Vera Chan

Jason Hunsberger

David Pointeau

Zach Anderson
Akamai is a cloud content delivery and security platform that helps organizations secure their applications, APIs, network access, and credentials that workforces and customers use every day. Akamai Zero Trust provides enhanced security for users, devices, and data across an organization by securing access to the corporate network, SaaS applications, email, and other resources. Akamai Application Security is a suite of security solutions designed to protect web applications from a wide range of threats, including DDoS attacks, bot traffic, and vulnerabilities in application code.
As a part of our continued partnership with Akamai, we’re excited to announce new integrations with Akamai Zero Trust and Akamai Application Security. Integrating Datadog Cloud SIEM with Akamai’s Zero Trust and Application Security solutions helps increase overall security posture, reduce risk, and increase the operational efficiency and effectiveness of security operations teams.
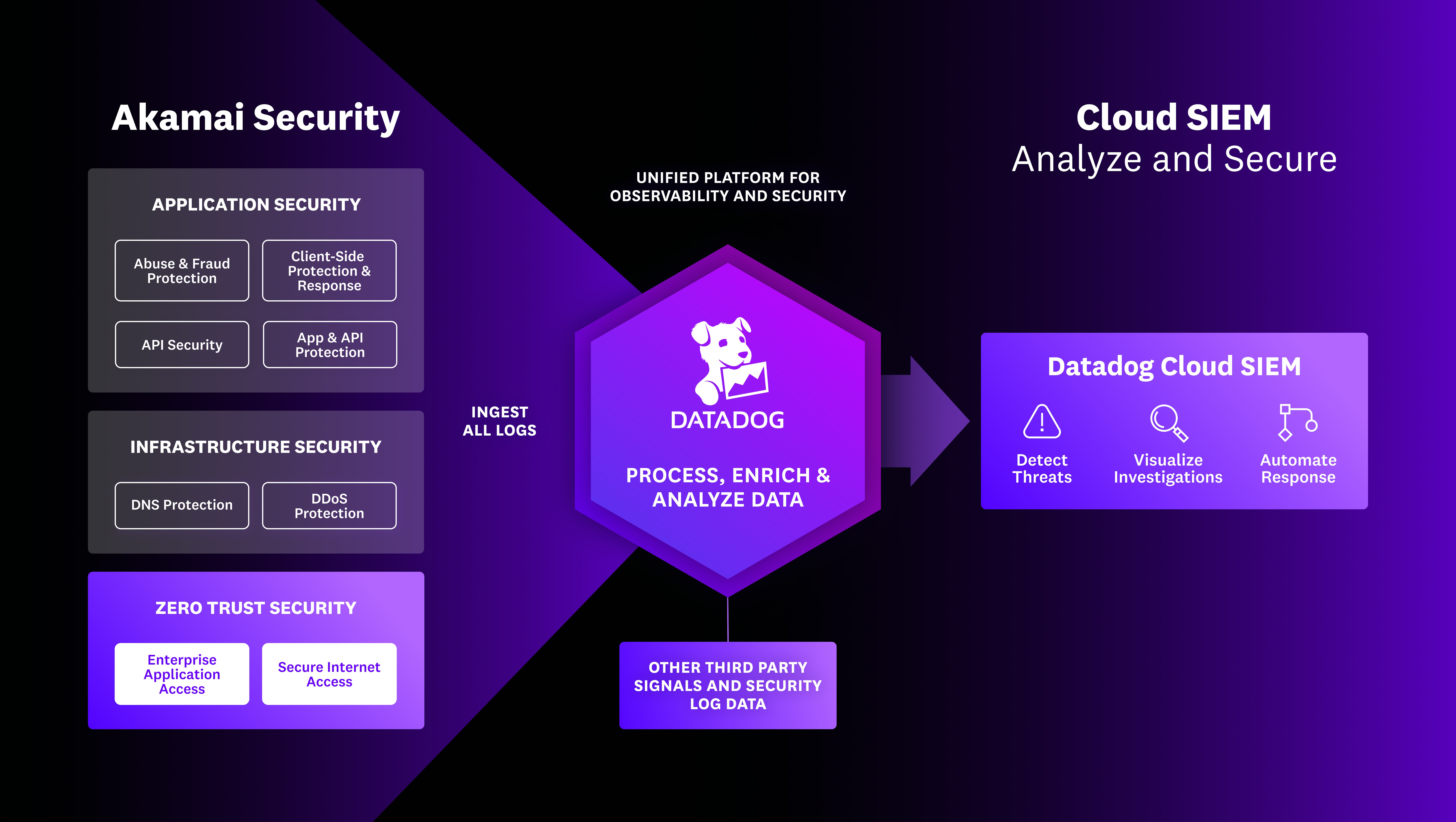
With Datadog Cloud SIEM’s intuitive query language and customizable threat detection rules, security teams can identify suspicious activity in Akamai Application Security and Zero Trust logs and correlate that activity with other observability context. In addition, out-of-the-box and custom dashboards can help assist with security monitoring, triage, and remediation. These integrations give security teams access to a unified solution that aligns network and security intelligence, enabling the effective mitigation of intricate risks associated with modern apps and cloud computing.
In this post, we’ll discuss how the Akamai Zero Trust and Application Security integrations enable you to:
- Control and protect your Akamai Security logs
- Build custom detection rules for log analysis and correlation
- Create dashboards for a shared view into your security posture and signal trends
- Customize your response workflows with Datadog Workflow Automation and Datadog Case Management
Control and protect your Akamai Security logs
To take advantage of this deepened integration, simply locate, install, and enable the Akamai Zero Trust integration or Akamai Application Security integration.
Datadog’s out-of-the-box log processing pipeline will automatically parse and normalize your Akamai Zero Trust logs. Standardizing the format of these logs helps structure them for easier analysis and correlation with your logs from other sources, so that Cloud SIEM can surface signs of related suspicious activity across all of your logs.
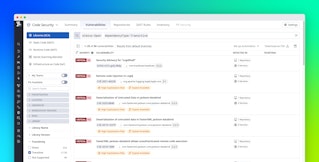
Datadog’s Akamai Zero Trust and Application Security integrations allow you to capture, retain, and deliver logs containing security information and events from Akamai to Datadog Cloud SIEM in near real time. If you use Akamai Zero Trust EAA (Enterprise Application Access) or Akamai App & API Protector, Kona Site Defender, Client Reputation, Web Application Protector, Bot Manager, or Account Protector, you can analyze security events generated on the Akamai platform alongside security events from other sources within Datadog. This centralizes your security signals across Akamai and from any of our 1,000+ integrations.
You can control and protect the data feed with event filtering, which lets you filter the security events you collect in Datadog Cloud SIEM by security configuration and security policy. Cloud SIEM also supports data retention, storing security event data for 12 hours so you can go back and capture missed events.
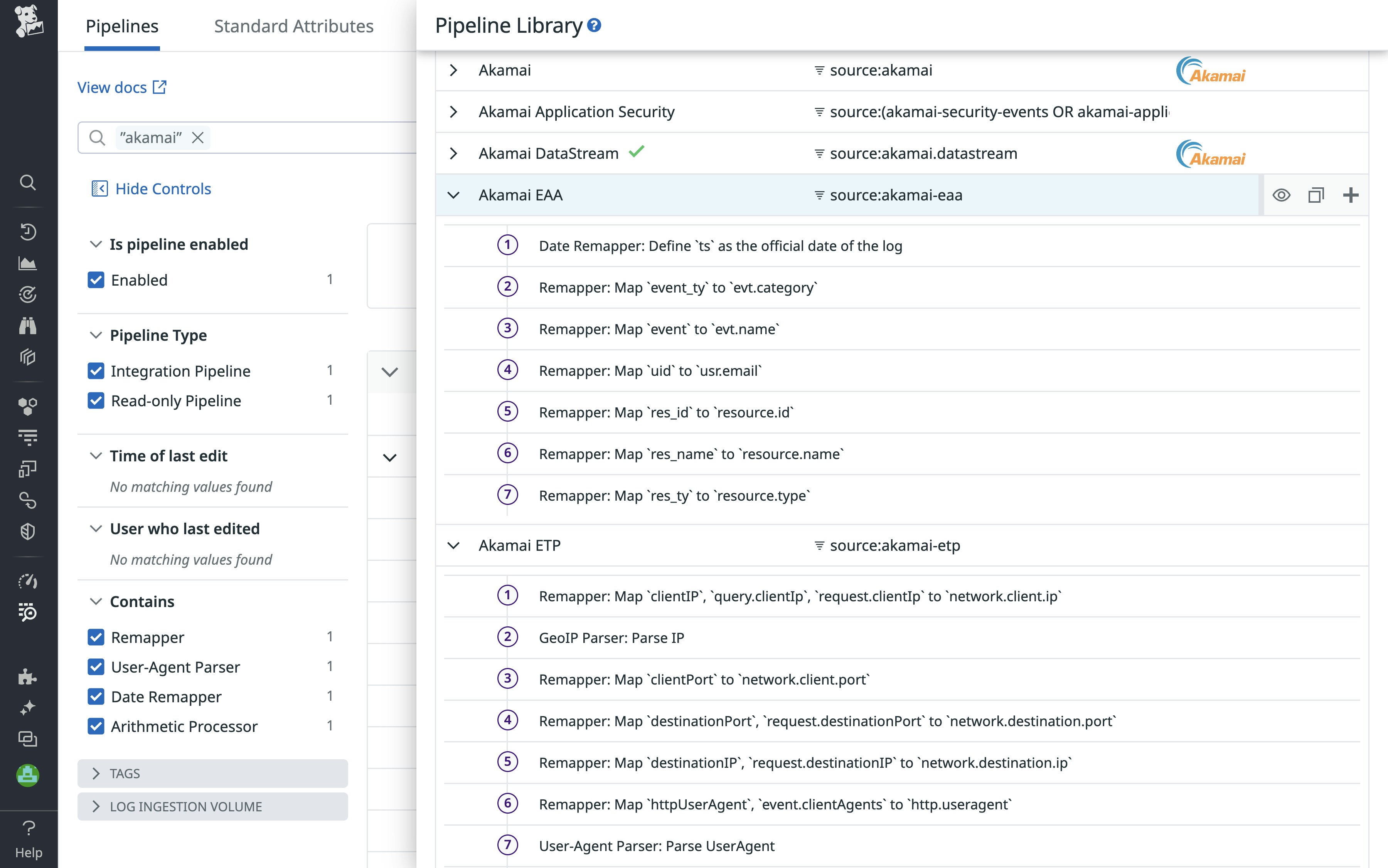
Build custom detection rules for log analysis and correlation
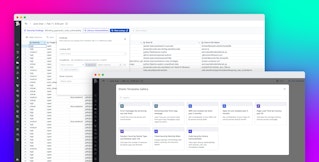
Datadog Cloud SIEM provides several capabilities that help you analyze your Akamai logs and correlate them with detection rules, so you can understand what’s happening in your environment and catch attacker behavior more quickly. Custom rules can also be easily created by copying and editing existing rules.
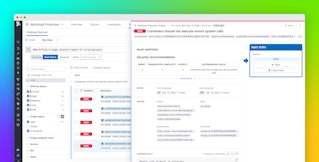
With Cloud SIEM, you can bring in your third-party alerts along with alerts generated by Akamai. For instance, if you have a bot protection alert in Akamai, the out-of-the-box Cloud SIEM detection rule shown below will generate a signal that will alert you to respond. Third-party alerts can be displayed within Cloud SIEM and combined with your Akamai alerts.
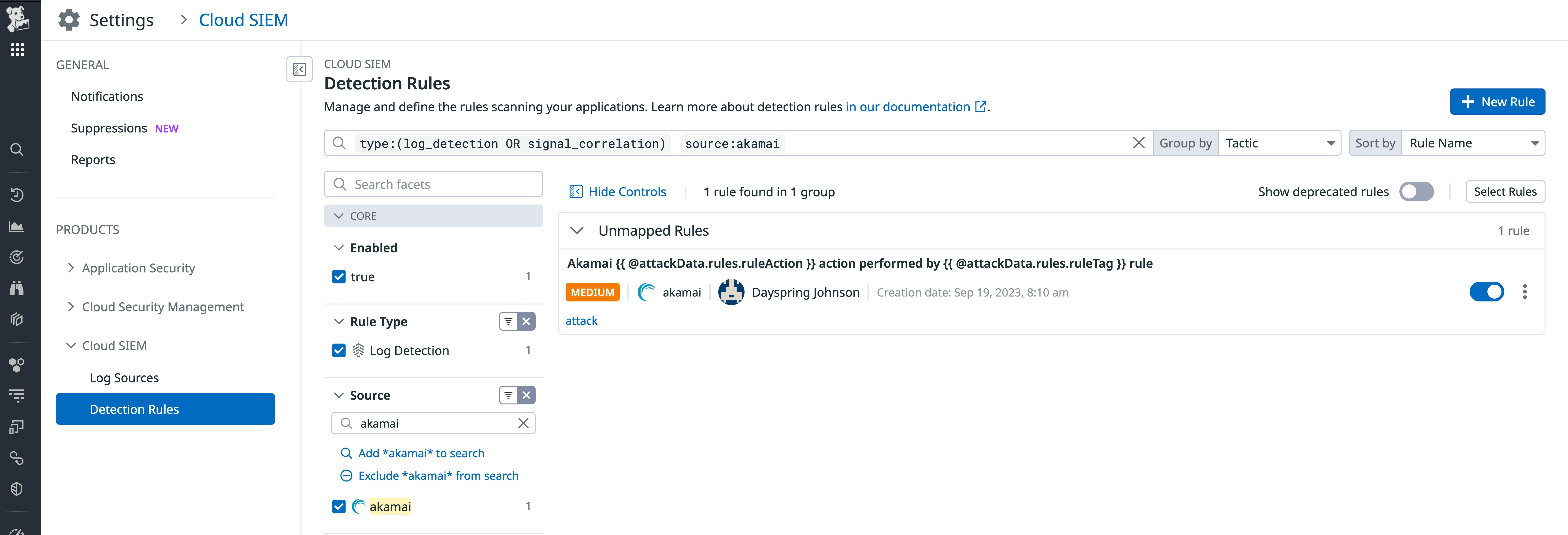
Create dashboards for a shared view into your security posture and signal trends
The Akamai Application Security out-of-the-box dashboard provides comprehensive insights into attack data, security events, and threat intelligence, enabling teams to monitor and respond to threats effectively. Use this dashboard to monitor your Akamai security events from Kona Site Defender and Bot Manager, tracking IP log activity and rare IP occurrences for enhanced visibility and proactive defense against potential security breaches.
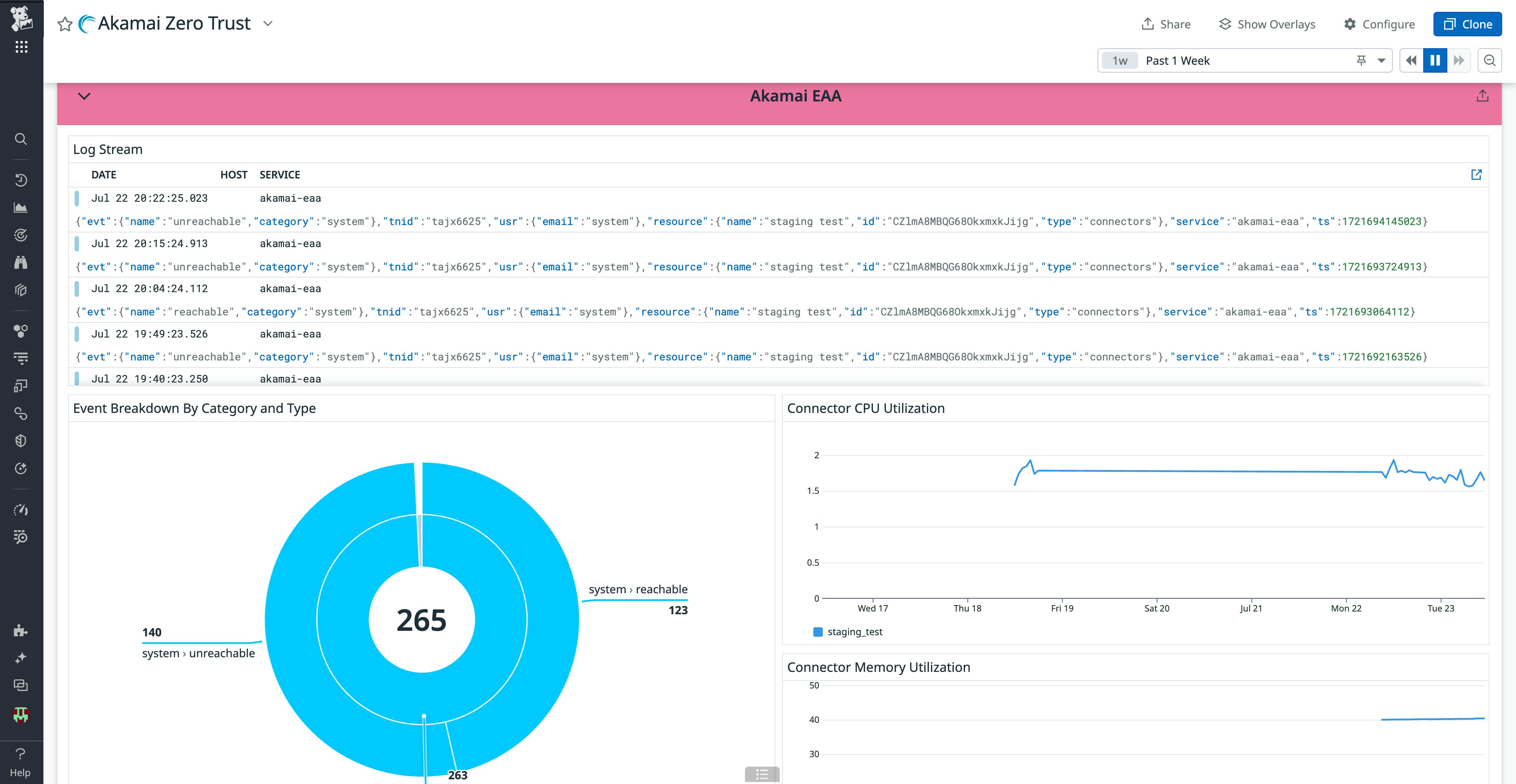
You can easily build and customize your own dashboard for Akamai Zero Trust with Cloud SIEM. Custom dashboards provide security teams with an at-a-glance, real-time view of Akamai-related security signals that may indicate threats targeting specific parts of your environment.
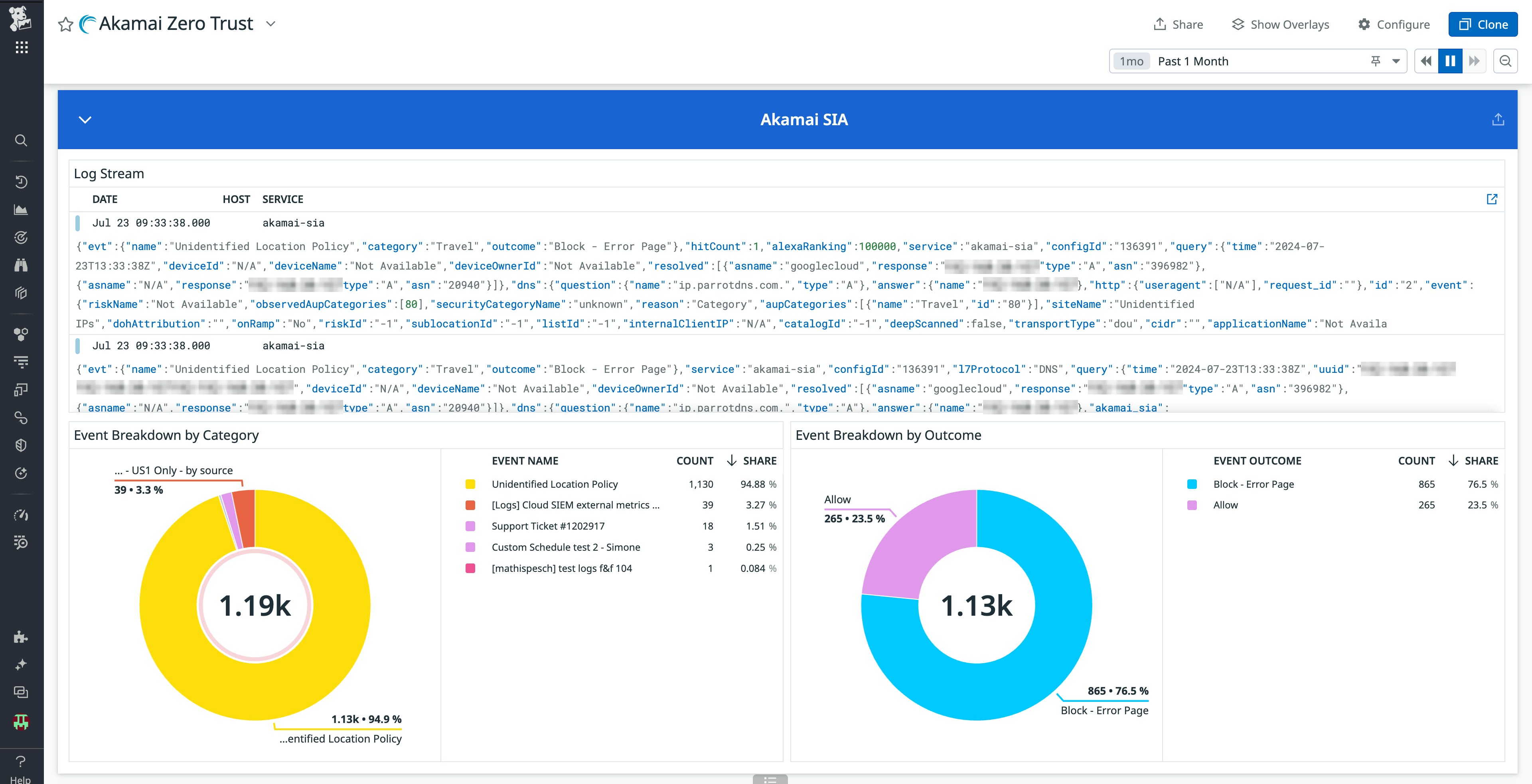
This customization allows teams to focus on the most relevant data, ensuring efficient monitoring and rapid response to threats. These dashboards integrate seamlessly with existing workflows, providing contextual insights that enhance decision-making and collaboration across teams.
Customize your response workflows with Workflow Automation and Case Management
You can also use Datadog Workflow Automation to orchestrate common response actions and automate processes on demand or in response to monitors or security signals. Customize your own workflows with a visual workflow builder and send chat messages and sync updates to tools such as Slack and Microsoft Teams. For instance, you can use a Slack approval workflow to triage signals from Akamai more efficiently.
Additionally, workflows integrate with Datadog Case Management, which brings security and DevOps teams together to rapidly investigate application issues using the same platform and the same data for complete visibility. Cross-functional teams can collaborate more effectively on security signals and threat investigations in workspaces to investigate and resolve issues quickly on Datadog’s unified platform for observability and security. You can use this feature to add a step to your workflow that creates a case in Datadog, so that while you’re taking steps to remediate the issue, you can triage and troubleshoot further.
Deeper insights into your Akamai Zero Trust and Application Security logs
Datadog’s Akamai Application Security and Akamai Zero Trust integrations provide you with more visibility to detect and secure your environment against threats. If you’re already a Datadog customer, you can learn more about our Akamai Zero Trust and Akamai Application Security integrations now in our documentation library. Or, you can get started today with a 14-day free trial.