entire event stream. If a rule is matched, Datadog evaluates the severity and whether anyone should be notified.
Additionally, rules trigger as soon as their conditions are met, including when logs and events are received late or out-of-order, for example due to network issues.
Datadog provides out-of-the-box rules for widespread attacker techniques, mapped to the MITRE ATT&CK framework. These default rules mean you can get started monitoring for threats in minutes, without any configuration. Datadog continuously adds new rules for more integrations and classes of attacks.
Simple and flexible rule creation
You can edit and fine-tune any rule, including out-of-the-box ones, to meet your organization’s specific needs. Our simple and flexible editor enables you to write real-time threat detection rules without needing to learn a proprietary query language.
In the above example, you detect a potential account takeover by monitoring spikes in login failures for every individual user over a five-minute sliding window. If a spike is detected, the rule includes logic dictating whether to generate an informational signal or high-severity alert depending on whether a successful login also occurs within the same time window, possibly indicating an account takeover.
Threat detection “Without Limits”
Detection Rules take full advantage of Datadog’s Logging without Limits™, which lets you customize what logs you want to index while still ingesting, processing, and archiving everything. Rules apply to the full stream of ingested, parsed, and enriched logs so that you can maximize detection coverage without any of the traditionally associated performance or cost concerns of indexing all of your log data.
Since all logs are sent to your own archives, you can use Datadog’s Log Rehydration™ to re-index relevant logs if you need to perform a security audit down the road.
Correlate and triage security signals
If Datadog detects a threat based on any rules, it creates a security signal. You can view all security signals in a unified explorer, making it easy to search, filter, and correlate them without needing to learn a dedicated query language.
You can use the Security Signals explorer to quickly triage possible threats and immediately begin investigating potential misconfigurations or attacks. Select a signal to review the deeper context, such as the timeline of the attack, or the attributes of events that triggered that signal. You can also easily pivot to the underlying observability data (e.g., related events, metrics, and processes) to quickly triage signals.
Signals are tied to entities such as the actor conducting the attack (e.g., username, IP) or their targets (e.g., hostname, application) so you can easily correlate signals across your infrastructure, applications, and security products to retrace an entire attack.
Collaborative investigations
With Datadog’s collaboration integrations—including Slack, PagerDuty, and others—your high-severity rules automatically notify the right people. You can also share signals directly from the explorer into your incident response tool, for example to create a JIRA ticket or a ServiceNow incident.
Add security visibility to your monitoring
Datadog’s Cloud SIEM brings greater security visibility to all teams across your organization, including development, operations, and security. If you already use Datadog, you can get started with real-time threat detection. Otherwise, sign up for a 14-day free trial.